Earlier this year, Microsoft Teams surpassed 270 million active users, meaning that if your customers did not use Teams before the COVID-19 pandemic, they likely are now. With this surge in usage comes an increasing demand from your clients to collaborate with individuals outside their organization by allowing external access.
As a managed service provider, you may be wondering how you can protect your customers’ environment without hindering their collaboration, or if there are any services or tools that can enable external users to safely participate in your customer’s Microsoft 365 (M365) tenant.
Fortunately, Microsoft does offer a variety of services that protect your customers’ external collaboration. As an MSP, it is your responsibility to work with your clients to set basic policies while configuring their M365 to enable access to outsiders. While there are many ways to develop and tailor the appropriate policies to your customers’ unique needs at a granular level, here are a few of the most important top-line considerations to discuss with them.

Who should be allowed to be invited as a guest?
Determine if the agility, regulatory, and sensitivity levels of your customer’s work environment are more appropriate for a policy that is “everyone except” or a policy that is “no one except” those from specific organizations or domains.
Once you work with your customers to make that determination, coordinate with your customer’s business stakeholders to either build a list of common collaborators (such as vendors) to whitelist or to identify organizations that may need to be blacklisted (such as competitors).
In general, highly regulated and sensitive environments will want to deploy a “no one except” policy while most organizations will want to deploy an “everyone except” policy while layering on more protections for specific workspaces and files downstream.
Should guests be allowed to see the organizational directory?
In most cases, it would be inappropriate for guests to be able to look up or contact anyone within your customer’s organization. The best practice is to limit access to those who are members of the same Team as the guest.
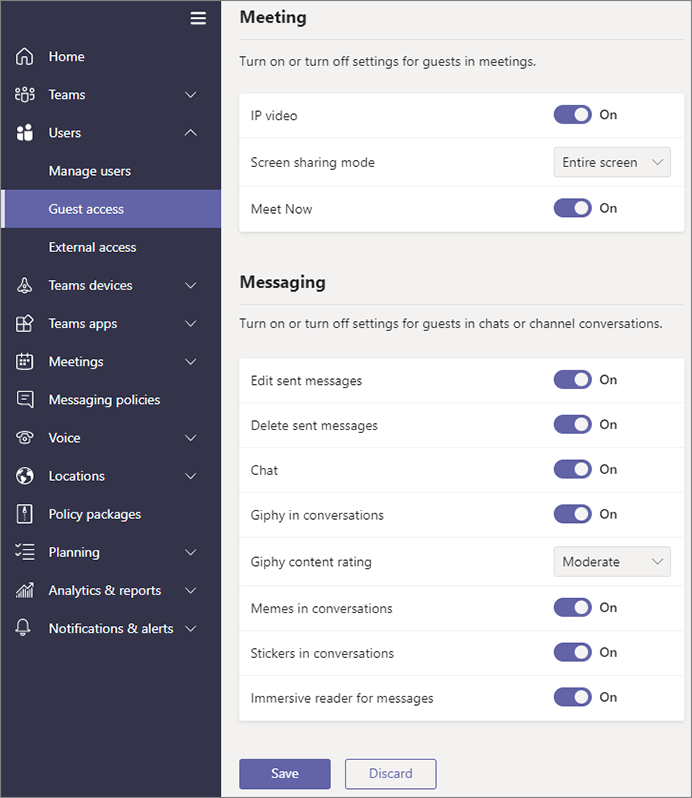
Who should be allowed to admit new guests to the Microsoft Teams environment?
When a user would like to have a guest added, there needs to be a process for admitting them into the environment. There are two people who can add an external user to a Team using Microsoft 365 native functionality: an IT admin or the Owner of the Team.
M365 will never let a member of a Team invite a net new external guest. Depending on the selected settings, however, members could add and share with guests who are already in Active Directory but are not members of the specific Team.
The challenge with having only IT admins add new guest users is that it creates a bottleneck. They’re also not as close to the business needs, so managing the lifecycle of a guest – when they need to be onboarded and offboarded – can be challenging.
On the other hand, not every organization is comfortable with enabling any Team Owner to admit new guests, which then presents two options: Enable Team Owners to invite guests and then lock down specific Teams where sensitive work is being done (which would require coding through Powershell or configuring sensitivity labels), or deploy a third-party solution such as AvePoint’s Cloud Governance to enable an approval process for admitting guests.
How will guest users be offboarded from M365?
Just like in real life, lingering guests can ruin the party. The reason for their invitation could no longer be relevant or the Team they were a part of was disbanded. But without an admin actively taking the step to remove them from Azure AD, those guests still have access to your customer’s environment. At this point, all it takes is for someone in your organization to accidentally invite the wrong “Bob Smith” to a Team with sensitive information, and viola: you have a data breach.
The challenge is that while Microsoft 365 offers an automated way for Team owners to request guests be added to the environment, it doesn’t offer an automated way for anyone within the business to require they be removed from Active Directory.
Here’s the catch: An AAD P2 license provides Azure AD Access review functionality, but that will only prompt Group owners to review and remove guests from their Groups on a periodic basis – NOT the directory. Veteran admins know this means a flood of IT tickets in the best-case scenario (and a cluttered and unsecured Active Directory the worst).
Bottom Line
The reality is modern organizations don’t do everything alone; they rely on networks of outsiders to perform and execute various work tasks. Sharing with outsiders isn’t a new idea, even though the mechanisms for doing so are changing. Using email to send documents to anyone has been a mainstay of business for decades, even though security controls are significantly lacking. Unless their email is disabled, your customer’s users are sharing externally.
Take control of this sharing in three easy steps:
- Ask the right questions
- Set appropriate policies
- Centralize external collaboration in Microsoft Teams
For more policy considerations, external collaboration best practices, and a step-by-step guide on how to configure specific settings to meet your customers’ needs, read our free eBook External Sharing and Guest User Access in Microsoft 365 and Teams.

