Nearly every organisation has an Achilles’ heel: 90% of organisations have at least one attack path, and 80% have attack paths that expose critical assets, as highlighted in the Microsoft Digital Defense Report 2024. Notably, 43% of organisations have poor Azure Active Directory (AD) configurations that leave them vulnerable to attacks.
The cyberattack by an Iranian advanced persistent threat (APT) group exemplifies this: Malicious actors exploited a simple misconfiguration that enabled them to gain full access to the victim’s Azure AD environment, causing massive destruction to critical digital assets.
The Microsoft report also revealed that over the past year, Microsoft blocked 7,000 password attacks per second, underscoring the persistent and pervasive nature of these threats. Moreover, threat actors have built extensive infrastructure dedicated to scouring the digital world for passwords, significantly supporting these identity-related attacks.
These figures highlight the urgent need to protect enterprise identities, particularly against attacks targeting systems like Microsoft Entra ID (formerly Azure AD) that serve as the gateway to their digital assets. This blog provides a comprehensive understanding of the attack vectors used by threat actors to compromise Entra ID and offers actionable insights to strengthen your defences against such threats.
Understanding Entra ID Attack Vectors
Let’s explore some of the most common entry points that threat actors exploit to execute their attacks:
1. Phishing Attacks
Phishing is a common method threat actors use to compromise Entra ID environments. This type of social engineering attack often starts with deceptive emails or messages impersonating trusted entities like Microsoft, IT support, or colleagues. The emails or messages contain urgent requests or alarming notifications to trick recipients into clicking on malicious links.
Once users access these links, they are directed to convincing replicas of familiar login pages, such as the Microsoft authentication portal. When credentials are entered, attackers capture them in real-time and can immediately access the victim’s Entra ID account. With valid credentials, malicious actors can bypass traditional security measures, posing a significant threat to organisations relying on Entra ID for identity management.
For EU organisations subject to strict data protection regulations like the General Data Protection Regulation (GDPR), the Network and Information Systems Directive (NIS2), and the Digital Operational Resilience Act (DORA), a successful phishing attack can have severe compliance implications, potentially leading to hefty fines and reputational damage.
Figure 1 shows how cybercriminals carry out a successful phishing attack:
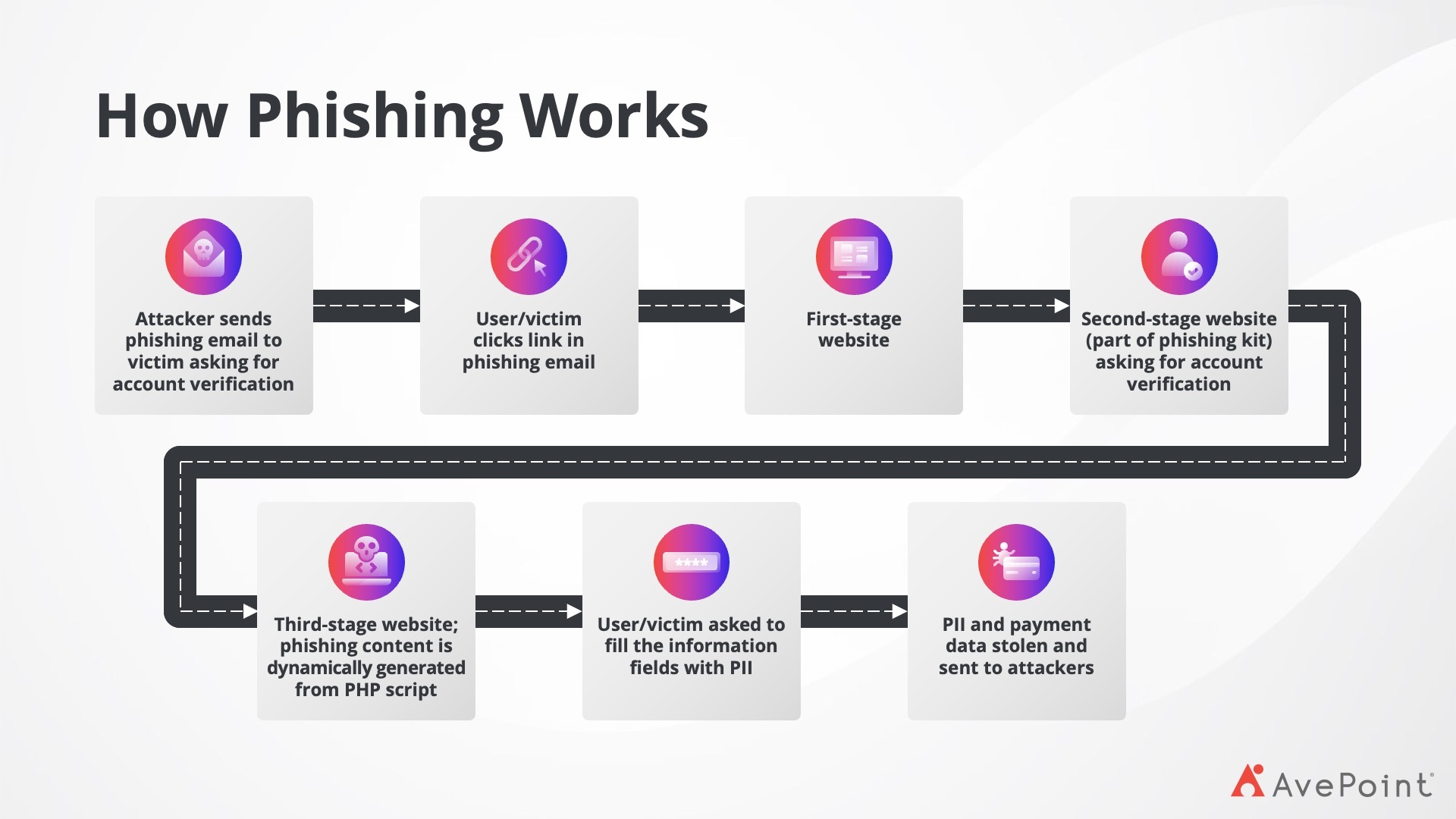
2. Password Spraying
Unlike brute force attacks that target a single account with multiple password attempts, password spraying uses a few common passwords against many accounts. This technique helps attackers avoid account lockouts whilst increasing their chances of finding vulnerable credentials.
Password spraying is particularly effective in Entra ID environments where users may have weak, predictable passwords or where robust password policies are lacking. The attack typically starts with threat actors collecting valid usernames through Open Source Intelligence (OSINT) techniques, such as examining corporate websites, LinkedIn profiles, or other public sources.
Once they have a list of valid usernames, attackers systematically try commonly used passwords (like "Company2024!" or "Password123") across all accounts. Even if only a small percentage of accounts use weak passwords, this method can yield successful breaches, providing attackers with initial access to your Entra ID environment.
Figure 2 illustrates how password spraying works:
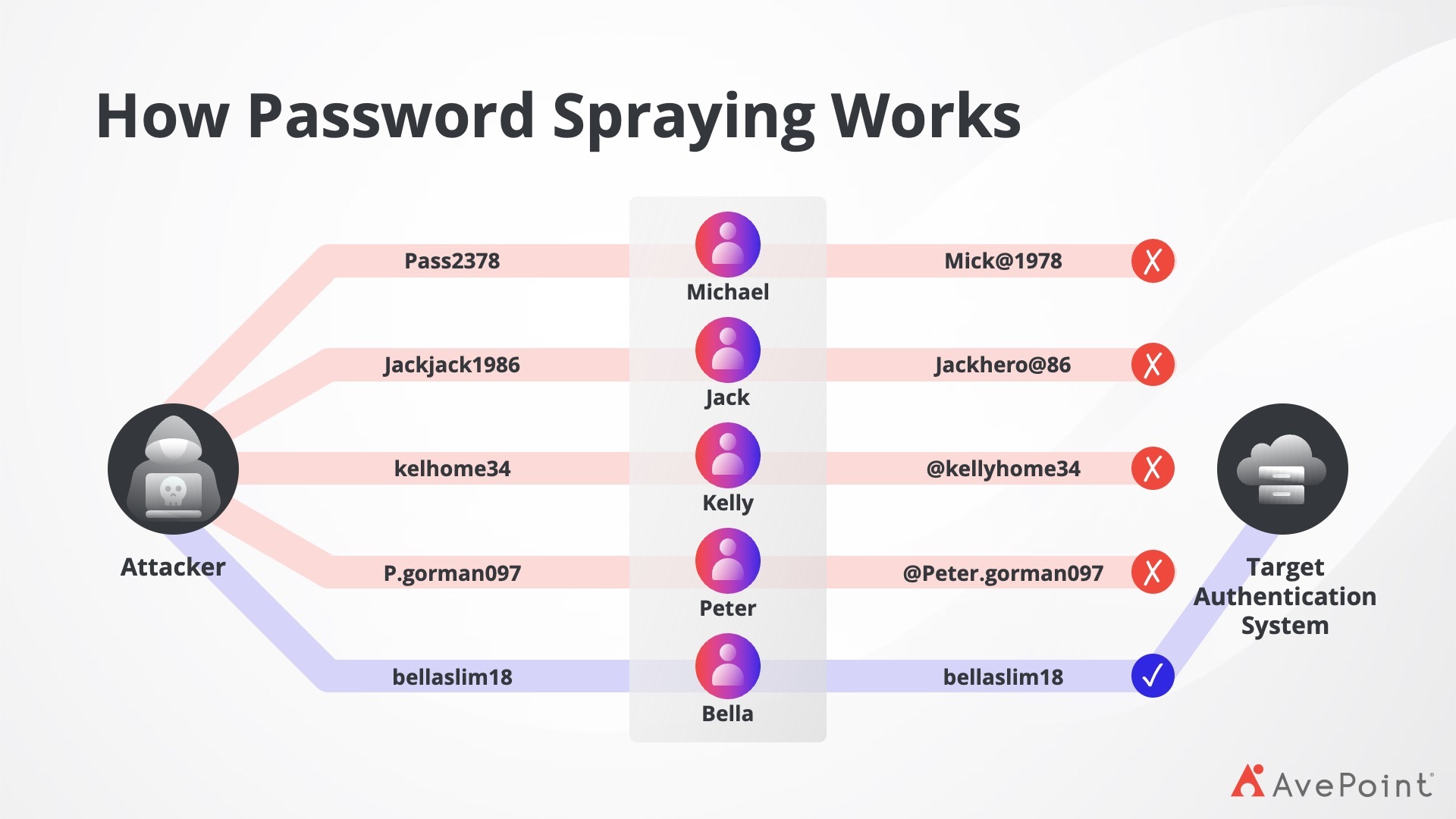
3. Misconfigurations and Poor Access Controls
After gaining initial access to an Entra ID environment, threat actors aim to escalate their privileges to reach higher-value targets by exploiting misconfigured roles, excessive permissions, or vulnerabilities in an organisation’s identity management infrastructure.
A common technique is targeting accounts with administrative privileges through lateral movement. Once attackers compromise a standard user account, they examine its relationships and permissions to find pathways to privileged accounts. They may exploit trust relationships or permission vulnerabilities to gradually increase access rights.
Malicious actors may access regulated data protected under GDPR or NIS2. Without proper privilege management and monitoring, these escalations can go undetected until significant damage occurs.
Figure 3 shows one of the ways that cybercriminals leverage poor access controls to launch an attack on an organisation’s Entra ID environment:
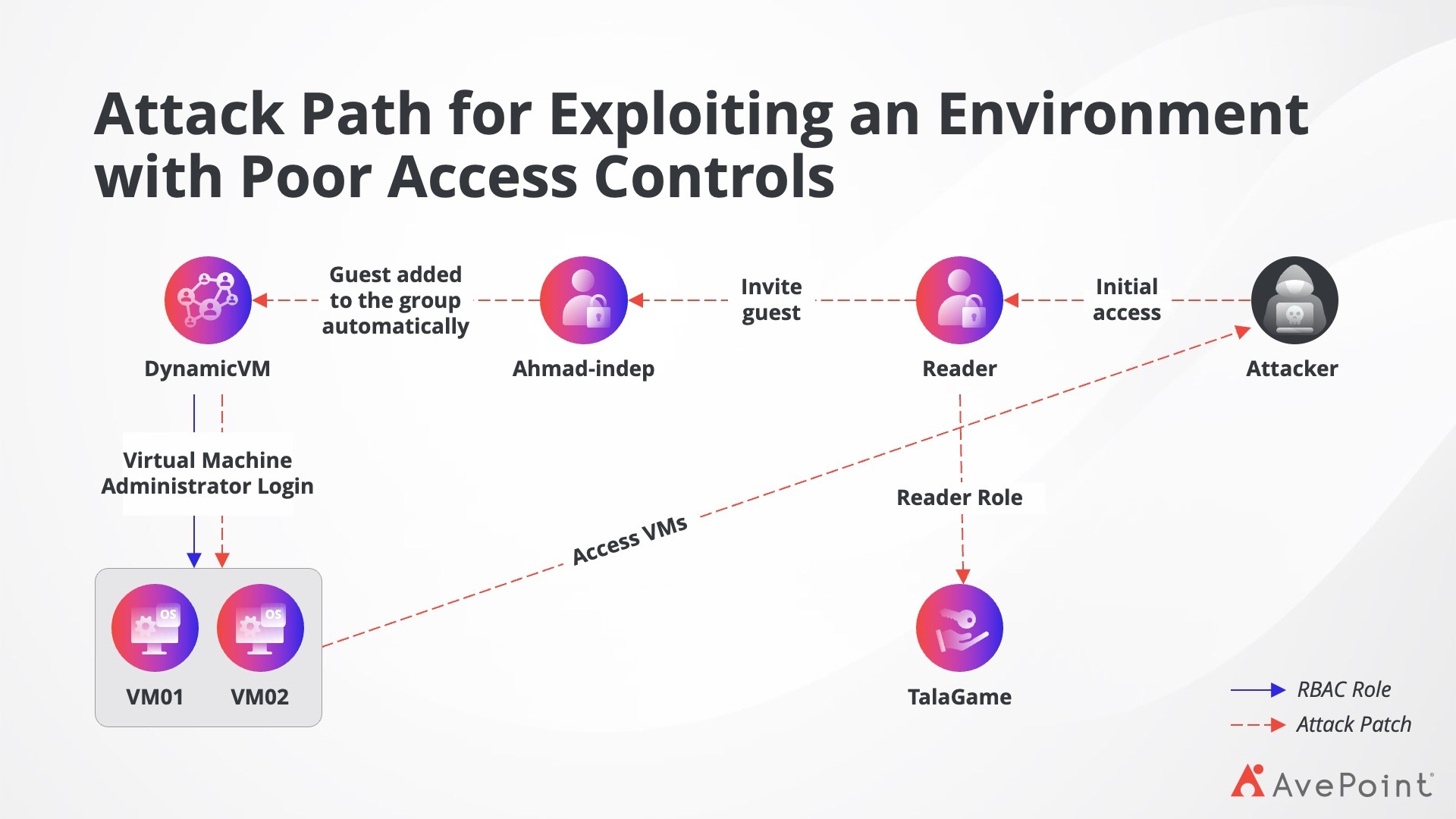
4. Malicious Applications
Entra ID’s integration with OAuth 2.0 and OpenID Connect allows third-party applications to request permissions for resource access on behalf of users. Although this feature can boost productivity, it also presents a tempting target for attackers.
Threat actors can create malicious applications that request excessive permissions during the consent process. When users grant these permissions, often unknowingly, attackers gain authorised access to sensitive resources like email and data. These permissions persist until explicitly revoked, allowing long-term access even if passwords are changed.
This poses a risk of unauthorised data transfers outside the EU, potentially violating GDPR. Equally concerning is that attackers can use malicious applications to extract data and operate with user-granted permissions, making this attack vector hard to detect through traditional security monitoring.
Figure 4 helps you visualise the attack chain carried out by cybercriminals using malicious OAuth applications:
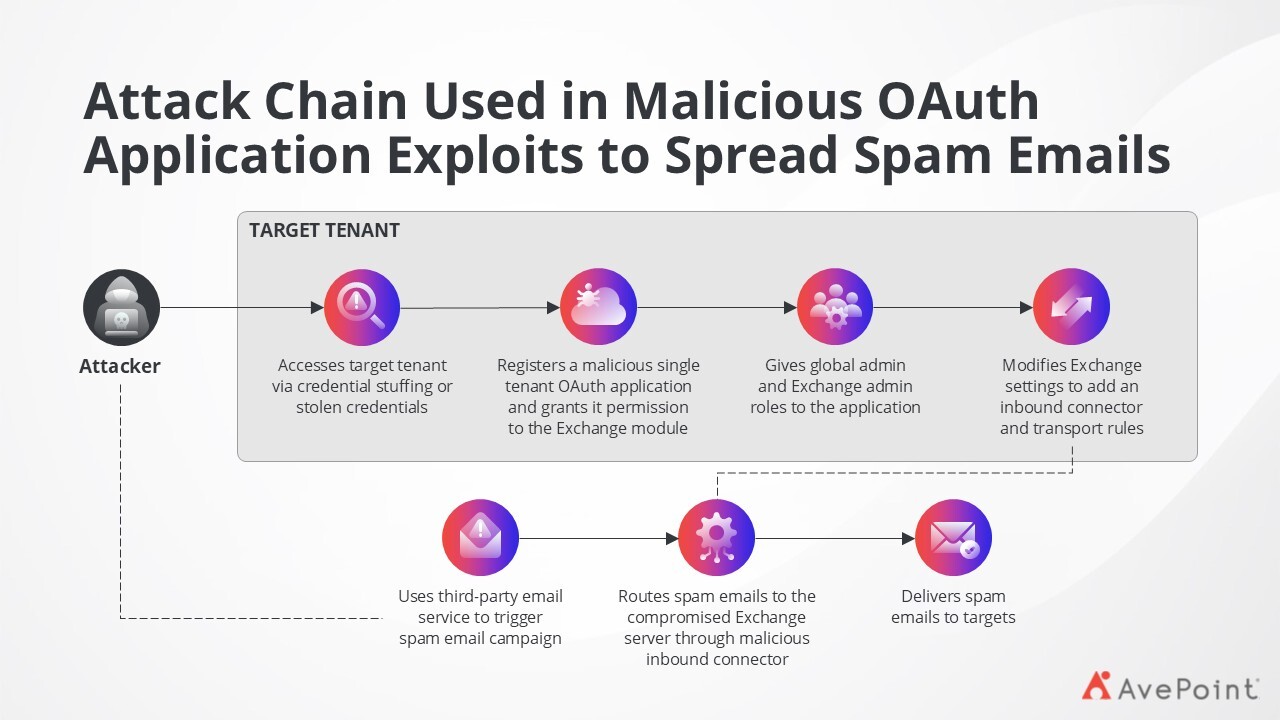
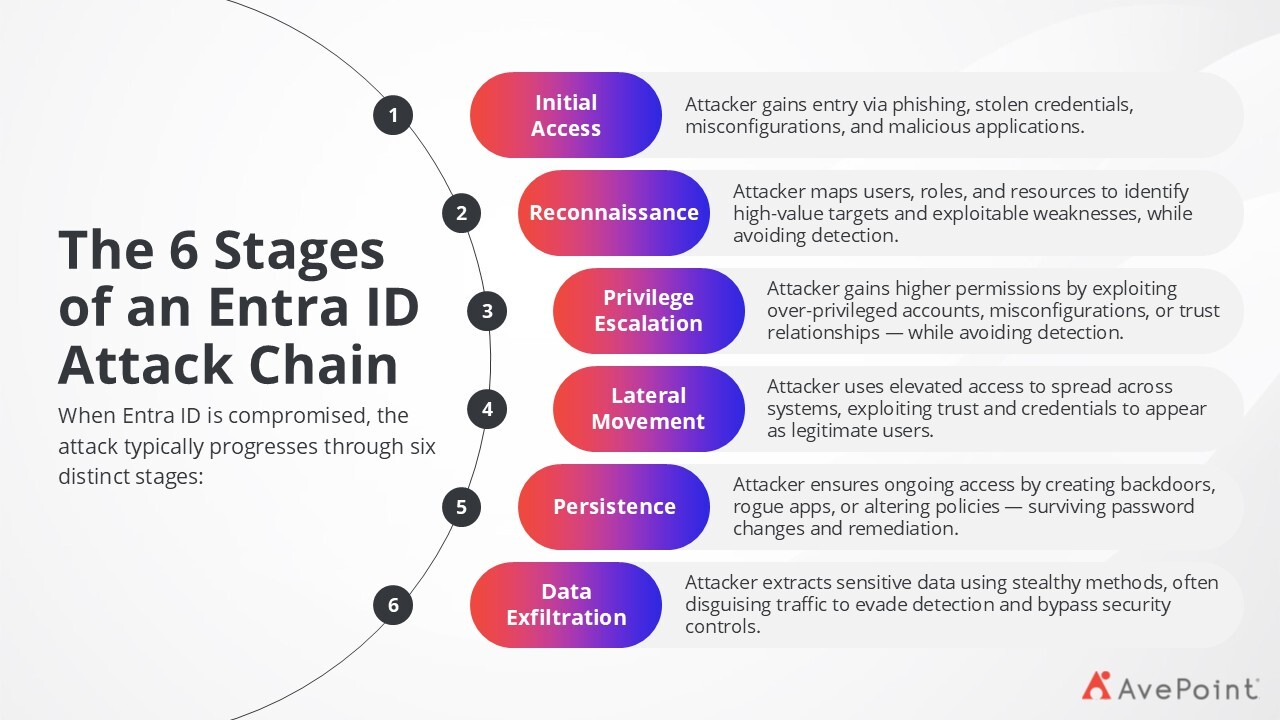
The 6 Stages of an Entra ID Attack Chain
When Entra ID is compromised, the attack typically progresses through six distinct stages shown in Figure 5:
How Backups Neutralise Entra ID Attacks
A robust backup solution serves as your organisation’s insurance policy against Entra ID compromises, providing the ability to quickly restore clean environments whilst maintaining business continuity. Proper backups can dramatically reduce recovery time and mitigate regulatory impacts.
1. Rapid Restoration
When Entra ID is compromised, time is of the essence. Comprehensive backups enable organisations to rapidly restore their environment to a known clean state, minimising both downtime and operational impact. Unlike manual recovery processes that can take weeks, as thousands of different settings and configurations are possible, automated restoration from verified backups can reduce recovery time to hours or even minutes.
For organisations operating across multiple time zones, this rapid restoration capability ensures business continuity and maintains compliance with regulatory requirements for service availability and business continuity. The ability to quickly restore access management systems also prevents cascading failures across dependent systems and applications.
During recovery, advanced solutions like AvePoint Cloud Backup can compare backup versions, highlighting only the changed objects. With thousands of configurations, you don’t want to waste time verifying sensitive workloads for restoration. AvePoint Cloud Backup shows exactly what has changed, allowing you to restore from a simple list. This speeds up recovery and ensures no misconfigurations are missed.
2. Granular Recovery
Not all compromises require complete environment restoration. Advanced backup solutions like AvePoint Cloud Backup offer granular recovery options that allow security teams to restore specific elements such as individual user accounts, group memberships, or conditional access policies. This targeted approach minimises disruption whilst effectively addressing security incidents.
Granular recovery is particularly valuable when dealing with selective compromises or when maintaining business operations is critical. It allows security teams to address specific attack vectors without affecting the uncompromised components of your identity infrastructure, maintaining accessibility for legitimate users whilst removing malicious elements.
3. Configuration Rollback
Threat actors often modify Entra ID configurations to establish persistence or facilitate lateral movement. These changes can include alterations to conditional access policies, authentication requirements, or permission assignments. Backup solutions provide the ability to identify and roll back these malicious configuration changes.
With AvePoint Cloud Backup’s comprehensive configuration rollback, security teams can compare current settings against previous states to identify unauthorised modifications. This capability is essential for thwarting attackers’ persistence mechanisms and restoring proper security controls. Organisations with complex compliance requirements need to maintain accurate configuration history to support audit requirements.
4. Forensic Analysis
Backup solutions can provide invaluable forensic information during and after security incidents. By comparing pre-attack and post-attack states of your Entra ID environment, security teams can identify compromised accounts, unauthorised applications, or modified permissions that indicate attacker activity.
This comparative analysis supports thorough incident investigation and helps organisations understand attack patterns, improve detection capabilities, and strengthen preventative measures. Organisations subject to breach notification requirements like NIS2 will find these forensic capabilities essential for regulatory compliance.
Solutions like AvePoint Insights enable you to search data stored for up to three years and export your data at any time. It uses role-based access control (RBAC) to simplify granting feature-specific access. IT admins can easily provide auditors with the necessary permissions for their investigations whilst ensuring other sensitive data, systems, and tools remain accessible only to authorised personnel.
Beyond Reactive Security: Boost Your Defences with AvePoint
The evolving threat landscape demands more than just reactive security measures for Entra ID protection. Whilst understanding attack vectors and implementing backups are essential, organisations must adopt a proactive, defence-in-depth approach to truly secure their identity infrastructure.
Consider implementing continuous real-time monitoring solutions to detect anomalous activities within your Entra ID environment. Utilise adaptive authentication methods that assess risk based on user behaviour, location, and device health before granting access. Regularly conduct privilege access reviews to identify and remove excessive permissions that attackers can exploit.
For comprehensive protection, explore AvePoint’s Cloud Backup for Microsoft Entra ID. Our solution provides automated, comprehensive backups with rapid restoration capabilities, granular recovery options, and powerful forensic tools — all designed to neutralise the impact of identity-based attacks and maintain business continuity.
Don’t wait for an attack to expose vulnerabilities in your identity infrastructure. Learn more about how AvePoint can help strengthen your cyber defences in this free webinar:


