The cloud has become the favorite hunting ground for cybercriminials, and the statistics paint a clear picture that enterprise applications are becoming their favorite prey. According to the Google Threat Intelligence Group's 2024 Zero-Day Exploitation Analysis, 44% of the 75 zero-day vulnerabilities exploited in 2024 specifically targeted enterprise technologies. This trend marks a significant shift toward business data, applications, and infrastructure.
Meanwhile, Gartner predicted that end-user spending on public cloud services worldwide would rise by 20.4% in 2024, reaching $675 billion from $561 billion in 2023. This growth – driven by generative AI (GenAI) and other cloud technologies, whose ROI depends on the amount of data available – expands the attack surface by bringing more and more data into the scopes of malicious actors.
Where the data resides and how it is consumed may vary, but many of the ways attackers infiltrate your cloud infrastructures remains the same whether it's infrastructure-as-a-service (IaaS), platform-as-a-service (PaaS), or software-as-a-service (SaaS). Understanding these attack vectors isn't just an IT concern; it's a business imperative that directly impacts your organization's resilience, compliance posture, and bottom line.
Decoding the Cloud: IaaS, PaaS, and SaaS Explained
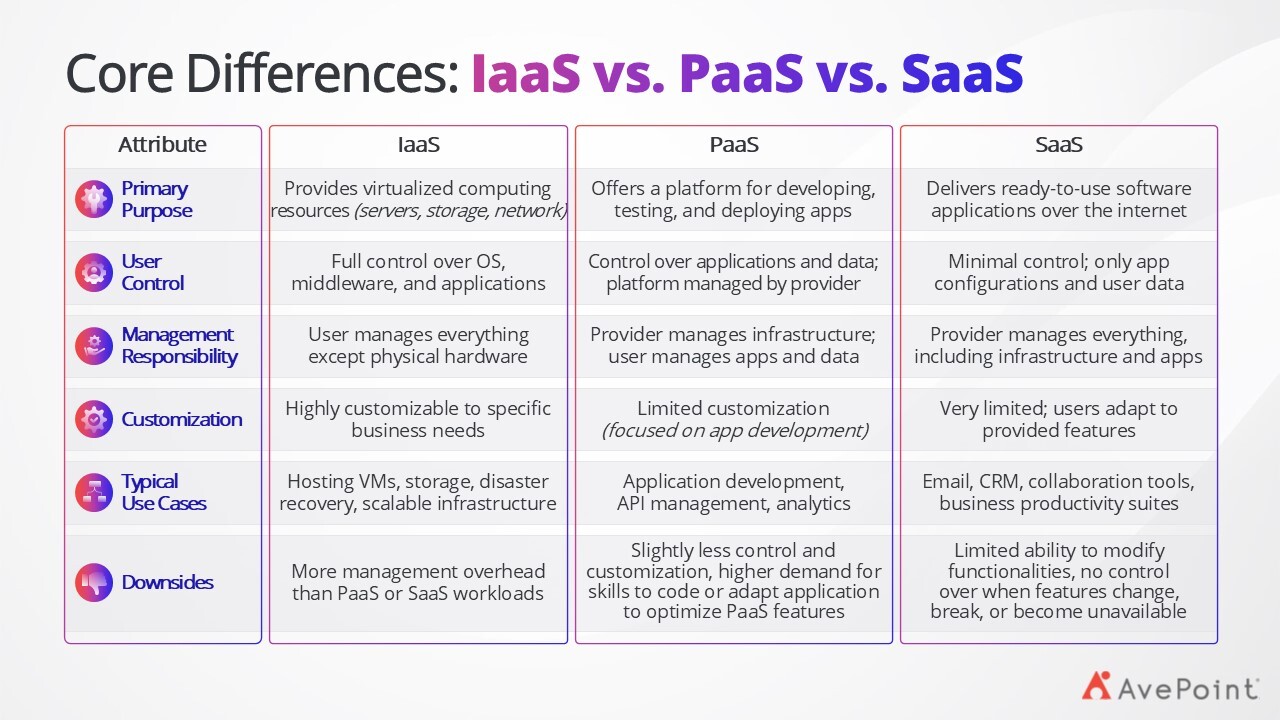
Before diving into attack vectors, it's crucial to understand what distinguishes these cloud service models. Each model offers different levels of control, responsibility, and customization, which directly impacts their security considerations and potential vulnerabilities.
IaaS
IaaS provides virtualized computing resources over the internet, including servers, storage, compute, and network-as-a-service (NaaS). You maintain control over operating systems, applications, middleware, and even get to choose between different chipsets, disks, and machine configurations while the provider manages the underlying physical infrastructure and virtualization. Popular examples include Amazon Elastic Compute Cloud (EC2), Microsoft Azure virtual machines (VMs), and Google Compute Engine. IaaS offers maximum flexibility and control but requires you to handle the configuration and management of security, networking, availability, and more.
Many organizations start with IaaS because it allows them to move much of their legacy server workload to the cloud with minimal changes. This is often called a “lift-and-shift.” This allows organizations to move quickly to the cloud and benefit from leveraging new hardware, lowering costs, and improving the physical security of their infrastructure. The downsides of this model include significantly more management overhead than PaaS or SaaS workloads and higher costs overall.
PaaS
PaaS delivers a development and deployment environment in the cloud, providing tools and services for building applications without managing underlying infrastructure. The provider handles servers, storage, networking, and runtime environments while you focus on application code and data. Examples include Microsoft Azure App Service, Google App Engine, and Heroku.
PaaS reduces management complexity and offers significantly more elasticity than IaaS. Elasticity in computing lets you easily increase or decrease your computer's processing power, memory, and storage as needed — without worrying about capacity planning and engineering for peak usage. The downsides of PaaS include slightly less control and customization, as well as higher demand for the necessary skillsets to code or adapt applications to make full use of PaaS technology.
SaaS
SaaS provides ready-to-use applications hosted in the cloud, accessible through web browsers or application programming interfaces (APIs). The provider manages everything from infrastructure to application maintenance, while you simply utilize the service. Think Microsoft 365, Salesforce, or Slack. SaaS offers maximum convenience and cost savings but minimal control and customization.
The rise of low-code, no-code applications is helping businesses bridge this gap today, while others are actually considering cloud repatriation or the return to traditional on-premises or private cloud infrastructure to satisfy customization, control, or data sovereignty requirements.
Understanding the Most Common IaaS and PaaS Attack Vectors
The cybersecurity landscape has evolved dramatically. Attackers are exploiting common vulnerabilities that often stem from misconfigurations across multiple layers of your cloud infrastructure. These attack vectors represent the most frequent entry points that threat actors use to compromise IaaS and PaaS environments.
1. Entra ID, Okta, or Other Cloud Identity and Access Management Vulnerabilities and Misconfigurations
Cloud identity and access management (IAM) vulnerabilities like Entra ID misconfiguration remain a primary attack vector, as identity and access management systems control the keys to your entire digital kingdom. Attackers target misconfigured identities, weak policies, compromised admin accounts, and inadequate multi-factor authentication implementations.
As we detailed in our previous analysis of Entra ID attacks, these identity-based compromises often serve as the gateway to broader infrastructure infiltration. It is a priority target for attackers to exploit because of the broad and highly privileged access a bad actor can obtain from this entry point in your stack.

2. Cloud Misconfigurations
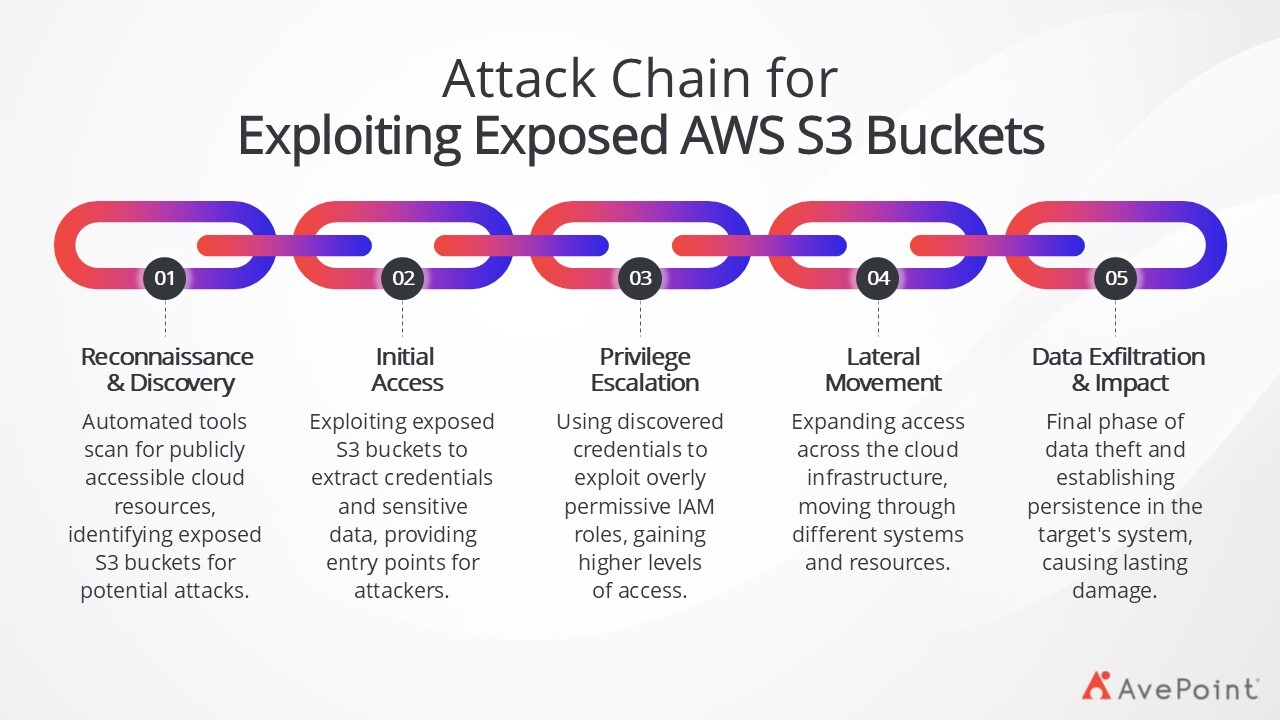
Cloud misconfigurations – such as overly permissive access controls, exposed storage buckets, and improperly configured security groups and network settings – continue to plague organizations.
These seemingly minor oversights create significant security gaps that attackers exploit to gain unauthorized access to sensitive data and critical systems. For example, threat actors can exploit misconfigured Amazon Web Services (AWS) Simple Storage Service (S3) buckets with public read or write permissions, allowing them to access, download, or modify sensitive data and configuration files without proper authentication.
While "security through obscurity" may be protecting you today, any misconfigurations will become easier to detect and exploit as attackers use tools like agentic AI to speed up their search. Attacks like this are less likely as they often require attackers to know things like the names of buckets, subscriptions, services, GUIDs, among others — but these can be obtained through other means in a multi-layered attack.
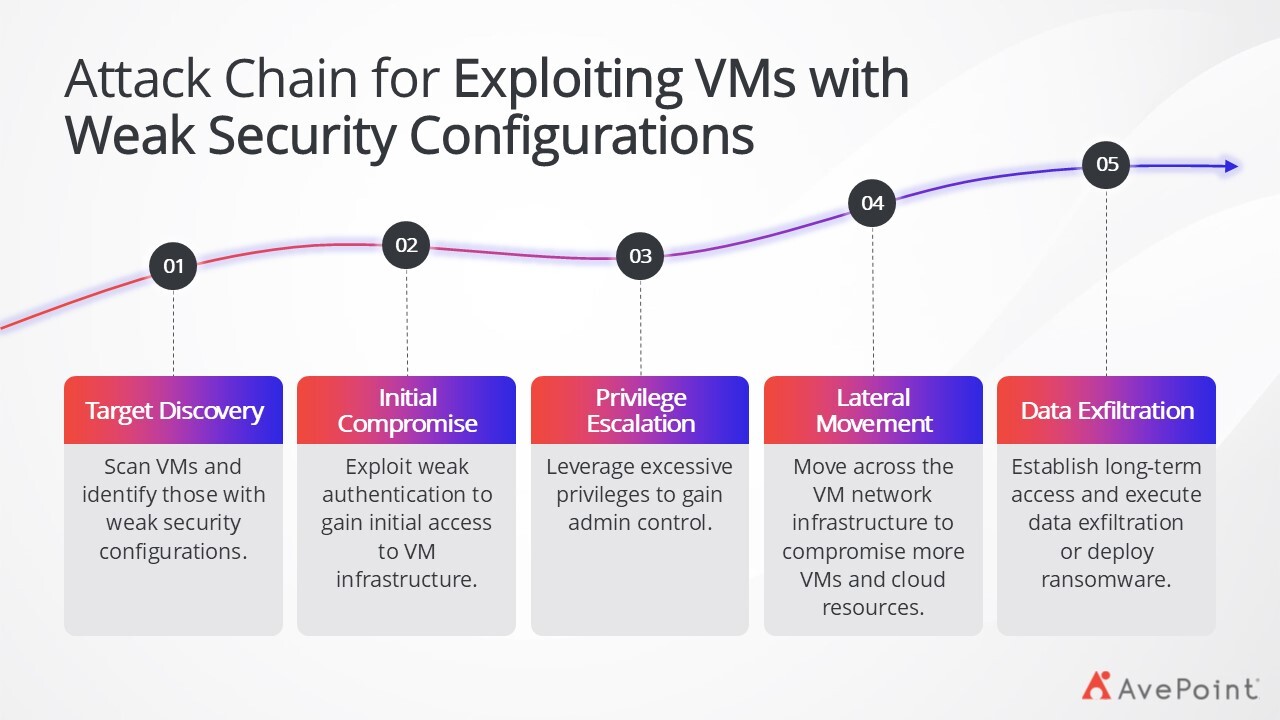
3. VMs Infrastructure Misconfigurations and Insecure APIs
Misconfigurations in VM infrastructure and insecure APIs pose significant threats to your IaaS environment. Poorly secured APIs may lack proper authentication, encryption, or rate limiting, making them vulnerable to attacks. Similarly, VMs can be compromised if their operating systems don’t have the latest security updates, have weak authentication mechanisms (admin, admin on a ‘dev box’ I’m looking at you), are running software or agents with unpatched vulnerabilities, or possess excessive privileges that attackers could exploit for lateral movement across your VM networks.
VMs and infrastructure running more popular OS versions like Windows are more likely to be attacked than various Linux-based distributions as well. There are many different factors at play, but all of them point to you needing to secure your infrastructure top to bottom.
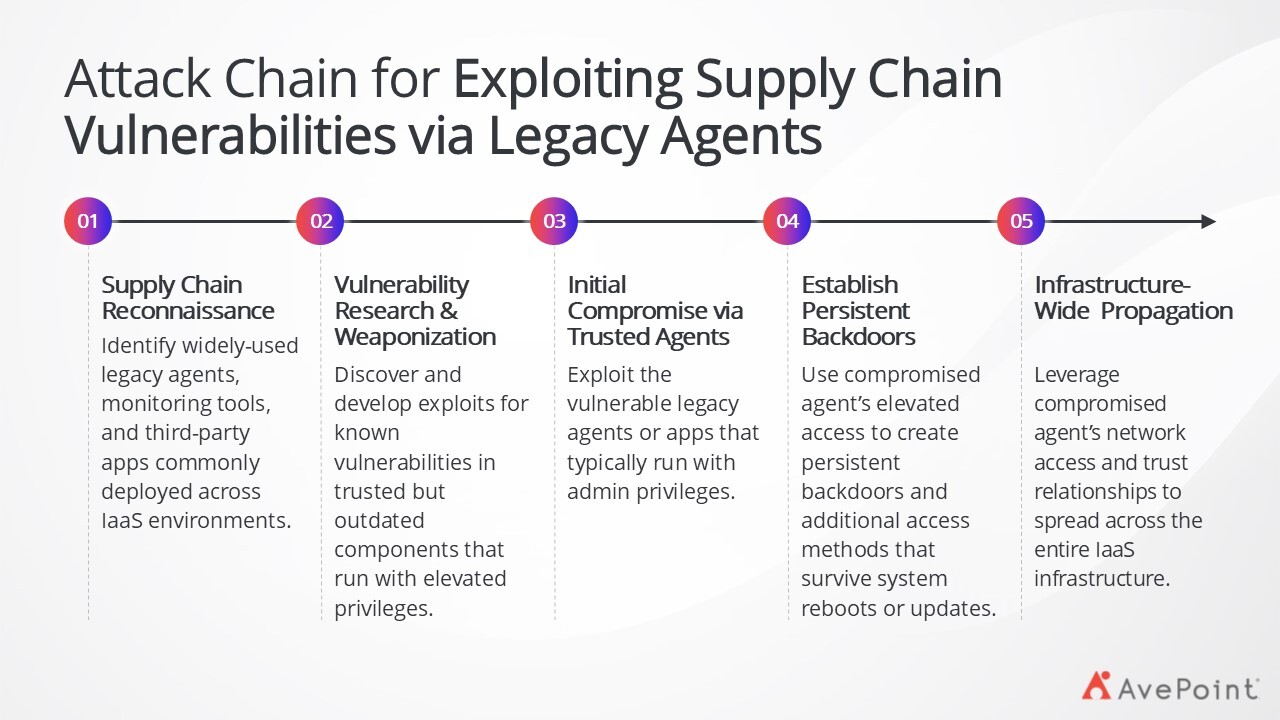
4. Supply Chain Vulnerabilities
Supply chain vulnerabilities pose an increasingly sophisticated threat, particularly through legacy agents installed on IaaS servers and outdated applications that contain known security flaws. These components often operate with elevated privileges and may lack regular security updates, creating persistent backdoors to your infrastructure.
With malicious actors now using agentic AI to exploit vulnerabilities faster than ever before, fortifying the security posture of your IaaS environments becomes a top priority. A recent Gartner report forecasts that by 2027, AI agents will reduce by 50% the time it takes to exploit account exposures. The report further warns that threat actors will increasingly use agentic AI to exploit weak authentication by automating credential theft and compromising authentication communication channels. This raises a critical question: How are you planning to recover when all preventive measures fail?
How to Strengthen Your IaaS and PaaS Security Posture
While the threat landscape continues to evolve, organizations can implement strategic defensive measures to significantly minimize their risk exposure and build resilience against sophisticated attacks. The key lies in adopting a multi-layered security approach that addresses both prevention and recovery.
1. Implement Zero-Trust Architecture with Comprehensive Identity Management
Move beyond traditional perimeter-based security by implementing zero-trust principles that verify every user, device, and application before granting access. This includes strengthening your Entra ID configurations, implementing robust multi-factor authentication (MFA), and regularly auditing privileged accounts. AvePoint's Confidence Platform can help you implement comprehensive identity governance while our detailed guide on protecting against Entra ID attacks provides actionable strategies for securing your identity infrastructure.
2. Administer Automated Configuration Management and Continuous Monitoring
Establish automated systems to detect and remediate cloud misconfigurations in real-time. This includes implementing API security gateways with proper authentication and rate limiting, along with maintaining comprehensive visibility across your entire infrastructure stack.
The Confidence Platform can help organizations achieve this by providing tools for automated configuration management. Specifically, its Policies feature automates common rules for access, settings, and external sharing — ensuring consistent policy implementation and catching configuration drift effectively. This proactive approach not only enhances security but also enables organizations to respond quickly to potential threats.
3. Build Resilient Recovery Capabilities with App-Aware Backup Solutions
Given that prevention alone isn't sufficient in today's threat landscape, organizations must invest in robust recovery capabilities. AvePoint Cloud Backup, as a feature of the Confidence Platform, provides app-aware recovery that enables organizations to restore their entire digital environment to its pre-incident state. This includes comprehensive configuration rollback capabilities that can quickly restore not just data, but also the security configurations and access policies that were in place before an attack occurred.
Turning Defense into Competitive Advantage: Your Path Forward
Proactive measures today can prevent the costly aftermath of tomorrow's attacks.
Building robust cybersecurity defenses and resilient recovery capabilities isn't just about protection — it's about enabling business confidence and competitive advantage. When your organization can demonstrate strong security posture and rapid recovery capabilities, you earn customer trust, meet compliance requirements more effectively, and pursue digital transformation initiatives with greater confidence. The key is adopting a proactive mindset that views cybersecurity not as a cost center, but as a strategic enabler of business growth and innovation in our constantly evolving digital world.
An ounce of prevention is worth more than a pound of cure. Don’t wait for an attack to expose vulnerabilities in your IaaS and PaaS environments. Learn more about how AvePoint can help boost your infrastructure's cyber defenses in this free on-demand webinar::


