Last week’s Google Docs phishing scam went viral on social media and gained even more attention by fooling more tech-savvy users to click on links.
The scam was very sophisticated – the email invites the recipient to access a Google Document from a person in their contact list or someone they might know. Once they click on the link, it directs them to a Google.com URL which looks like a sign-in page, but it actually asks permission to access your Google account. If you agree and click Allow, then the attack extends to all of your email contacts and repeats the cycle in order to make a bigger impact.
Luckily, Google was brilliantly efficient in identifying the scam and preventing it from spreading in less than an hour. Even though Google said that only 0.1 percent of their customers might have been affected, that’s roughly 1 million users in less than an hour.
What really got my attention was that social media users were more focused on the details of the scam and how to minimize the risk in case you were affected by this Google Docs scam – but not really emphasizing how to avoid future similar scam efforts.
Let’s quickly review the definitions of phishing and spear phishing:
Phishing is the practice of sending out emails that purport to be from a well-known source, such as a major bank or utility provider. Spear phishing is a more targeted version of phishing. Emails will address you by name and may appear to come from someone senior within your organization.
In most cases of phishing or spear phishing, an email asks you to provide your credit card and PIN, social security number, and passwords in order to verify you. However, banks and service providers will never ask for such details – at least, they’re not supposed to.
How do cyber attacks work?
This is how targeted hacking attacks work:
Are people cybersecurity’s weakest link?
A 2016 investigation of user behavior from Friedrich-Alexander University (FAU) researchers reported that almost every other person, or up to 56 percent of email recipients and 40 percent of Facebook users, would click on a link from an unknown sender. We’ve heard many times that “people are cybersecurity’s weakest link,” and it all starts from human curiosity or simple negligence.
What would the results be if you conducted a similar impact analysis or assessment within your organization? Do you have a way to automate privacy and security by design? Do you conduct periodic user awareness programs in order to avoid or limit incidents such as phishing?
As a former Chief Information Security Officer, I can definitely say that user awareness programs and periodic impact assessments help organizations to see the gaps or the missing links between people, processes, and technology.
Practical Tips for Protecting Yourself
No strategy is bulletproof, but here are a few basic tips for you and your users to follow to avoid becoming victim to one of these nasty attacks:
- At all costs, avoid clicking on links within emails that are from unverified sources, request that you log in, provide sensitive information, or request permissions and access to applications and other sensitive data.
- Always open a new tab or browser, visit the online service, and log in manually
- If you receive an email from a trusted source like a family member, reach out to them directly and verify if they sent it.
- It’s not only important to protect yourself. This could be an important step in making someone else aware that they’ve been compromised.
- Use multi-factor authentication (MFA) wherever possible. Even if your username and password are compromised, that additional verification layer may save you the headache and give you enough time to recover and reset your account. Most services now offer some form of MFA, whether it’s a security code sent to your phone, an app running on your device, or a token generator.
- Use strong and complicated answers to security questions that are sometimes essential to recovering your account. For questions like “What is the name of your pet?” be very careful that information like this is not publicly accessible on private or professional social networks. It can be very easy to get educational information via LinkedIn or learn about your pets and loved ones via Facebook and Instagram.
- One recommendation is to use an obscure and complex password or phrase completely unrelated to the security question. Your dog or cat won’t take it personally that your favorite pet is “1Fjiowprio34$.”
Simplify User Training with Privacy Impact Assessments
The International Association of Privacy Professionals (IAPP) distributes the AvePoint Privacy Impact Assessment (APIA), a free solution that helps organizations understand and automate the process of evaluating, assessing, and reporting on the privacy implications of their enterprise IT systems. With APIA, organizations can conduct Privacy Impact Assessments (PIAs) and introduce privacy and security by design, but also utilize the built-in workflow engine and form-based survey system with configurable questions to simplify training or deploy user awareness programs.
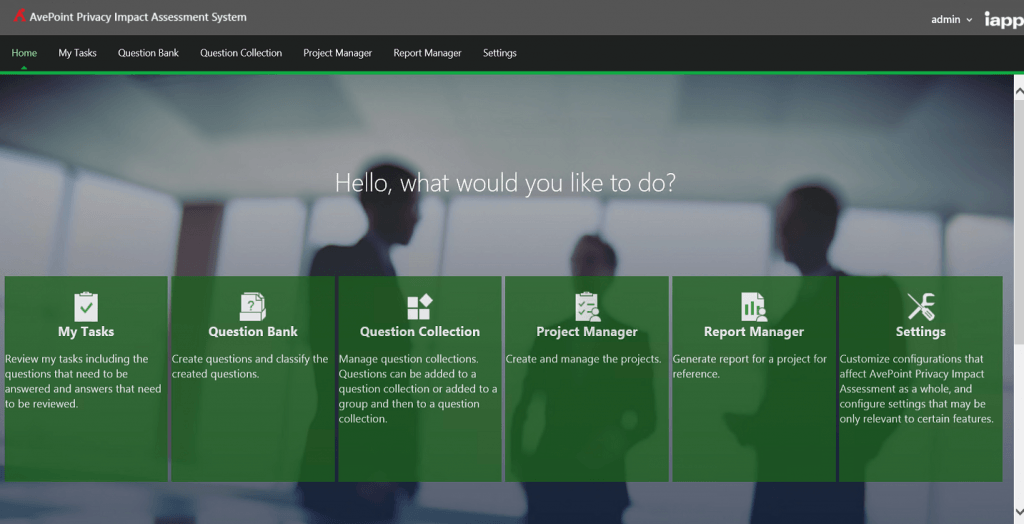
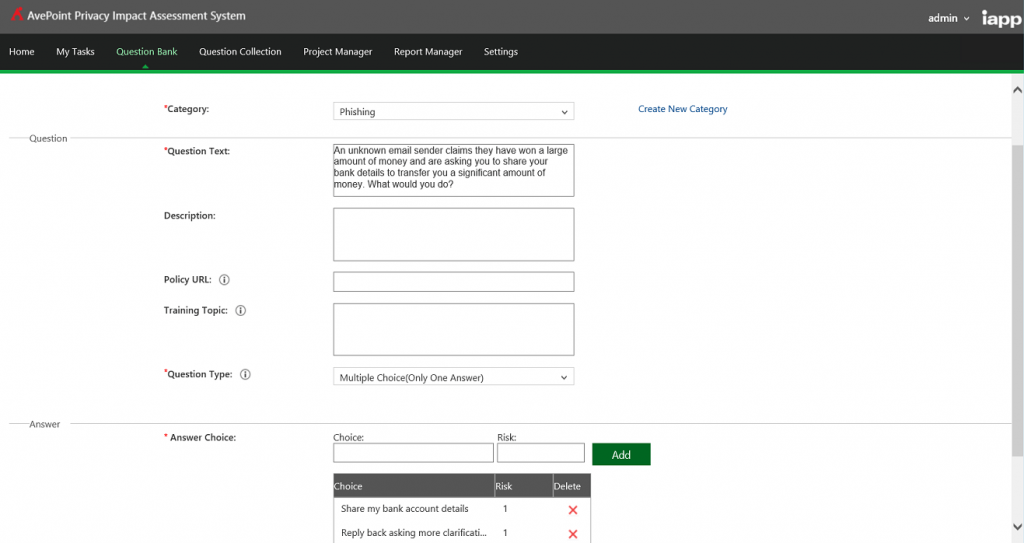
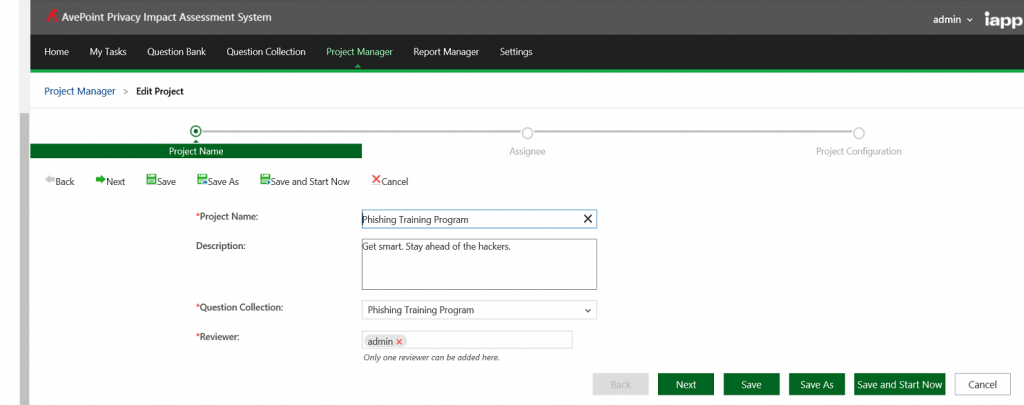
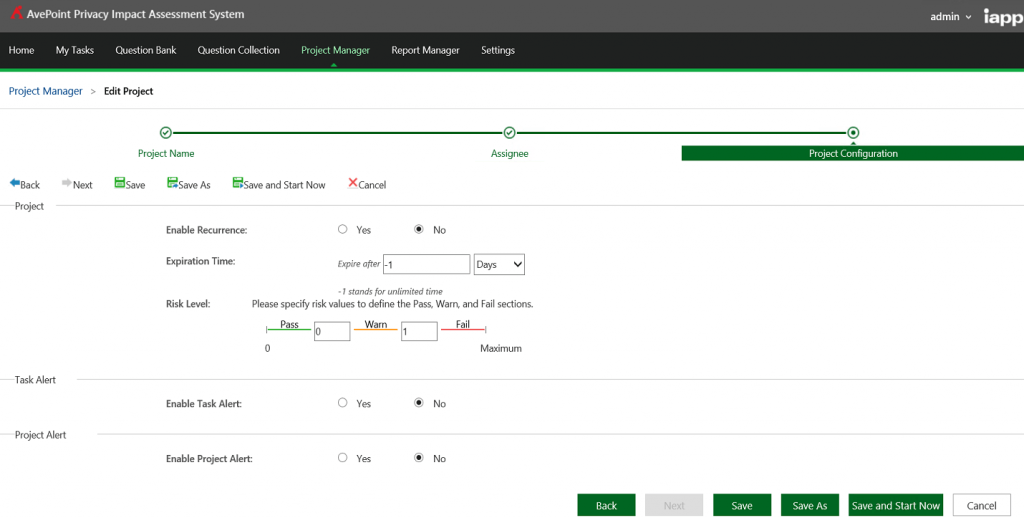
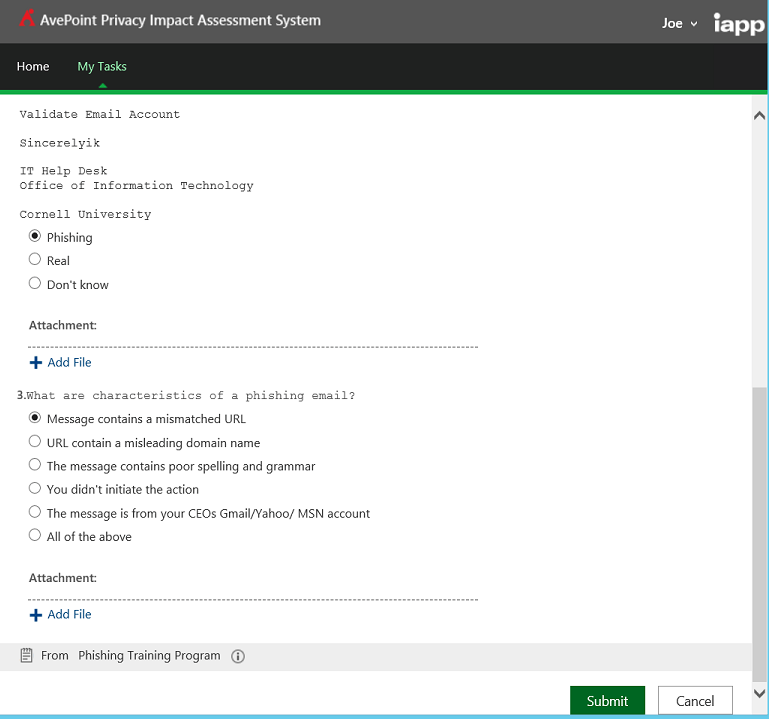
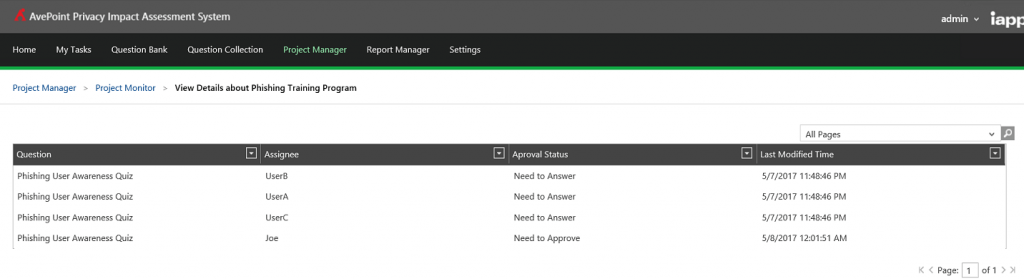
Organizations can benefit from APIA’s flexibility to extend beyond just automating PIAs. It can also help Information Security Officers or Human Resources Managers to get even more value by allowing them to implement survey-based questionnaires to avoid incidents or a phishing scam. In the case of the Google Doc phishing scam, it took Google less than an hour to quarantine, but not every organization has Google’s engineers or expertise – or even the technology required to react and prevent future incidents in less than an hour.
If your organization has a similar incident, what would be the time to react and prevent this type of an incident? Do your employees know how to spot and prevent a phishing scam? Do you invest in training your employees to prevent your business or customer data falling in the wrong hands? Download APIA today to get started.

