Does your agency deal with taxpayer information? Read our free ebook “How To Manage Federal Taxpayer Information In Microsoft Teams” today!
This is the 5th installment in a series addressing the challenges facing the DOD as they move into Microsoft 365. The others are here:
- The DOD’s Cross-Command Telework Platform (CVR) Expires Soon: What’s Next?
- Considerations for Governance in DOD365
- Is Zero Trust Enough to Secure Your Data?
- How Teleworking and the CVR Affect Records Management for the DoD/IC
- Backup & Retention Policies for Microsoft 365: Why the DOD Needs Both
- Smart Data Governance Lessons Worth Learning From the CMMC
- What to Use When for Secure Microsoft 365 Collaboration
The last installment of this blog series addressed the need for proper Records Management within each Department of Defense (DoD) agency, especially as remote work becomes less novel and more commonplace. Metadata mapping, documentation, tagging, and management is critical; however, security must extend governance efforts to ensure compliance after migration. DoD agencies and executive offices are also being asked presently by the Committee on Armed Forces to assess how their internal enterprise cybersecurity hygiene matches up to the new Cybersecurity Maturity Model Certification (CMMC) standards.
Digital Labelling Before and After Migration
Organizations migrating to Microsoft 365 from the Commercial Virtual Remote (CVR) environment or other cloud tenants should develop a labeling strategy for content in the new tenant, but also ensure existing tags and labels are not lost in the process. A grave concern many agencies face today is not the loss of content as much as it is the loss of security during the transition. Specifically, a file or file set previously accessible to a handful of select individuals could gain default permissions and configurations upon migration – leaving the file or file set vulnerable to far greater access or export.

Digital labeling is a growing complexity in modern organizations and stretches previous physical media requirements, whereas protections and policies have been in place and largely followed amongst the DoD for nearly a century. Physical media requires specific labels be applied to printed documents, storage devices (USB, CD, etc.), and more. The lifecycle and possible export scenarios of data in the cloud are far more complex and practically countless.
In Office 365 alone—or Microsoft 365—a user can share a file from OneNote, SharePoint, OneDrive, and Microsoft Teams or accidently display Controlled Unclassified Information (CUI) via a PowerBI dashboard, for example. Third-party and native tools exist to remedy these scenarios and require additional strategy discussions.
For instance, CUI will require drastically different labeling and protections than classified data or Federal Contract Information (FCI). Your organization needs to define a plan for each data type in Microsoft 365:
- What will users need to access this data type? What Microsoft Groups and Teams do these users align with?
- Where will users access this data type and on what devices or endpoints?
- Must we log interactions with this data type?
- What retention standards apply to this data type?
Unified Labeling in Microsoft 365
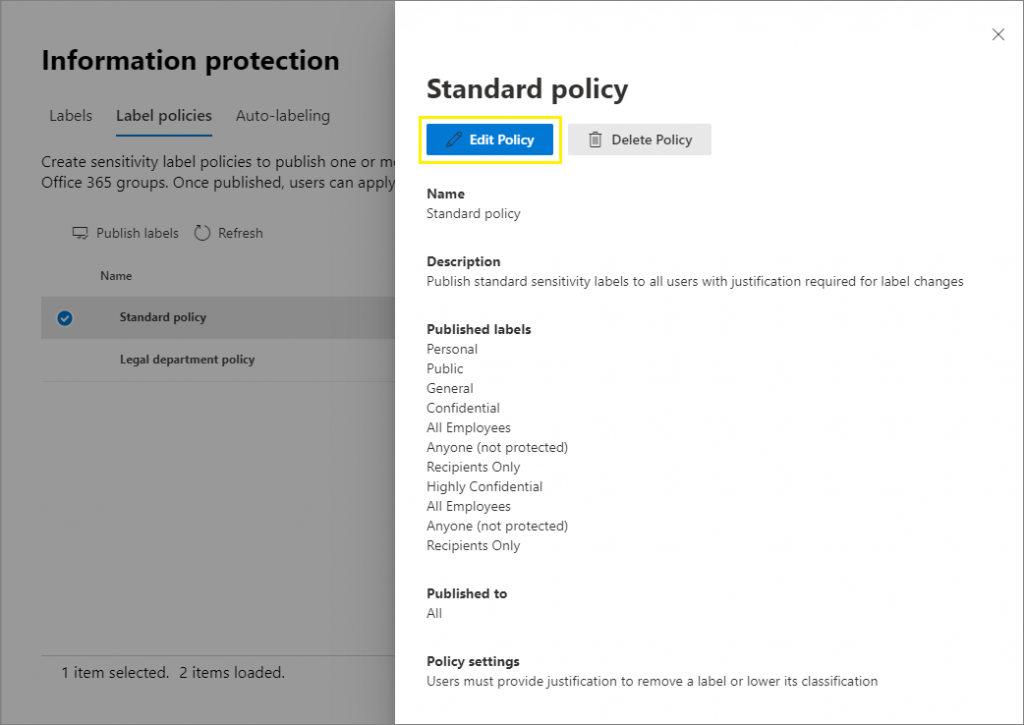
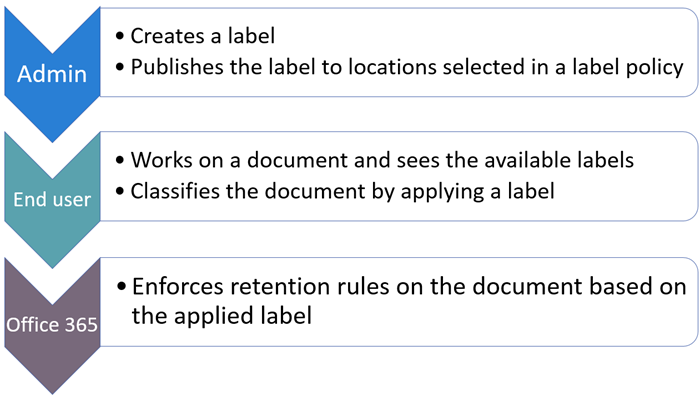
For modern agencies, long gone are the days where files were maintained behind firewalls or site/folder-level permissions served as the frontline of defense for data protection. These questions above and the resulting requirements will drive your Unified Labeling policies to protect data as it traverses cloud applications and platforms. Unified Labeling is the Microsoft 365 and Azure native suite of digital tagging tools consisting of Azure Information Protection (AIP), Microsoft 365 Retention, and Sensitivity Labels. AIP previously served as the engine for labeling in Microsoft 365 GCC High and DoD but is now rolling into the Unified Labeling client this year.
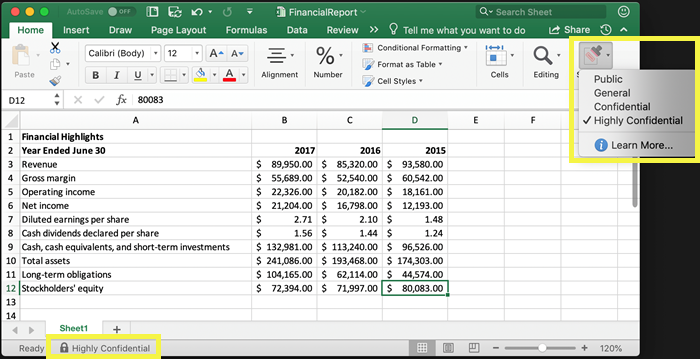
Organizations can create and apply sensitivity labels to files from the Unified Labeling client and many other native locations, such as SharePoint or OneDrive. Once a sensitivity label is applied to a specific file, the file can be automatically encrypted and watermarked, and limitations can be set on access. A labeled file contains specific metadata that is then used by other powerful products in the Microsoft 365 and Azure stack like Data Loss Prevention (DLP) to prevent accidental or malicious transmission of sensitive content.
This capability directly ties into agency-wide requirements found in NIST 800-53 and elsewhere. As an example, NIST 800-53 states that a “subject that has been granted access to information is constrained from passing the information to unauthorized subjects… changing one or more security attributes on subjects… [and] granting its privileges to other subjects.”
DoD regulations require the application of sensitivity labels to ensure the right individuals can access the right files or data at the right time, but those variables can change. What may be appropriate for one individual presently may not be appropriate for viewing or editing after some time. Additionally, users may gain or lose elevated privileges in an organization as restructuring occurs or new projects spin up. Therefore, modern document or data management focuses on item-level security and proper identity management through the use of Microsoft 365 Groups and proper Azure Active Directory configurations.
Preparing for Unified Labeling in Microsoft 365 DoD
DoD Agencies and respective Offices should map their varying access control scenarios to data types and determine how they will apply sensitivity labels and/or third-party tagging technologies. As of this writing, a user or administrator can apply a single sensitivity label to a file—not multiple. Some organizations may operate without the need for multi-label scenarios; however, many DoD agencies communicate and collaborate around data with several layers of control. A single file may contain CUI-General, FOUO, FOIA, export control, PII, and personnel records. As such, a subset of users may be permitted to access CUI but do not need to access to CUI containing financial or personnel records.
Another consideration for agencies looking to deploy Unified Labeling in Microsoft 365 DoD is feature parity, or the availability of certain capabilities compared to the commercially available platform. The DoD recently announced the JEDI contract award to Microsoft after several rounds of arduous protests, and this contract and eventual cloud rollout serve as a sign of optimism for feature parity.
Have questions about labeling in M365 DoD? Check out this post: Click To TweetMicrosoft will be responsible for releasing features to Microsoft 365 GCC, GCC High, and DoD within a short time period after making them Generally Available (GA) in the Commercial platform offering. As of this writing, the limitations of Unified Labeling and AIP specifically are listed below according to Microsoft’s documentation.
- Document tracking and revocation are currently not available.
- The classification and labeling add-in are only supported for Microsoft 365 Apps (version 9126.1001 or higher). Office 2010, Office 2013, and other Office 2016 versions are not supported.
- Information Rights Management (IRM) is supported only for Microsoft 365 Apps (version 9126.1001 or higher). Office 2010, Office 2013, and other Office 2016 versions are not supported.
- Sharing of protected documents and emails to users in the commercial cloud is not currently available. Includes Microsoft 365 Apps users in the commercial cloud, non-Microsoft 365 Apps users in the commercial cloud, and users with an RMS for Individuals license.
- Information Rights Management with SharePoint Online (IRM-protected sites and libraries) is currently not available.
- The Rights Management Connector is currently not available.
- The Mobile Device Extension for AD RMS is currently not available.
Lastly, define the new labels necessary for your command’s enterprise and what individuals in your organization can create custom labels. Default labels, shown below, will likely fall short and require adjustments or additions:
- Personal
- Public
- General
- Confidential
- Highly confidential
Your Next Greatest Export Risk is Digital
A perception persists that users are now more apt or capable of sharing files outside of the organization during this new normal. However, prior to the pandemic, many DoD IT leaders could not provide complete details on the whereabouts or digital lifecycle of a sensitive document when asked (who created the file and where, who has accessed the file since origination, when and where was it accessed, and what changes were made along the way if any).
Commands transitioning to Microsoft 365 must rely on Microsoft’s native capabilities and other third-party applications to secure the digital lifecycle of a file at every point along the way and fully monitor export controls for compliance and national security.