Using passwords for our computer systems has had a long and checkered history. Ever since the first digital password was used at Massachusetts Institute of Technology in 1960, millions worldwide have grown accustomed to creating a password to get into many digital systems. It’s become as common as breathing.
However, using passwords has become more critical than before.
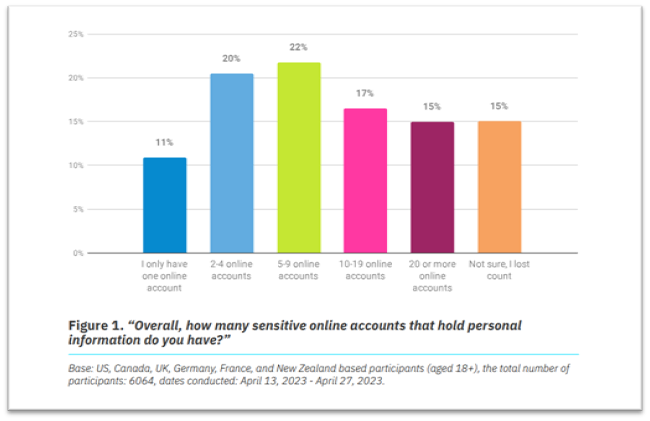
As technology continues to evolve, the number of applications and websites people use for work and personal purposes is increasing. According to the National Cybersecurity Alliance’s (NCA) Oh Behave: The Annual Cybersecurity Attitudes and Behaviors Report 2023, almost half (47%) of people have 10 or more sensitive online accounts, such as payment-related accounts and email accounts. In addition, 15% said they have lost count of their online accounts. This matters because every application and website requires a username and password, which means people have to remember multiple passwords.
And when you factor in the increasing frequency of cybersecurity attacks and data breaches, the importance of password security cannot be overstated. In fact, over 80% of confirmed security breaches come from stolen, weak, or reused passwords.
Despite increasing threats from poor password hygiene, many still take shortcuts with their passwords.
How Are People Managing Their Passwords Today?
In line with Cybersecurity Awareness Month, we looked into some trends in password creation and usage among individual users and employees. The NCA’s 2023 report showed some worrying statistics:
Password Creation
- 46% create passwords 9-11 characters long, but 30% go shorter than that
- 34% resort to using a single dictionary word or someone’s name, only adding numbers and/or symbols for good measure
- 32% included personal information, such as names
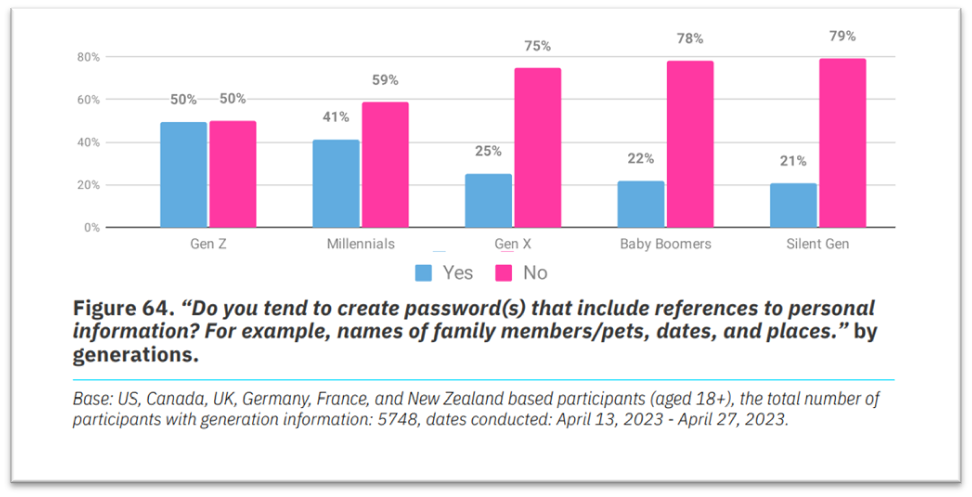
- 50% of Gen Z and 41% of Millennials use names of family members or pets, dates, and places in their passwords
Password Management
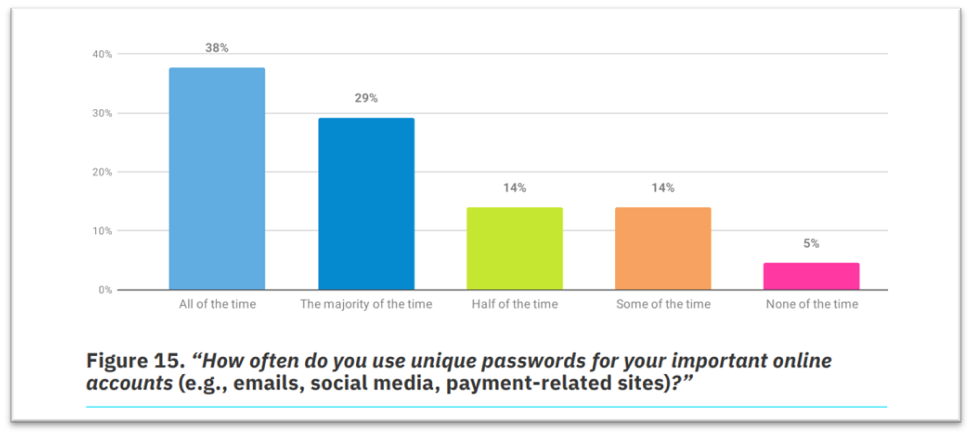
- 33% juggle fewer passwords for their important online accounts
- 34% only change sensitive online account passwords if they have to, with 37% of Gen Z and 44% of Millennials only updating a few characters or a couple of words
Regardless of current creation and usage practices, passwords serve as the entry point into companies’ environments, which host a treasure trove of data and confidential information.
This is why it is crucial to further cybersecurity awareness across the organization. Every IT leader and information security professional should have a plan to ensure passwords are as secure as possible as part of a more comprehensive information security approach.
Create Your Password Security To-Do List
To avoid any cybersecurity breach, creating a strong and secure password is the first line of defense against cyber-attacks. However, with the increasing number of online accounts and passwords we need to remember, ensuring each one is secure can be challenging. That’s why having a password security to-do list and instilling cybersecurity awareness among employees is essential.
- Educate, educate: The importance of cybersecurity training cannot be stressed enough to ensure the security of the workforce’s accounts and company information. The NCA report found that of participants who attended cybersecurity training, 57% began following instructions on using strong and separate passwords. However, an alarming 53% of employees do not have access to cybersecurity training. It is high time that companies drive cybersecurity awareness through employee training.
- Not “if,” but “when:” Start with the assumption that someone’s password will be compromised and prepare your approach accordingly. Hackers have exposed more than 24 billion passwords in 2022
- Encourage unpredictability: Password entropy measures how unpredictable (read: harder for a hacker to guess) a password is, leading to potentially lower cybersecurity risk. It is based on the character set you use, which you can expand through lowercase letters, uppercase letters, numbers, and symbols. According to the National Institute of Standards and Technology’s password guidelines, the recommended length for a secure password is more than 12 characters or a string of three or more words.
- Monitor and act: Hackers can try thousands, tens of thousands, or even hundreds of thousands of password attempts per second to crack into accounts. Prevent the number of attempts and window of attack by implementing password lockouts and password expiration. Implement reporting and monitoring to detect and lock out suspicious sign-ins.
- Implement MFA with passwords: Users face the issue of remembering their passwords, which leads to simple and reused passwords that others may also use. Implement MFA that includes something unique to you – whether it’s something you have (such as a token, authenticator app, or access card) or something you are (such as biometrics). Microsoft found that among human-operated ransomware attacks, 88% of engagements are from those without MFA, making it easier to run a cybersecurity attack.
- Think of password security as one brick in your security wall: Implementing strong password security policies is important, but it’s just one way to fortify your organization from cybersecurity attacks. Consider implementing firewalls, role-based access controls (RBAC), data loss prevention (DLP) scanning, and virtual local area networks (VLANs) as part of your information security approach.
Securing Your Sensitive Information with AvePoint
At AvePoint, we help organizations implement a robust cybersecurity framework. Our solutions, processes, and people follow industry standards and best practices for security and compliance. We adhere to and have been certified against the industry standards for security and privacy, such as:
- ISO 27701:2019
- ISO 27001:2013 and ISO 27017:2015
- Cloud Security Alliance (CSA) Level 2
- SOC 2 Type II
- FedRAMP
- IRAP

We also enable our customers to leverage their Microsoft Entra ID (formerly Azure Active Directory) for authentication with our cloud solutions and Active Directory Federation Services for those using our on-premises solutions. This enables organizations to use their existing password security and management protocols.
For more information on how AvePoint places safety in the hearts of our customers, visit the AvePoint Trust Center.



