Ensure your data is secured with our new ebook “Public Sector Cloud-to-Cloud Data Protection for Office 365 and Microsoft Teams!“
This is the 3rd installment in a series addressing the challenges facing the DOD as they move into Microsoft 365. The others are here:
- The DOD’s Cross-Command Telework Platform (CVR) Expires Soon: What’s Next?
- Considerations for Governance in DOD365
- How Teleworking and the CVR Affect Records Management for the DoD/IC
- How to Prepare for Unified Labeling in Microsoft 365 DoD
- Backup & Retention Policies for Microsoft 365: Why the DOD Needs Both
- Smart Data Governance Lessons Worth Learning From the CMMC
- What to Use When for Secure Microsoft 365 Collaboration
Collaborating is Sharing, But Who Can See Your Files?
The cloud is finding a foothold across the Department of Defense. The Air Force has been well on their way with the CHES program, the JELA III contract made Microsoft 365 available to the Army and many of the COCOMs, the Navy added Microsoft 365 licensing SKU’s in their most recent Enterprise Agreement (EA), and the Defense Enterprise Office Solutions (DEOS), is expected to be awarded in a few months.
The COVID-19 pandemic brought a “Teams-only” version of Microsoft CVR, but with the more fully-featured DOD365, the DOD will need to mitigate many previously avoided security risks.

Embracing the cloud has put a lot of security buzz words in play. Vice Admiral Nancy Norton reported that DISA and others in the DOD are working on Zero Trust-referenced architecture. Cloud Access Security Broker (CASB) and Data Loss Prevention (DLP) are also leaders in the security conversation. Clearly, controlling who can access your environment and what they can do with the data continues to be a top priority.
Answering these security questions means that the Generals leading these DOD commands and 4th Estate agencies can have confidence their data is secured without hampering the warfighter’s productivity. However…
If you’re using Microsoft Teams, how do you confirm “Shadow Users” don’t have access to your files?
Shadow Users occur when files in a Team are shared with people who aren’t part of that Team membership. This can happen from SharePoint—which is not currently accessible in the CVR—or from desktop applications like Word and Excel where a SHARE button is built into the ribbon.
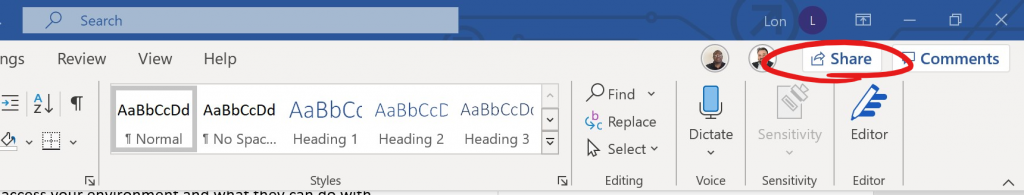
So, is the Teams Membership enough to ensure your data is secure? Can you report on who is accessing potentially high-risk content? What or where IS my high-risk content? What insight do you have into high-exposure data or sites (accessible to large/many groups)?
If you want the CliffsNotes version of this article, the short answer is “No, native tooling does not give you insight into these issues.” CASB, DLP, or Zero Trust ensure only the right users can access your environment, but you still need solutions to ensure the data is used and shared appropriately with users you “trust.”
Why is this such a difficult task?
Microsoft 365 is a construct of various services that work together to provide an easy-to-use solution for the end user. Per the graphic below, chat conversations are in Exchange and their attachments are in OneDrive, but did you notice that Teams conversation attachments go to SharePoint?
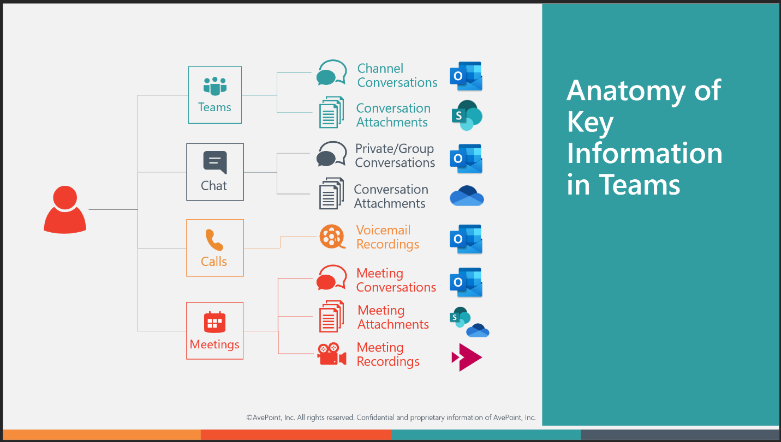
Prior to the release of Teams, these elements of chat (Skype/email) and files (SharePoint/OneDrive) were standalone solutions with their own capabilities for sharing and security. With Microsoft Teams as the overlay, new content and security boundaries must be analyzed to ensure data security.
Let me visualize how this problem quickly escalates and, if you are a CISO, Security/Privacy Officer, or SOC operator, I encourage you to try this yourself as you follow along.
At AvePoint, our US Public Sector Team has five Owners and 93 members for a total of 98 users.
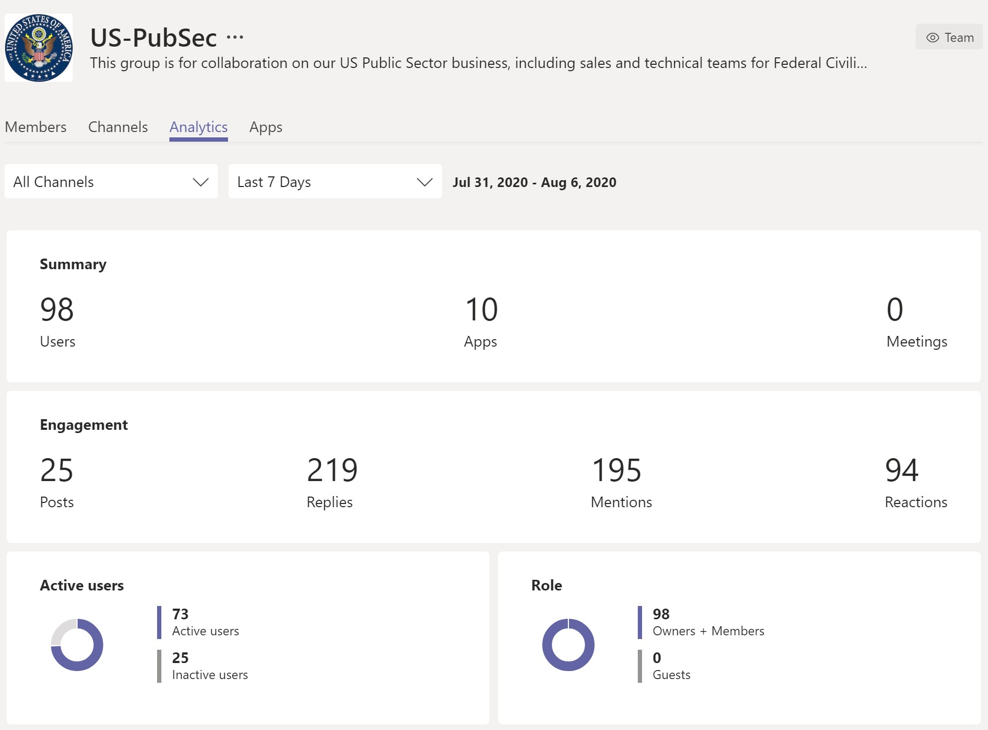
BUT, are these 98 individuals the only people with access to the shared files within this Team?
We know that every Team has a corresponding SharePoint site collection, and by navigating to the one that corresponds with our US-PubSec Team I already see a discrepancy. The US-PubSec Team has 98 users, but the SharePoint site has 106 members.
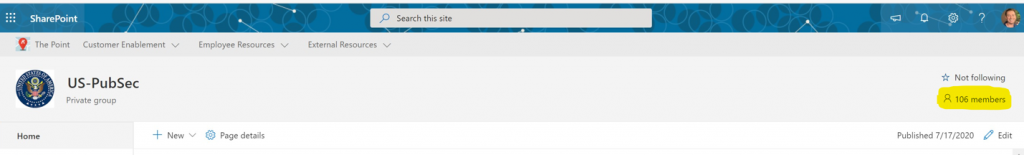
These eight additional users are our Shadow Users referenced earlier
- What can they see?
- Which documents are shared with them?
- Who granted them access?
- What rights/permissions do they have to those documents?
- What have they done in those documents?
- Do they have permission to share with others?
You might be asking, “How did this happen?” or exclaiming, “That’s bad governance/security!” But is it? One could argue that this is the way Microsoft 365 was designed, to be open for collaboration and sharing.
Let’s play out a sample scenario to see how sharing happens in Microsoft 365.
- In the Word Doc: A General is writing a memorandum about an upcoming event and needs to collaborate with his Chief of Staff (CoS) inviting that specific user to collaborate.
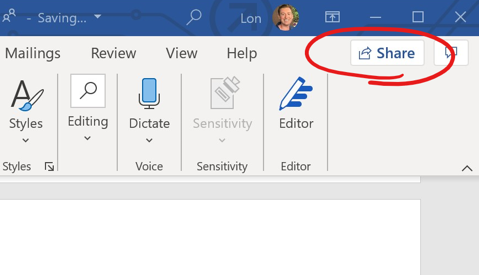
- In the Teams Application: The memo get’s posted to a Channel discussion in the Teams application to coordinate logistics with other members.
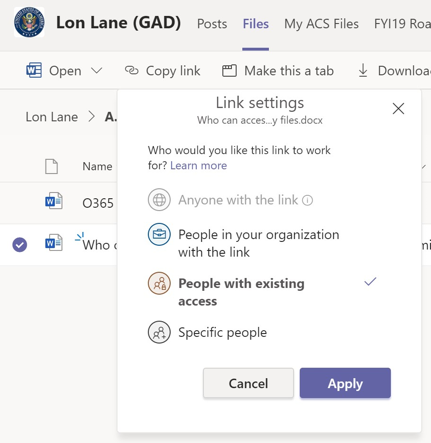
- From SharePoint: The CoS needs to incorporate base logistics and security members as part of this event, but those people aren’t a part of the General’s M365 Team. Since they shouldn’t be invited into the General’s Team, the CoS shares the file through SharePoint.
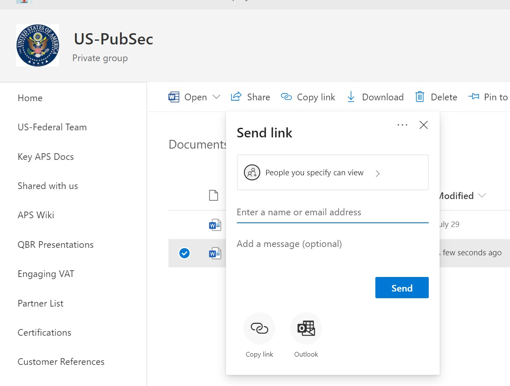
Looking at this sharing example, everything that’s been done is logical by the General and CoS to get work done but this same sharing capability has likely added Shadow Users to the SharePoint Site Collection which won’t be reported to the Team owner.
Searching for who has access
Going back to my challenge, “Who has access to your files?” let’s do some more digging and peel back the onion.
If you’re following along, navigate to a Channel and then to Files. We don’t see a way to know who has access to this file. Thus, I’ll have to navigate to SharePoint…
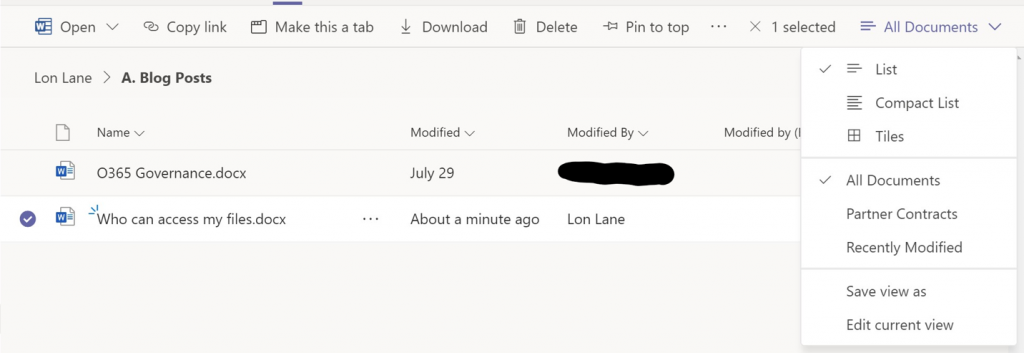
In SharePoint I can see the file permissions, but only the group names. I can’t drill into which members are in these groups.
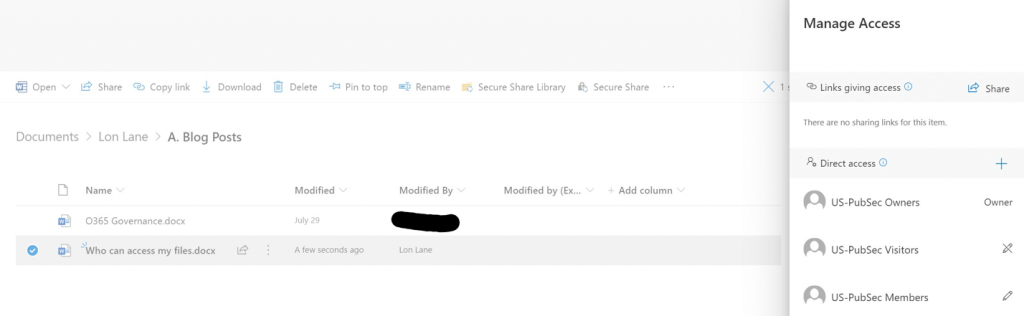
Like me, you’ll need to go file-by-file to view the explicit permissions on each. While most had the same US-PubSec Owners, Members, Visitors, etc., I did start to find files that had explicit permissions. See the example to the below:
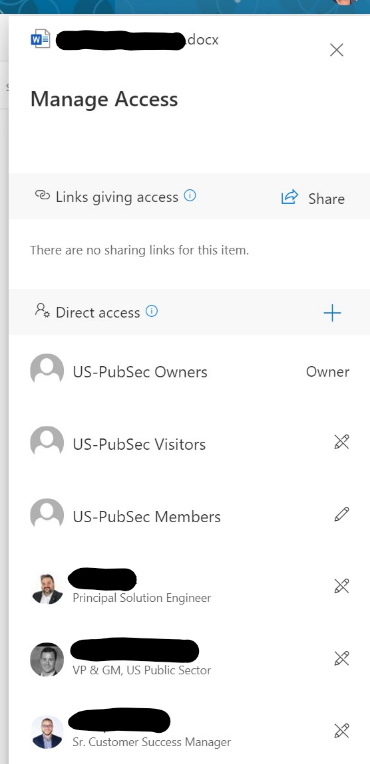
This seems like progress, right!? We’ve successfully reviewed our files. However, it was only within this folder, on this SharePoint site, at this specific point in time. This task was time-consuming, not comprehensive, and only valid for today. Permissions could change tomorrow.
While my example is a review of my personal files, how would a person in a security or privacy role do that for everyone across the command?
Enterprise Management of Access and Risk
AvePoint’s Policy and Insights (PI) for Microsoft 365 is a single pane of glass, providing insight into who has access to files, if the content is sensitive in nature, and the exposure level.
But Insights is only half the battle, and PI’s Policy capability enables operators to see these over-exposed areas, take action within the tool, and create policies that improve the commands’ security posture over time.
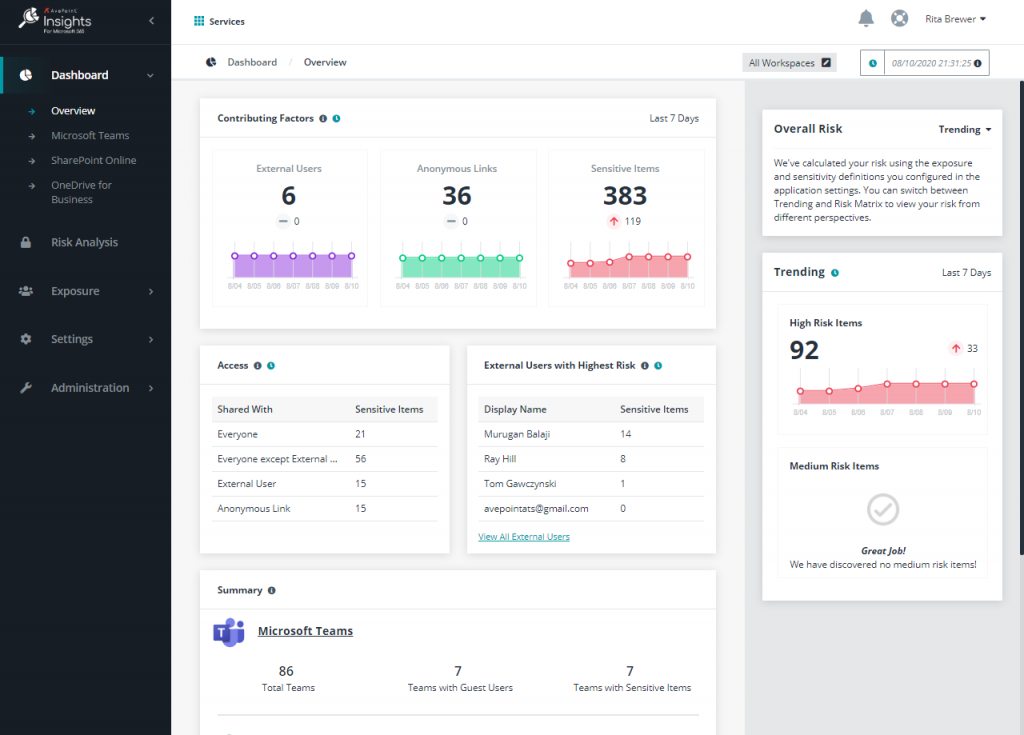
The above Insights Dashboard and related detailed reports are your first step towards understanding your risks and creating policies to proactively mitigate them. This can be done in any collaborative workspace and across multiple tenants.
For example, the ability to see risk across all Teams belonging to a specific command becomes a powerful story in ensuring we write and automate the right policies to keep our data secure. Another capability that blew me away was the ability to search for a specific user and see across all content what that user has access to, what they have done with that access, and where those permissions came from.
Thinking back to the example from AvePoint’s US-PubSec Team, I requested our security team review the reporting in AvePoint Insights and found out that the six user discrepancy so obviously pointed out by SharePoint was actually only the beginning; there are a total of 86 shadow users! Clearly we have some policies that’re in need of review!
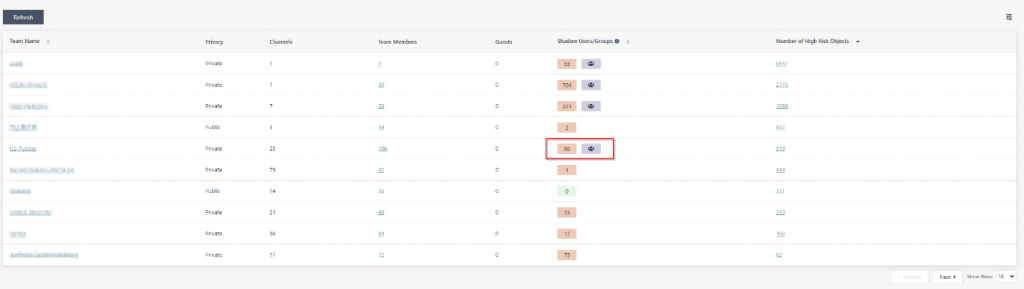
Consider the power in identifying the behavior of a specific risky individual, or seeing explicit permissions and how they break inheritance, or what sites have anonymous links that enable ANY user to see specific sensitive data.
How it works
Permission Caching
PI maintains a near real-time cache of all the objects that have unique permission settings within a selected scope. The scope could be a group of SharePoint sites, a Microsoft 365 tenant, or multiple Microsoft 365 tenants.
This permission caching also enables us to do fast search for users, documents, permission levels, and auditing. For example, I want to know who has “full control” permissions across Sites X, Y, and Z, and then remove users who have unwarranted access.
Exposure Level
PI performs calculations on the backend to identify and highlight exposure. Exposure isn’t merely content in a public place, like a command’s landing page. It can also be large groups or a collection of groups accessing folders or lower-level sites. This calculation can get complex since group membership is constantly in flux and changes can have rippling effects on parent and grandparent groups.

Sensitivity Level
PI leverages Microsoft 365 Sensitive Information Types to identify data that may contain content such as Social Security Numbers, Credit Card Numbers, or other sensitive markers.
Activity Logs
When high-risk data is identified, part of the forensic activity is to trace who had/has access, who used that access, when it occurred, and what actions were taken in the document.
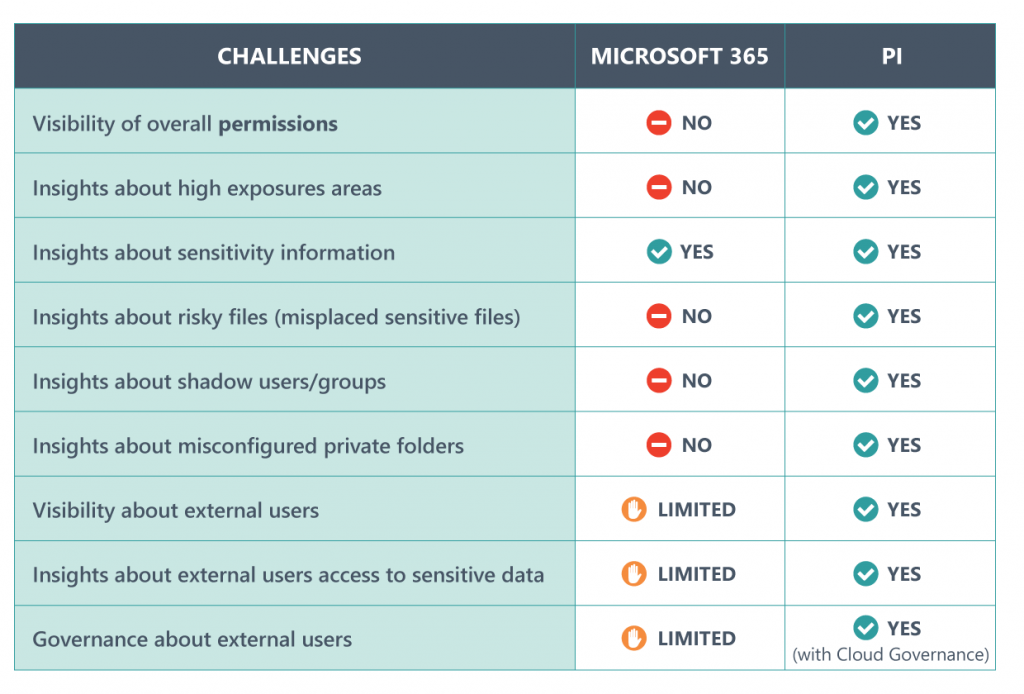
Remember the questions from before about permissions, high exposure areas, and misplaced sensitive files? Here’s a comparison of native reporting versus what PI can do:
In Summary
Security is a multi-faceted operation incorporating networks, devices, applications, identity, and data. We are only as strong/secure as our weakest link, and minimizing data exposure within the network is just as important as securing access to the network.
Together, AvePoint’s Policy and Insights enables you to provide the warfighter with the best capabilities of Microsoft 365, encouraging collaboration and all the while keeping a close eye on their permissions, data exposure, and risk.
Now, let’s try again…“Who has access to your files?”

