Need help meeting the impending 2019 NARA deadline? Download our NARA Compliance Resource Kit!
Over 80% of all Federal agencies use Microsoft Office 365, Azure, and collaboration products such as SharePoint, Yammer, and Teams to serve its thousands of employees and contractors. Office 365 has many benefits including enhanced security, mobility, and reporting, but how can you be sure that you stay compliant and protect information that would be of concern during an OIG audit?
In this article, we will discuss how to set up Office 365 security and governance features to ensure your Office 365 tenant will hold up against an OIG (Office of Inspector General) audit.

Microsoft Office 365 and Federal Agencies
Over the years Microsoft has worked with Federal agencies and contractors to ensure its government cloud services, Azure Government, Office 365 U.S. Government, and Dynamics 365 Government meet the demanding requirements of the US Federal Risk and Authorization Management Program (FedRAMP), enabling U.S. federal agencies to benefit from the cost savings and rigorous security of the Microsoft Cloud. What makes Microsoft 365 Government unique is that its entire infrastructure has been created from the ground up just for its Federal customers. This is important when considering leakage and data breaches, both of which would be of concern for the OIG.
Currently, Microsoft has three plans to assist your Federal agency with government-specific regulations, data security, and privacy. Ensuring users don’t upload information that causes concern for your OIG audit is of the utmost importance.
Microsoft’s Federal Office 365 Plans are as follows:
- Government Community Cloud (GCC) – This was built with civilian agencies in mind.
- GCC High – This was built to store highly sensitive information, and is available to both DOD employees and DOD contractors.
- DoD Cloud – This was built for the armed forces and the agencies it works with.

What is the Office of Inspector General (OIG)?
The OIG was established by act of Congress in 1976 first under HHS to provide Federal and state oversight. Today, there are over 73 offices containing 430 departments, agencies, and sub-agencies. From its early days, the OIG’s mission has always been to fight waste, fraud, and abuse. With the rise of SaaS (Software as a Service), PaaS (Platform as a Service) and IaaS (Infrastructure as a Service), the OIG has ramped up enforcement to ensure Federal agencies and Federal contractors that transmit Federal government Controlled Unclassified Information (CUI) are following policies set by NIST, such as SP 800-171.
What will be examined during an OIG Audit:
Management of PII
The SEC was recently audited by the OIG, and the SEC was found to have not stored PII information correctly. This included names, addresses, birthdates, and account information. From the audit report:
“In addition, in at least five instances, agency personnel had not enforced contract requirements related to safeguarding personally identifiable information (PII) even though experts had access to PII, including investors’ names, addresses, dates of birth, and customer account information. We also found that contracts lacked controls regarding the inadvertent release or disclosure of information after the SEC transmits information to experts. As a result, the agency lacked assurance that experts and their information systems achieved basic levels of security to protect the SEC’s sensitive, non-public information, including PII. We did not identify instances in which unauthorized individuals accessed such information after it was provided to experts. However, the agency should take steps to minimize the risk of unauthorized disclosure, modification, and use of its sensitive, non-public information provided to experts.”
PII management has always been a concern for agencies. Having the proper compliance management features turned on in Office 365 will help you scan, monitor and control who has access to PII information and mitigate and prevent PII leaks.

Multi-Factor Authentication
Office 365 comes built-in with NIST grade multi-factor authentication, which is adequate in most cases. Multifactor authentication—in combination with Personal Identity Verification (PIV) cards—can decrease the load on your helpdesk and add an additional layer of protection.
The deadline for all Federal agencies to have PIV integrated with their physical and information infrastructure is June 30, 2024. NIST’s handy guidance on the best way to implement PIV cards with your correct infrastructure is referred to as the “Federal Information Processing Standard (FIPS) Publication 140-2” or FIPS for short.
The OIG has a low tolerance for agencies and organizations that don’t protect their data with multi-factor authentication. In a recent audit of the DOE’s system, the OIG stated:
“The weaknesses identified occurred, in part, because officials had not fully planned for implementation of multifactor authentication on information systems. Department guidance and requirements related to multifactor authentication technologies also were not always communicated effectively. Without development and implementation of a Department-wide multifactor authentication process, the Department’s information, including sensitive data, will continue to be at a higher-than-necessary risk of compromise. We have made recommendations that, if fully implemented, should help the Department enhance its cybersecurity posture through effective implementation of multifactor authentication. Management concurred with the report’s recommendations and indicated that corrective actions had been initiated or were planned to address the issues identified in the report.”
To ensure your agency doesn’t run into the same issues, work with your agency’s FSO (Federal Security Officer) and information office on developing a roadmap for implementing multifactor authentication.

Retention Policy
Depending on your agency and the regulations you’re required to follow, you’ll have different retention schedules for emails, financial statements, voicemails, drafts of memoranda, and documents. This can be a heavy lift if documents and emails have not been tagged correctly or if metadata has not been used. The best way to organize and label your content is to work with your agency’s compliance officer and review the current procedure for retention rules. Office 365 has an extensive setup for retention rules that can run enterprise-wide.
For example, let’s say users are storing documents in multiple SharePoint libraries that should be part of a seven-year retention rule. Office 365 has the ability to search for and find such documents and place them in a multi-level Recycle Bin after the retention period. It’s best to work with your compliance office and Office 365 administrators to ensure all retention rules are active and being followed.
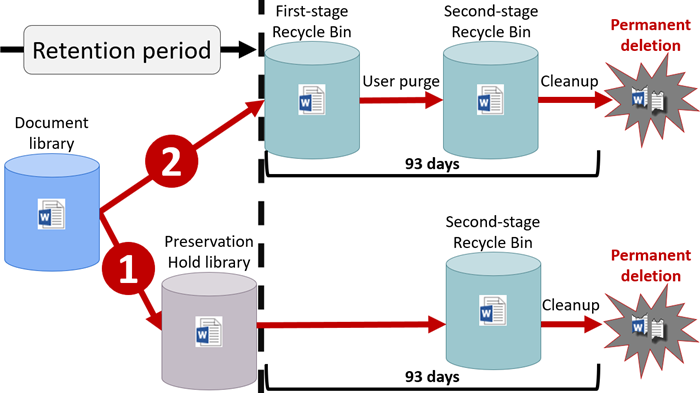
Turning on Office 365 Audit and Security Features
Office 365 does not come with audit and security features turned on; by default, the features are off and must be set up by your Office 365 administration team. Before turning activating those features, be sure to work with the security and compliance office to create a security plan specifically for Office 365.
The best way to start using Office 365 audit and security features is to conduct tests on one department or division at a time. It can be overwhelming to turn on security features across your entire organization all at once. In the end, Office 365 audit and security come down to your agency’s unique policy.
Final Thoughts
OIG audits can be frustrating, time-consuming, and resource-intensive. In most cases, the OIG will schedule an on-site follow-up to ensure all violations have been addressed. The best way to pass your OIG audit is to prepare your organization’s Office 365 tenant and conduct your own internal audits.




