For a SharePoint administrator, risk typically comes from a collision of two forces: a lack of control over permissions policies and improper storage of sensitive content. Often times, an admin’s approach to SharePoint has been one of an absentee landlord: “I have provided you a space – what you do in it is up to you.” However, when an audit or breach occurs, the IT department ends up owning much of the responsibility for what is in SharePoint and what is done with it. It is up to the technical staff to provide incident reports and proof of ownership.
What if responding to an incident or an audit was as simple as granting access to the systems already in use on a daily basis? These events would no longer become fire drills with expensive reallocation of resources and lost time on other projects, but instead an integral part of the system and processes already in place. Moving from afterthought to forethought is as simple as a shift in mindset from landlord to steward.
The Insider Threat
Least access is an important concept that IT professionals have learned and understand intuitively. On the other hand, a business user’s goal is removing any barrier to controlling their content, and understandably so. When they see “Full Control” as an option when granting permissions, it may be the most sensible option to them if they do not want their users to have any issues collaborating in SharePoint. They may not realize that those with full control can, among other things: remove anyone’s permissions from the site including their own, delete subsites (and lists/libraries), and completely change the look and feel of the site. Plus, these permissions might get inherited into other unintended areas as well. From the perspective of an IT professional, actions including these can be seen as threat to the integrity of the environment even if they are non-malicious. Grouped together, they are often called the “Insider Threat.”
According to the 2015 Vormetric Insider Threat Report, 92 percent of healthcare IT admins fear insider threats. To compound the problem, the survey results confirmed the statement with 54 percent of respondents reporting compliance requirements and regulations are the top reason for protecting sensitive data. Threats to data and vulnerabilities from newly developed attack methods can easily outpace the slow-growing compliance requirement. In other words, adhering to compliance requirements is not enough for sensitive data protection. The culture of stewardship is needed to drive protection.
Assessment Questions for SharePoint Admins
As we know, over time, SharePoint trends towards chaos without proper oversight, governance, and enforcement. Luckily, the reasons for the chaos are so common that they can be easily anticipated. Some questions a SharePoint admin should be able to answer at any time include:
- Is my content being accessed by the right people?
- Is my permission structure still intact? Are my policies being violated?
- Is there sensitive information in my environment? How can I tell? Where does it live?
If you cannot retrieve any of this information with minimal effort, it could be cause for concern. Becoming an active steward of your SharePoint environment means having processes in place as part of daily SharePoint life that addresses these questions.
Privacy Impact Assessments and Beyond
A long time ago, before SharePoint was installed, you may have helped your organization’s privacy officer fill out an assessment of the privacy and security capabilities of SharePoint. The goal was to understand the risk that SharePoint was adding to the enterprise based on its out-of-the-box capabilities. At the time, conducting privacy impact assessments (PIAs) was likely a manual back-and-forth process – perhaps a spreadsheet being sent over email. To automate this process, the AvePoint Privacy Impact Assessment (APIA) solution is available now as a free download from the International Association of Privacy Professionals (IAPP). Privacy officers can utilize APIA’s browser-based interface to manage questions, response workflows, and reoccurring assessments with a secure and automated tool.
While PIAs are a critical part of assessing a SharePoint environment, additional insights an admin needs to understand the risk inherent in his or her SharePoint deployment include:
- Risk profile of the location and severity of sensitive content in the environments
- Permissions profile of who has access to what, what they are capable of doing, and what they have been doing with the content and configurations
A well-structured, regularly-scheduled portfolio of reports can help change any SharePoint admin from absentee landlord to steward.
Risk Profile and Security Search
AvePoint Compliance Guardian – AvePoint’s data loss prevention (DLP) and governance, risk, and compliance (GRC) management platform – can easily generate a Risk Profile report of content in the environment. This report is built from scans of the content itself based on external compliance regulations and any other indicators of sensitive information unique to the organization. A risk score can be generated by weighting the results by severity, frequency, and reliability to help with prioritization of sensitive information. The location of this content matters because of who has access to it, so the Risk Profile report should be combined and exported with additional reports that cover the permissions policy and activity on this sensitive information.
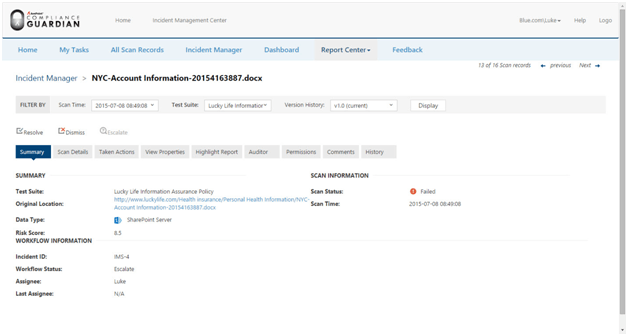
DocAve Security Search provides a holistic view of the permissions in SharePoint. This report simplifies greatly the permissions audit and recertification process. It is easy to get the full picture of who has access to what, what level of access users have, potential action they can take, and – as an administrator – make changes to the permissions as necessary all from the same report.
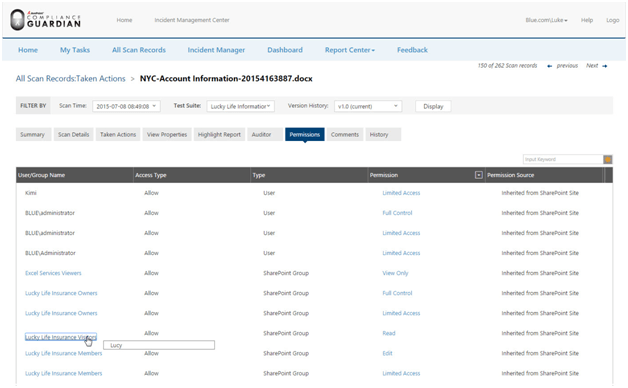
Permissions Profile
The final piece of the puzzle is provided by the DocAve Compliance Reports which show exactly what actions users took within the target scope. Was sensitive content viewed or downloaded? Were permissions changed that increased risk? What actions were taken prior to a major event? These are all questions that can be answered by Audit Reports.
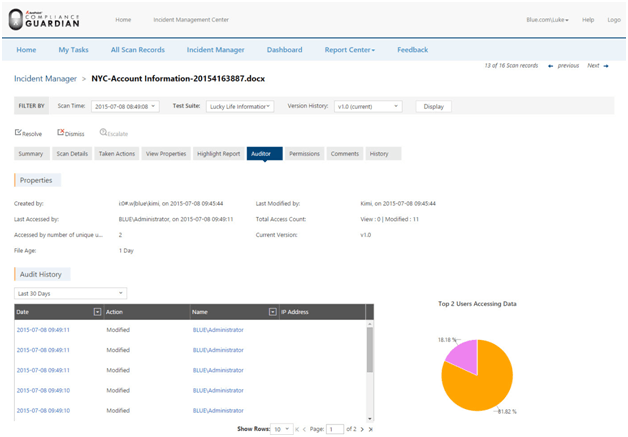
Get Your Free Assessment Guide
All these reports can be easily automated and delivered to the people who need them. They provide a level of insight into SharePoint that is not possible natively and absolutely vital to continued assessment of risk in the environment. By making these processes an integral part of IT’s function, admins protect themselves and their organizations from unintentional risk and have the tools they need to survive audits, breaches, and security incidents on the platform.
Want more advice on how to assess your SharePoint environment? Register for our free Survival Guide for Assessing SharePoint today!

