The business world is a one big community. For an organization to flourish, connections must be made. This means collaboration among agencies and people outside your organization is bound to happen.
While email has been our primary tool for years, productive collaboration with external parties such as vendors, clients, and partners has been made better with platforms such as SharePoint, OneDrive, and Microsoft Teams.
But letting users into your environment can be unnerving—what if your guest users have malicious intent and end up having access to your highly sensitive files?
Luckily, Microsoft 365 allows you to configure your environment to help you control your guests’ actions, identities, and access permissions, and eventually better manage the guests in your tenant.
Here are seven steps you should take if you want a more secure guest sharing environment:
1. Set Up Multi-Factor Authentication
Knowing your guests’ identity is key to ensuring the right person is accessing the right information. But identities can be stolen, so setting up a second factor of authentication for your guests would help reduce not only the chances of an account being compromised but also help prevent unintended parties from gaining access to your files and sites in case a guest account does get hacked.
2. Manage Guest Access Reviews
One common external sharing problem is the issue of knowing when a guest should be removed once the project timeline is at its end.
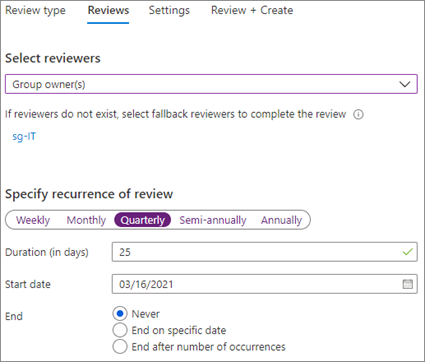
Through guest access reviews, you can have a periodic overview of user access to various Teams and Groups. This way, you can be assured that guests do not have access to your files and sites longer than necessary.
To make things easier, Microsoft encourages creating a dynamic group in Azure AD that will contain all your guests and then create an access review for that group.
3. Configure Session Timeouts
Another way to help ensure that the right person is accessing your sites and files and that your guest is who they say they are is to require them to authenticate on a regular basis.
By configuring session timeouts for guests you can observe if the device and identity accessing your data is secure. Coupled with multi-factor authentication, a stronger identity policy is set up to protect your environment against unwarranted access.
4. Establish Web-Only Access
By applying a policy where guests can only access your files and documents on a web browser, you can reduce the risks of your data being modified without your knowledge. This then secures the authentication of the files that are being shared with people outside your organization.
Microsoft’s Azure AD conditional access policy can help you achieve this.
5. Use Sensitivity Labels
By putting up security labels based on your sensitive information types, you can manage the content specific to your organization.
You can then set up policies on how you can monitor and control these sensitivity labels by utilizing Azure AD’s Data Loss Prevention (DLP). Setting up DLP can prevent the risky sharing of sensitive files as it uses deep content analysis to detect sensitive items.
Additionally, leveraging third-party tools like AvePoint’s Policies & Insights (PI), which also employs Microsoft’s sensitivity labels, can help you better secure your sensitive data by giving you an overview of how it is used by users, alerting you of possible exposure, and acting based on the data for more proactive detection of and protection against malicious actions.
6. Create a Managed Guest Environment
If your partner organization uses Azure Active Directory, you can create a managed guest environment where users can self-enroll in an extranet site or Team and are given access through an approval workflow.
By creating an extranet site, you have an easier method of sharing collaboration resources while effectively managing your user access without placing a heavy burden on your IT department.
To this end, Cloud Governance can also be utilized if you want more secure and automated approval workflows and policy configurations.
7. Manage “Anyone” Links
While it’s extremely advisable to change the default sharing link type to only People in your organization or existing guests, some businesses do prefer to keep the default to Anyone. In those instances, there are additional settings you can set up to better manage your Anyone links and reduce the risks of unauthenticated sharing:
Set Expiration Dates
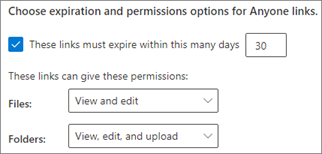
Setting expiration dates to your Anyone links can ensure forgotten and unmonitored guests do not have access to sensitive documents that may be subject to retention policies.
Set View-Only as Default Link Permission
Instead of the default Edit permissions to Anyone links, you can set the default to View permissions. This way, you can allow unauthenticated sharing but prevent unauthenticated people from modifying your organization’s content.
If you want users to edit your document, you can give Edit permissions with the Specific People link type.
Final Thoughts
The key to creating an effective guest sharing environment is understanding that security is as essential as collaboration. As IT leaders, utilizing the tools and resources available to avert the risk of having guest users without compromising both collaboration and security is critical.
By deeply understanding Microsoft’s capabilities and leveraging effective third-party tools like PI and Cloud Governance, internal and external collaboration risks are abated with proactive security measures.

