Are you looking for ways to effectively govern your Office 365 environment? If so, check out our free Office 365 cloud governance webinar!
For Part 1 of this post, click here.
Perhaps one of the most frequently asked questions during customer conversations on how to protect their data is “How can I prevent data overexposure, both on-premise and in the cloud?”
It’s not a secret that the unfortunate reality for every CISO is the fact that with cloud technologies, the security perimeter is no longer within a given radius of the environment they work in.
Compounding the issue, security is as good as the weakest link (the human factor) in the organization. With cloud systems like Box or Dropbox, for example, sharing (or exposing) data outside of an organization is as easy as an employee uploading files and clicking a button.

Your first reaction might be to announce “Okay, it’s against company policy to store confidential data in system XYZ” and problem solved, but as a former CISO I can assure you that the next step employees would take is to bypass that statement and use another solution–SharePoint Online or OneDrive for Business for example.
If it’s not forbidden, it means it’s allowed. It’s not that you shouldn’t trust your employees, but it’s much better to understand how data is being used and how it can potentially go outside of your organization.
Want to know how to effectively monitor and act on unwarranted external user activity in Office 365? Check out this post:Click To Tweet
In Part 1 we covered how to monitor and report on Office 365 file usage by external users. While this is great, reporting alone isn’t enough to prevent unintentional data breaches.
AvePoint’s Compliance Guardian helps organizations proactively monitor and neutralize violations of privacy, security, and compliance. It ensures information security across unstructured and structured data both at rest and in motion. It also applies classification that can drive records management policies, migrations, and other assessments and take preventative action to protect information.
To get started, we need to:
1) Create a check for external sharing
2) Add the check into a Test Suite
3) Create your Scan Plan using the newly-created Test Suite
How to Create a Check in Compliance Guardian
- Open Compliance Guardian, go to Control Panel, then Check Manager:
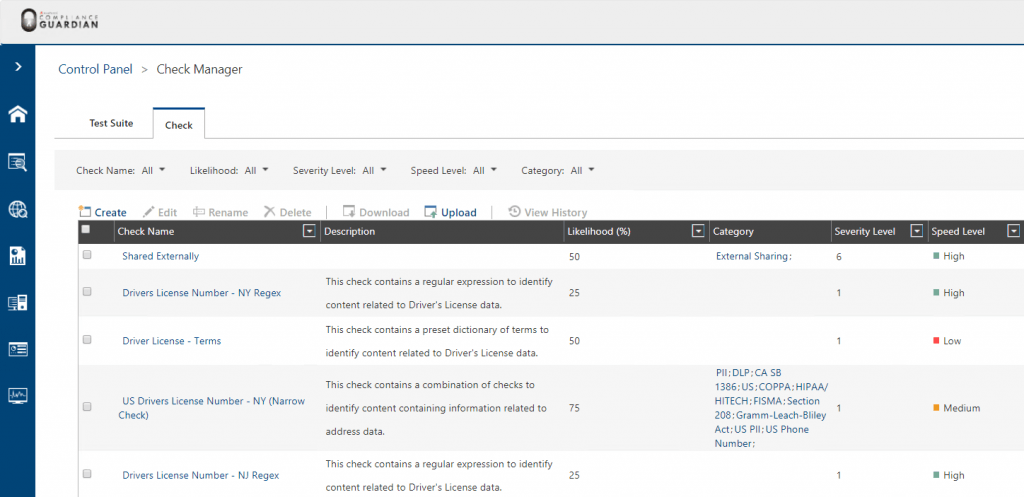
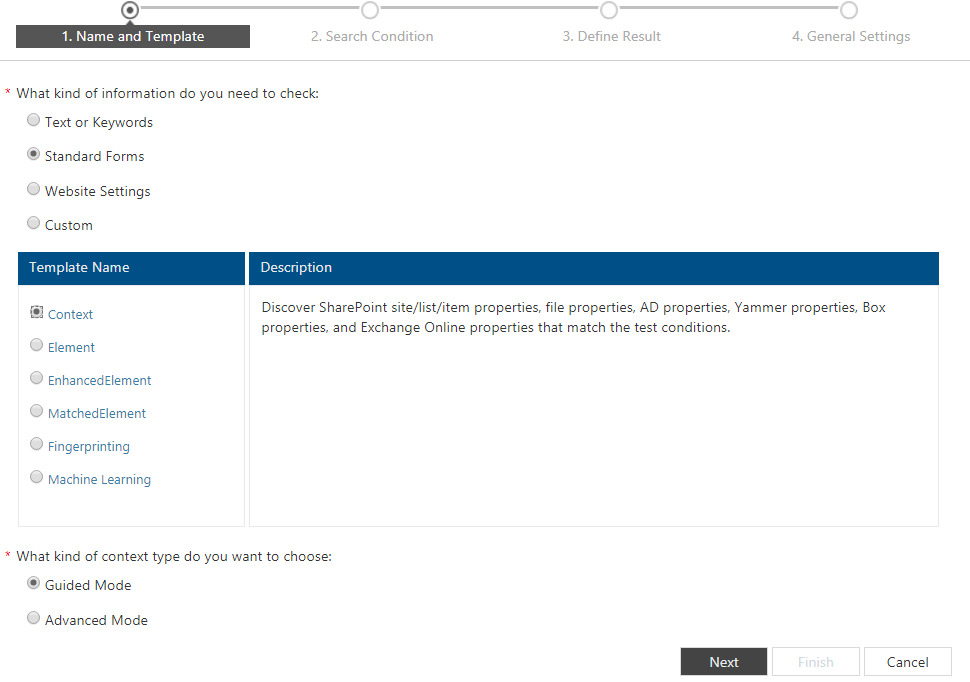
- Within the Check Manager, click on Check > Create and then from the Standard Forms select the Context Check:
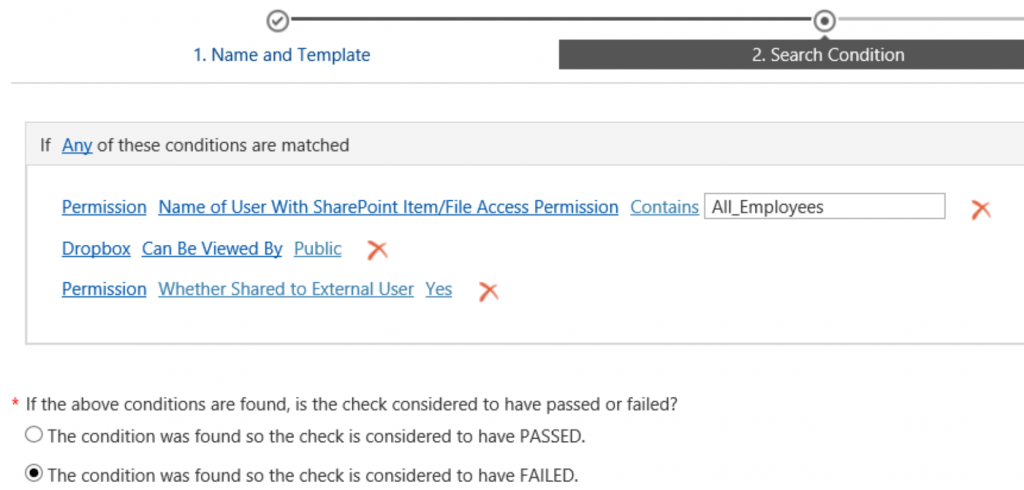
3. From Search Condition, we can define our conditions and requirements. Within one Context Check you can utilize multiple requirements. For example, you can check if a file is shared externally and/or with everyone in your organization.
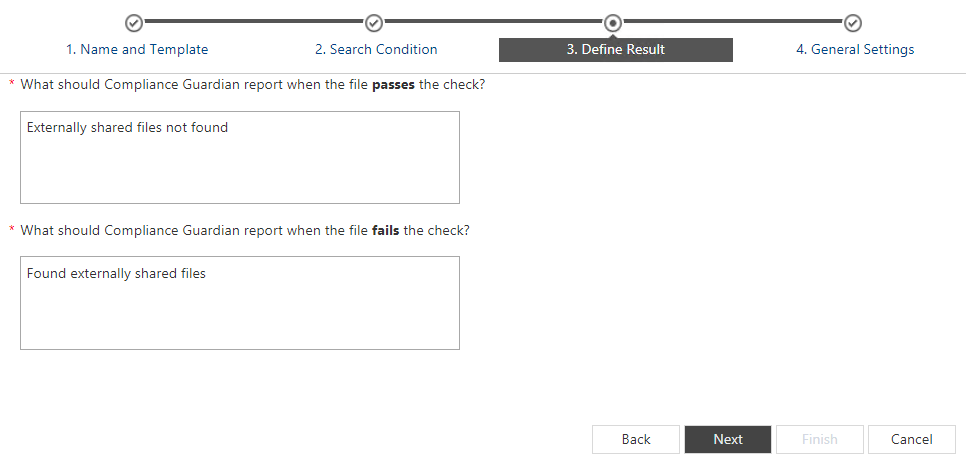
- The next step is to define the message result depending on the discovery outcome. If the Context Check identifies an externally-shared document, the scan would result in a fail.
How to create a Test Suite in Compliance Guardian
- Once the check has been created and saved within the system, the next step is to Create a Test Suite and add the new check.
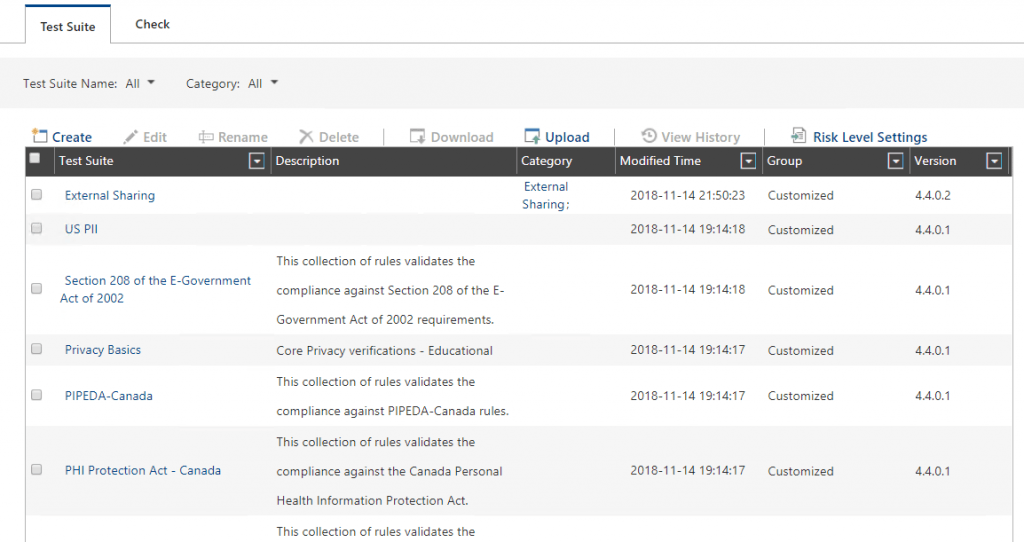
- Select the option for Privacy, information assurance or operational security issues:
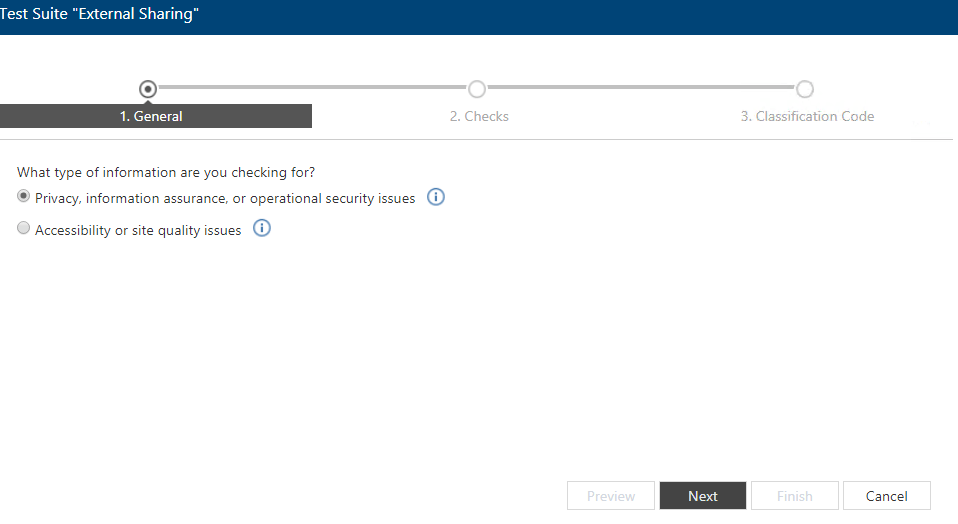
- Click on Add Check. You can combine multiple checks for different scenarios. For example, you can identify if a file is externally shared while also scan to see if the file contains any sensitive data (something that would significantly worsen the situation).
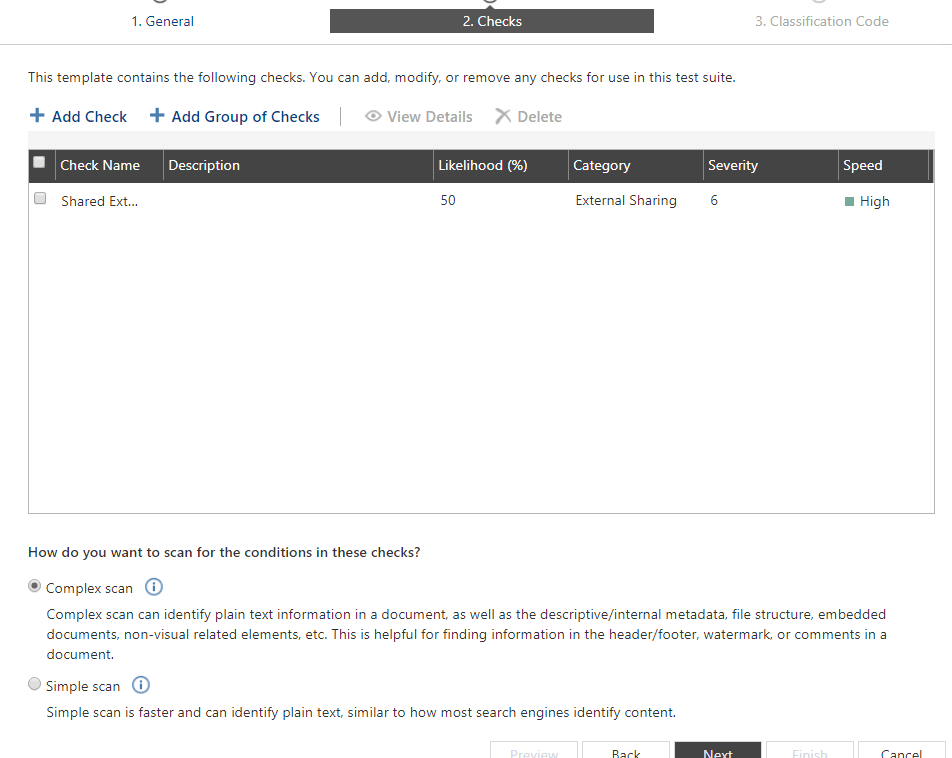
- Next would be to (optionally) configure a classification value which later on can be used to drive the application of automated security controls with Compliance Guardian. Note that you can combine multiple conditions from multiple checks within your Test Suite, thus allowing your security policy to accommodate multiple and various use cases within your environment.
How do we create a Scan Plan in Compliance Guardian?
- Once we save the newly-created Test Suite, we can monitor our data as a scheduled scan, on-demand or in real-time via the Scan Manager. The difference between scheduled and real-time scans is that real-time scans allow plan violations to be identified immediately and thus prevent potential data breaches. Scheduled scan plans, on the other hand, might be a bit too late to prevent a potential data breach depending on how often the scan plan runs.
Another difference is that with scheduled scans, you can benefit discover data that has already been externally or over-exposed whereas, with real-time, it is in effect only for documents created as soon as the real-time scan plan is created. Click Create to start with your Scan Plan configuration.
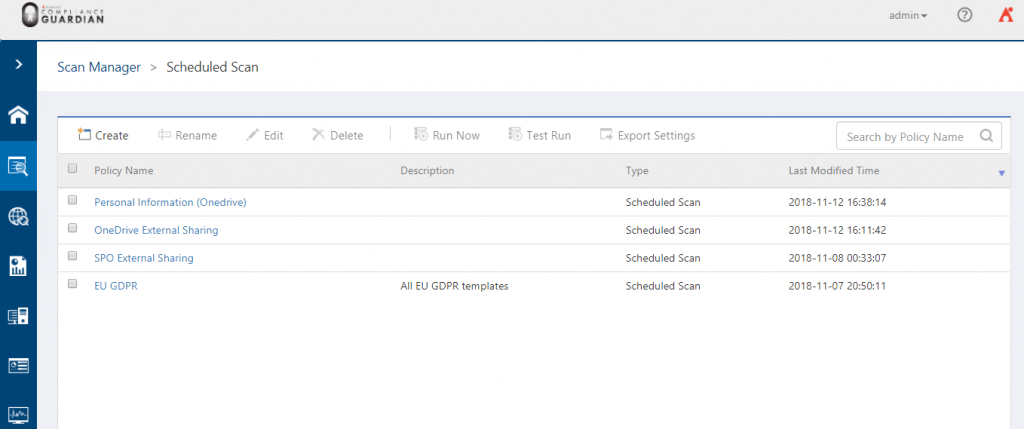
- The first step within a Scan Plan is to select a Test Suite. Click Yes I want to use a test suite and then click Add a Test Suite.
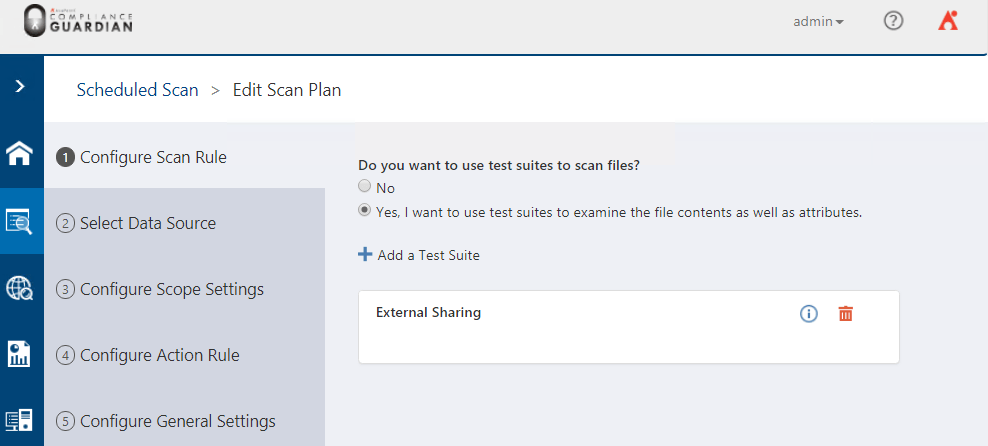
- The next steps are to select the Data Source:
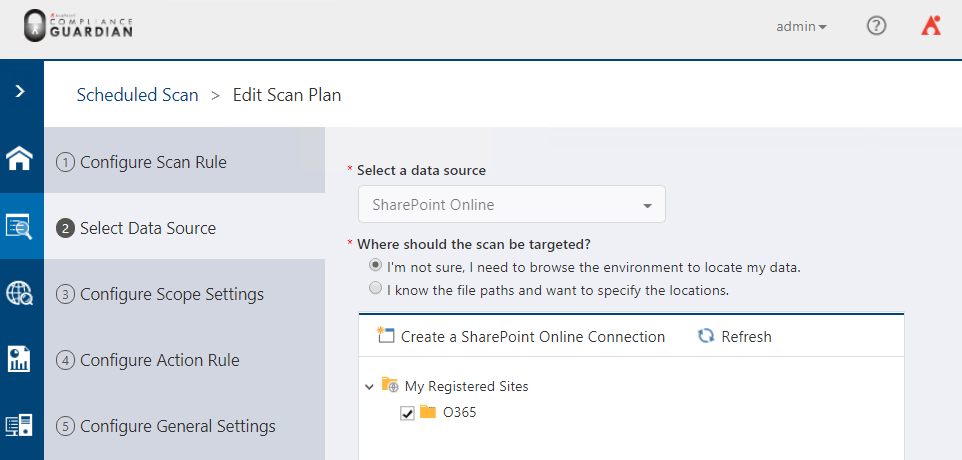
- The Action Rule step is where the benefit of Compliance Guardian comes in. As we mentioned earlier, monitoring and reporting are great, but preventing violations or potential data breaches is even better. Select Yes if you would like to take action. You are then able to build your use case condition and apply one of the many available actions in Compliance Guardian.
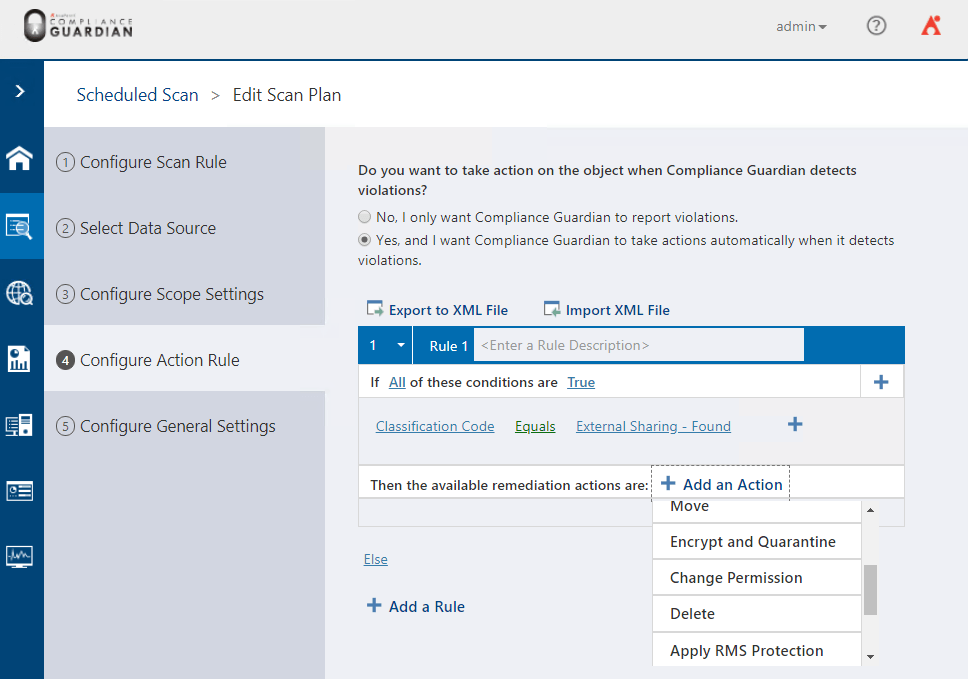
Compliance Guardian can drive Information Access Management policies and one of the methods to remove External Sharing is to Change Permission to the files. You can read more about how to secure external sharing in SharePoint Online, Box, Dropbox and other cloud applications here.
- As soon as you Save and Run the Scan Plan, you can see the progress within the Job Monitor:
Once the Scan Job has finished, we can see the findings from the Incident Management Center > Dashboard:
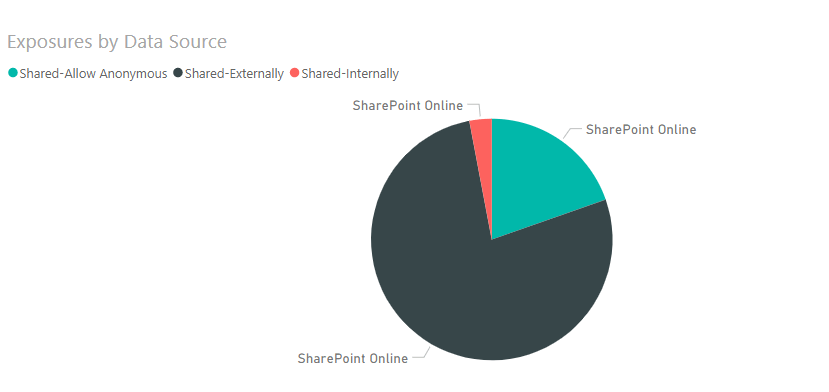
AvePoint Compliance Guardian Sharing Exposure by Data Source
Let’s summarize!
Every organization is sharing files. Whether internal or external, the challenge is the same: how can you protect your data from over-exposure and prevent it from getting in the wrong hands? The ability to monitor and report such potential violations is great, but protecting and preventing them from happening is even better (and will save you from enduring hefty penalties). If you’re interested in learning more about how AvePoint Compliance Solutions can help, click here for more details.
Want more on Office 365 security from industry experts? Subscribe to our blog.

