From migrating organizations on-prem to the cloud, today’s challenges now revolve around building a secure workspace in organizations’ new cloud environments.
For Microsoft 365 users, there are different tools available to develop a security posture for a risk management strategy and scale in the cloud securely. But without the right knowledge on what to protect, customers may find it hard to utilize the tools as best they can.
AvePoint and Ingram recently partnered with Microsoft for a webinar to zoom in on today’s cloud risks and how visibility and swift action can help. Check out the on-demand session here: How Successful MSPs Protect Their Customer’s M365.
Microsoft 365 Insider Risks
When we talk about application security, it’s mostly about building defenses against outside threats such as Multi-Factor Authentication, data security and sensitivity labels.
But some threats come from inside the organization. What makes them even riskier is the fact that it’s more than just malicious employees having access to sensitive information.
Insider risks are the vulnerabilities the cloud-first approach unlocked—as people own their data without thinking of their responsibility towards its security, there’s a bigger gap in what IT teams can manage and have control over.
For Managed Service Providers (MSPs) and security providers, there’s a pressing need to address this issue not only to build trust with customers but also to ultimately incorporate proactive security solutions into your offerings.
So, how do you address this challenge?
Visibility in Microsoft 365
The key thing to remember in building a risk management strategy is that organizations primarily care about how safe their critical data is and what defenses are best used to remediate any issues.
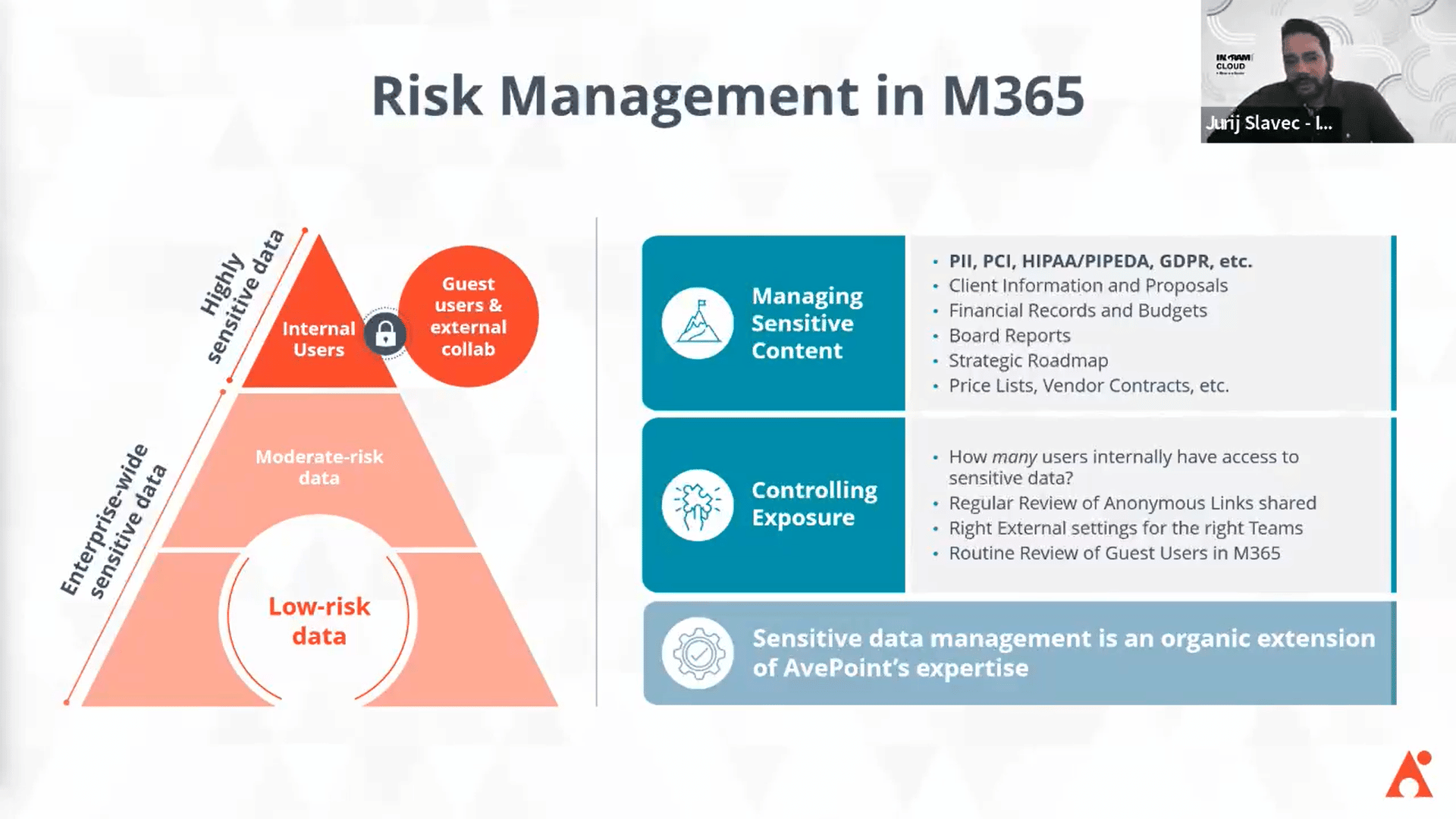
To ensure that, you need complete visibility over every content and data in a Microsoft 365 environment. Achieving that, however, means you need to go through several processes:
- Download DLP reports to help identify what’s sensitive in a Microsoft 365 environment
- Go through your Audit Logs to see what happened for any item in Microsoft 365
- Use PowerShell to assist admins in identifying current permissions
Beyond this, you need to utilize various tools to fix the issues you’ll find. As an MSP, this is an extremely tedious task to do for multiple customers!
Policies and Insights: Automated Visibility and Action
There’s a way to instantly get both a bird’s eye view and zoom in to specific security segments and fix issues with minimum effort.
With Policies and Insights (PI), you can examine all data, remediate security issues, and standardize policies across multiple Microsoft 365 environments to ultimately create the best risk management plan—all in a single dashboard.
a. Automated visibility with Risk Assessment Report
PI’s Risk Assessment Report automates the process of pulling out reports, whether it is specific user violations, shadow users, permissions granted to multiple users, or even who has access to and what actions were done to sensitive data.
In addition, these reports can quickly be transformed into easy-to-understand formats so you can conveniently present them to your customers, all while highlighting the risks specific to their environment and the efficiencies made by your team.
b. Proactive remediation and easy policy enforcement
By automating your policy enforcement, you can ensure a quick fix to your issues, proactively remediate security risks, and enhance access and governance policies.
One of the key security challenges is identifying shadow users or shadow access to your data by external identities. With PI, you have visibility over access to every content and data and then remediate guest or external access issues—like revoking access or labels, removing link access, or resetting your guest lists.
Policy enforcement is also enabled with proper rollouts to ensure good deployments across tenants.
c. Scale by standardizing across tenants
Lastly, with Nitro, you can easily standardize and templatize your security policies across multiple tenants, so you don’t have to create and reapply the same policy to each of your customer’s tenants.
Get all the details in our on-demand webinar!
Watch a live demo of PI’s capabilities by joining the on-demand session of AvePoint and Ingram’s recent webinar!
Check out the session to know how to get started, learn how to introduce the solution to every type of customer, and get a free Enterprise License from AvePoint and Ingram’s experts.


