Protecting sensitive government data is critical for the Department of Defense (DoD), thus making it critical, too, for its contractors across the Defense Industrial Base (DIB).
As more of the DIB adopts Microsoft 365 (M365) as a mission-critical collaboration solution to carry out mission-critical activities, the DOD continues to mature its data security guardrails in the Cybersecurity Maturity Model Certifications (CMMC), specifically designed to protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
Simplified Implementation of CMMC in Microsoft 365: Separating Data, Not Users
Effective implementation of CMMC in Microsoft 365 requires a balance between security and collaboration. To accomplish this balance, some organizations elect to create separate enclaves, taking a multi-tenant strategy to segregate users and data at the tenant level, ensuring zero chance of cross-pollination of data. While this strategy may work for some organizations, it can create unnecessary barriers to collaboration and add complexity to security postures. Alternatively, a single-tenant strategy that separates data without separating users can simplify compliance efforts and reduce the risk of errors.
To achieve this, AvePoint has partnered with leading DIB organizations to leverage Microsoft Teams and SharePoint Sites, to share, store, and communicate about sensitive data with automated controls protecting sharing and user management. By applying access controls and data security measures directly to the workspaces (SharePoint site collection, document library, Teams channel, etc), we enabled important governance control over their data without the management burden or segregated user experience of a multi-tenant approach.
Watch our webinar on-demand:
To accomplish this, the customer utilized AvePoint’s MyHub for Microsoft 365 to implement a self-service catalog enabling end-users to request a SharePoint Site or Team. Through this process, they captured information regarding the expected use of sensitive data within the workspace, such as if they expect personnel data, FCI, or International Traffic and Arms Regulation (ITAR) data. With this information, AvePoint solutions can automatically implement security and sharing restrictions to protect sensitive government data from being shared outside the controlled workspace.
Through this process, metadata and labels can be automatically set, enabling Data Loss Protection policies; SharePoint sharing settings can be turned off; and a conditional approval process can be added. This last piece allowed the customer to implement an exceptions process: in the case that a foreign national has the need to know and security approval to view ITAR data, they can be added with a simple workflow, requesting approvals from the appropriate parties.
This approach not only reduces the risk of accidental exposure of CUI but also simplifies compliance efforts by automating data classification and access controls. By separating data at the workspace level instead of creating a second tenant, organizations can maintain a unified environment for collaboration while still meeting CMMC compliance requirements. This approach allows users and admins to focus on their work without having to worry about where data belongs in the environment.
Looking for expert advice to meet CMMC compliance standards in Microsoft 365? Register for our upcoming Summit to get started.
Get Started: 4 Steps to Build a Single-Tenant Strategy for CMMC Compliance
Deploying a single-tenant strategy to meet CMMC standards in Microsoft 365 can feel daunting – and for some organizations, a multi-tenant enclave may make more sense. However, if you follow these best practices and implement proper controls, securing your sensitive data will be easier and provide a better user experience for your organization.
Here’s how to get started:
1. Create separate workspaces for sensitive data
The first step to building a single-tenant strategy for CMMC compliance is to create separate workspaces for sensitive data, enabling you to control access to only authorized personnel. This not only means architecting purposeful spaces for collaboration and storage of sensitive data in separate workspaces, but also providing a means for requesters of new Teams and SharePoint sites to tell you how they will be used, by whom, and what type of data they plan to use.
This can be done in a custom first-party solution like a Form or Power App, or a third-party COTS tool such as AvePoint MyHub. This information, gathered at provisioning and refreshed during any lifecycle actions, should be stored in the workspace and guide the security and access policies necessary to contain sensitive information.
2. Implement access controls
Once you know which workspaces store sensitive information, you must apply the proper controls to ensure only those who need access have access. With AvePoint Cloud Governance, you can programmatically apply sensitivity labels by workspace and automatically enforce appropriate permissions control. With the solution, you can also set membership restrictions, forcing new members to go through a predefined approval process before accessing your workspaces, confirming things like “need to know” and “right to know” through management and cybersecurity teams. This makes it easy to ensure that only approved members have access to your sensitive data.

Don’t forget to turn off sharing controls! SharePoint, Teams, and even the desktop Office applications have a number of ways to share your data, so for workspaces containing your most sensitive data, don’t forget to build policies to modify which of those controls work and with whom that information can be shared.
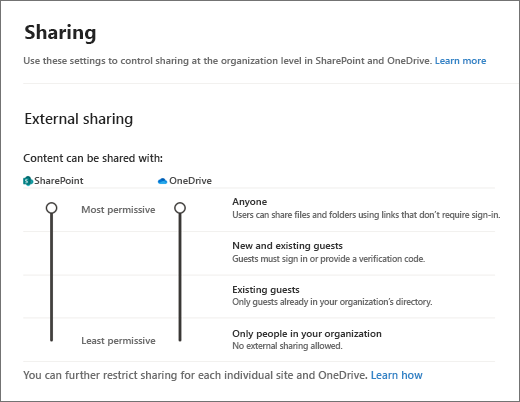
3. Manage the exceptions
Native rules within Microsoft are effective, but pretty black and white, making it challenging to handle exceptions to the policies you set. For example, under ITAR regulations, foreign persons should not have access to export control data; however, some foreign individuals work for the government and require this access to do their jobs.
Solutions like Cloud Governance can help by creating conditional access rules and approval policies to support them. For example, you can set up a multi-stage approval process to capture when foreign individuals are trying to access confidential data workspaces and give your security teams a means to approve it without manual IT intervention. This approach adds flexibility to your policies without compromising security, allowing you to handle any exceptions to the rules.

4. Leverage delegated administration
Delegated administration is an effective strategy to achieve the benefits of a multi-tenant compliance approach without the downsides. Sometimes called a “virtual tenant,” delegated administration allows you to grant specific privileges to trusted resources by workspace, user group, or action, without over-privileging them.
Instead of giving full admin rights to an entire service across a tenant, like SharePoint Online, you can break down permissions even for service administrators by allowing only a set of permissions to do specific tasks in the service admin center.
AvePoint EnPower makes it easy to control who has access to sensitive data providing an abstraction layer combining Role Based Access Controls with a scope of content, ensuring that only authorized personnel can make changes to any given workspace or service. With delegated administration, you can achieve fine-grained control over permissions and enable secure collaboration within your organization.
Build Your Proactive CMMC Strategy with AvePoint
To achieve CMMC compliance in collaboration tools like M365, organizations can follow four steps to deploy a single-tenant strategy and implement other security best practices. Using solutions like AvePoint Cloud Governance can automate the compliance process, making it easier to maintain compliance over time. Implementing suitable strategies and solutions not only simplifies compliance but also enhances defenses and enables organizations to leverage the latest collaboration tools and features offered by Microsoft.
As security and compliance specialists, AvePoint can help organizations meet their regulatory and compliance requirements. With a focus on the public sector, AvePoint understands the unique challenges faced by government agencies and contractors in meeting strict compliance mandates like CMMC.
Through a combination of industry-leading solutions and deep knowledge of regulatory requirements, AvePoint can help organizations navigate the complexities of compliance, ensuring that their sensitive data is protected at all times. From secure data management to governance and risk management, AvePoint has the expertise and solutions needed to enable organizations to meet their compliance requirements with confidence.
Ready to get started? Join the upcoming Microsoft, Summit 7, and AvePoint Summit to gain valuable strategies and best practices for meeting CMMC requirements to better protect US Federal data, contract data, and US person’s data in Microsoft 365.







