Need help navigating federal records management? Download our NARA Compliance Resource Kit!
In January, the Office of the Under Secretary of Defense for Acquisition and Sustainment (OUSD(A&S)) released the Cybersecurity Maturity Model Certification (CMMC) framework. This framework was developed in concert with DoD stakeholders, University Affiliated Research Centers (UARCs), Federally Funded Research and Development Centers (FFRDCs), and the DIB sector with the goal of providing a certification path to demonstrate compliance with information handling and safeguarding requirements when doing business with the DoD.
When working with the DoD, organizations find themselves having to comply with a variety of federal regulations. CMMC “encompasses the basic safeguarding requirements for FCI (federal contract information) specified in Federal Acquisition Regulation (FAR) Clause 52.204-21 and the security requirements for CUI (controlled unclassified information) specified in National Institute of Standards and Technology (NIST) Special Publication (SP) 800-171 per Defense Federal Acquisition Regulation Supplement (DFARS) Clause 252.2047012 [3, 4, 5].”
While the certification process and requirements for becoming a CMMC Third Party Assessment Organization (C3PAO) has not been finalized, a CMMC Accreditation Body has been formed to determine these requirements. This body will determine the requirements for C3PAOs and intends to set up a “marketplace” for organizations in need of CMMC certification to look for help achieving it. However, it remains true that there are no accredited C3PAOs, and anyone advertising certification, training, or accredited services related to CMMC certification are to be considered suspect, at best.
SEE ALSO: AvePoint’s FedRAMP Authorization Expands to 6 More Solutions
Most organizations are familiar with the FAR, DFARS, and NIST security requirements. These are technical controls put in place in the IT infrastructure to protect sensitive data. The CMMC incorporates those practices (organized into 17 domains) and adds the concept of a maturity model to the actual practice of these requirements and the processes of evaluating them. As the CMMC documentation explains:
“In general, a maturity model is a set of characteristics, attributes, indicators, or patterns that represent capability and progression in a particular discipline. The content of such a model typically exemplifies best practices and may incorporate standards or other codes of practice of that discipline. A maturity model thus provides a benchmark against which an organization can evaluate the current level of capability of its processes, practices, and methods and set goals and priorities for improvement. To measure progression, maturity models typically have levels along a scale [9,10].”

That’s the best way to think of CMMC: a benchmark to evaluate current security protocols and practices, review them, and institutionalize the proper practice of securing information.
The CMMC breaks down into 5 levels, with each level including distinct practices or processes that are drawn directly from the FAR, DFARS, and NIST basic data handling requirements. However, additional controls are not the goal of the higher levels of CMMC. The model is intended to measure the maturity and institutionalization of the security practices involved.
How do you measure maturity? Again, quoting from the CMMC document: “The CMMC model measures cybersecurity maturity with five levels. Each of these levels, in turn, consists of a set of processes and practices which are characterized in Figure 2. The processes range from ‘Performed’ at Level 1 to ‘Optimizing’ at Level 5 and the practices range from ‘Basic Cyber Hygiene’ at Level 1 to ‘Advanced/Progressive’ at Level 5.”
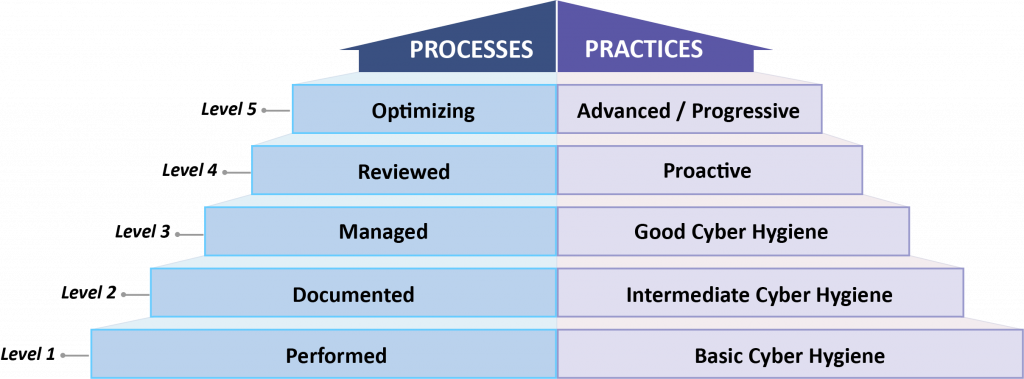
CMMC Levels are cumulative; your organization must demonstrate that it meets all the requirements of all lower levels to be certified at any given level. It’s not enough to show that the practices at each level have been implemented. Organizations must also show that they have institutionalized the processes for each level, and all levels listed below. If for any reason the organization meets different achievements for process institutionalization and practice implementation, the organization will be certified at the lower level.
Each CMMC level increases the number of practices and increases the level of process institutionalization required for certification. Below, I’ve listed each level and a short description of the process institutionalization and practice implementation required. (Note: Practices are direct quotes from the CMMC document.)
Level 1
Processes: Performed
Level one is for those cases where an organization may have minimal FCI or CUI and may not have processes that can be institutionalized or are only used in an ad hoc manner. Maturity is not assessed at level 1.
Practices: Basic Cyber Hygiene
“Level 1 focuses on the protection of FCI and consists only of practices that correspond to the basic safeguarding requirements specified in 48 CFR 52.204-21 (“Basic Safeguarding of Covered Contractor Information Systems”) [3].“

Level 2
Processes: Documented
Level 2 is the first assessment of maturity. At this level, all security practices are documented at a minimum.
Practices: Intermediate Cyber Hygiene
“Level 2 serves as a progression from Level 1 to Level 3 and consists of a subset of the security requirements specified in NIST SP 800-171 [4] as well as practices from other standards and references. Because this level represents a transitional stage, a subset of the practices reference the protection of CUI.“
Level 3
Processes: Managed
At level 3, an organization should begin to manage their security practices. Beyond simply documenting the practices in use, this requires things like written policies, remediation plans, and more intensive analysis of risk. This is the CMMC Level the majority of organizations doing business with the DoD will need to be certified for, as this is the level at which CUI begins to be considered (though CUI may not be handled by the organization).
Practices: Good Cyber Hygiene
“Level 3 focuses on the protection of CUI and encompasses all of the security requirements specified in NIST SP 800-171 [4] as well as additional practices from other standards and references to mitigate threats. It’s noted that DFARS clause 252.204-7012 (“Safeguarding of Covered Defense Information and Cyber Incident Reporting”) [5] specifies additional requirements beyond the NIST SP 800-171 security requirements such as incident reporting.“

Level 4
Processes: Reviewed
Creating overall policies and documenting practices is only useful when the policies and practices are reviewed regularly. Level 4 adds regular review requirements to the entire information security “stack” – review processes, policies, practices, and capabilities.
Practices: Proactive
“Level 4 focuses on the protection of CUI from APTs and encompasses a subset of the enhanced security requirements from Draft NIST SP 800-171B [6] as well as other cybersecurity best practices. These practices enhance the detection and response capabilities of an organization to address and adapt to the changing tactics, techniques, and procedures (TTPs) used by APTs (advanced persistent threats).”
Level 5
Processes: Optimizing
At level 5, an organization should demonstrate a maturity that allows them to begin optimizing their security practices, processes, policies, and capabilities. Organizations at level 5 would be regularly reviewing and analyzing their security posture to combat advanced and prospective risks.
Practices: Advanced/Proactive
“Level 5 focuses on the protection of CUI from APTs. The additional practices increase the depth and sophistication of cybersecurity capabilities.”
The CMMC that has been developed is a very comprehensive and desperately needed update to the way organizations think about information security. It’s great, and will make it far easier to ensure organizations meet the security requirements for working with the DoD.
For more information, please see the following references:
- Office of the Under Secretary of Defense for Acquisition & Sustainment Cybersecurity Maturity Model Certification website
- CMMC FAQ
- CMMC Model v1.02 document
- CMMC Appendices
- Public Briefing Slides

