The first time an organization comes face to face with risky content is usually unpleasant. In the best case scenario, someone within the organization may find confidential information within a SharePoint search result and reports it to the proper teams to have it removed. In the worst case, it is an auditor or regulatory agency who finds it, or the user in the previous scenario shares the information with someone who shouldn’t have access to it. From there, risk can quickly escalate to a national news story.
We find what is common in all scenarios is that when an organization begins to identify risk, they end up finding a lot of it. It does not matter what the size of the organization or industry, everyone has this issue. Violations are plentiful in SharePoint, file shares, websites, databases, and social environments. In fact, they are often so plentiful, that dealing with the violations can quickly become overwhelming and seem insurmountable.
What is important to consider is that risk at your organization is not owned by any one individual or department. It may fall to a specific person or team to identify risk, but the responsibility and management of it is a group effort. Key questions to resolve are:
- Can we accurately identify risk in our environment?
- How long does it take to get from identifying risk to resolving it?
- How can we process a large number of violations efficiently?
The complexity of setting this up can be daunting. There are three dynamic variables when assessing content and assigning violations for human review:
- Scope answers the question of where is the content (SharePoint, file shares, Yammer, etc.), which will let us know what kind of workloads it is supporting and level of governance applied to it.
- Permissions answers the question of who has control of and access to the content and whether that is appropriate or not.
- Content answers the question of what is actually in the file and if it is sensitive or needs special considerations.
Each document, item, version, page, record, and instant message has an ideal state based on these three criteria and the potential to become a violation if any of them are changed. For example, a document containing personally identifiable information (PII) can be safely stored in a SharePoint library with restricted permissions. But if the scope of that file changes to a personal share drive, for example, it becomes a violation and needs to be recorded and managed as a compliance incident.
Available now, the latest release of AvePoint Compliance Guardian helps you automate incident management processes by providing designated users with a manageable set of tasks to perform. AvePoint Compliance Guardian can:
- Scan the content and identify indicators of risk within
- Weigh the amount risk to prioritize handling the most severe violations first
- Isolate a potential violation either permanently or until the content owner can verify and resolve the compliance incident
- Track who is impacted by this content and what their role is
With this information, AvePoint Compliance Guardian can then delegate the responsibility of incident management to the correct content owners by providing them a prioritized, manageable list of tasks. This way, risk management is handled by the most effective and knowledgeable resources and compliance becomes a group effort where everyone holds responsibility for their content.
Below I will share a scenario that shows how AvePoint Compliance Guardian simplifies incident management through its unified risk management platform.
Incident Management in Action with AvePoint Compliance Guardian
Jill is an accountant working on documents in the Accounting department SharePoint site. She uploads a support document for her project:
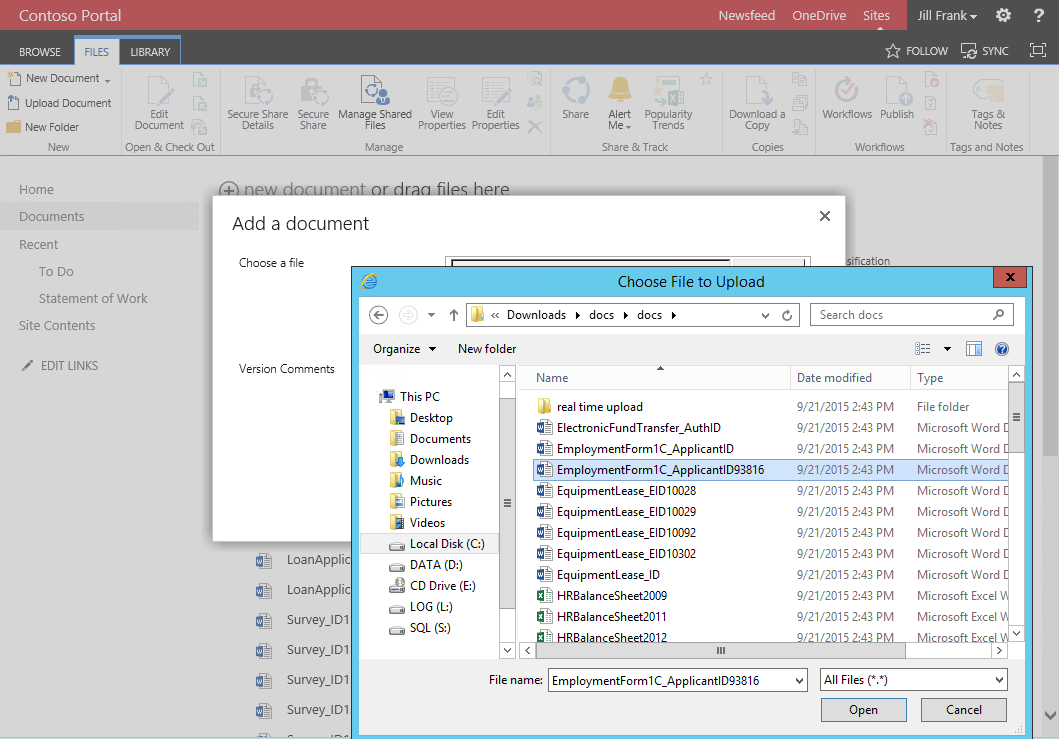
However, this time, she receives a warning message and email letting her know there was sensitive information in the document she was uploading.
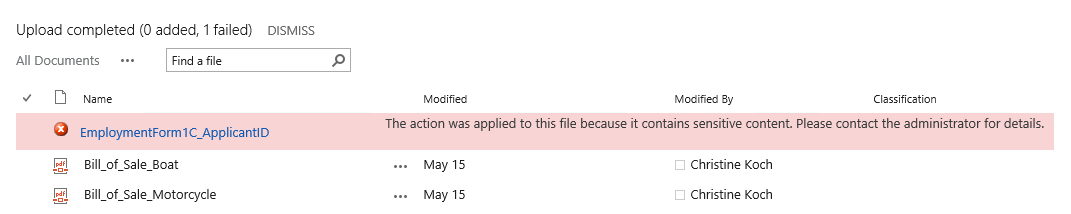
Three things happened behind the scenes when Jill uploaded the document:
- AvePoint Compliance Guardian first intercepted the upload and scanned the entire contents of the document looking for sensitive information based on the library and permissions.
- Then, based on the results of the scan, AvePoint Compliance Guardian tagged the document and the classification column in SharePoint and sent an automated email.
- Lastly, AvePoint Compliance Guardian encrypted the document to protect it and started an incident workflow, which we will see below.
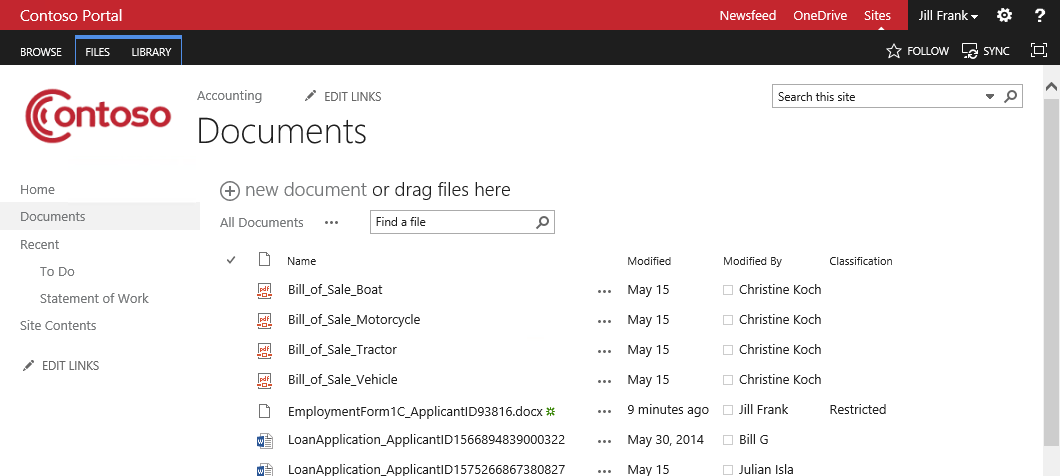
When she returns to the library, Jill sees that her document is marked “Restricted” and it is encrypted when she tries to open it.
There is also an email waiting in her inbox explaining the incident.
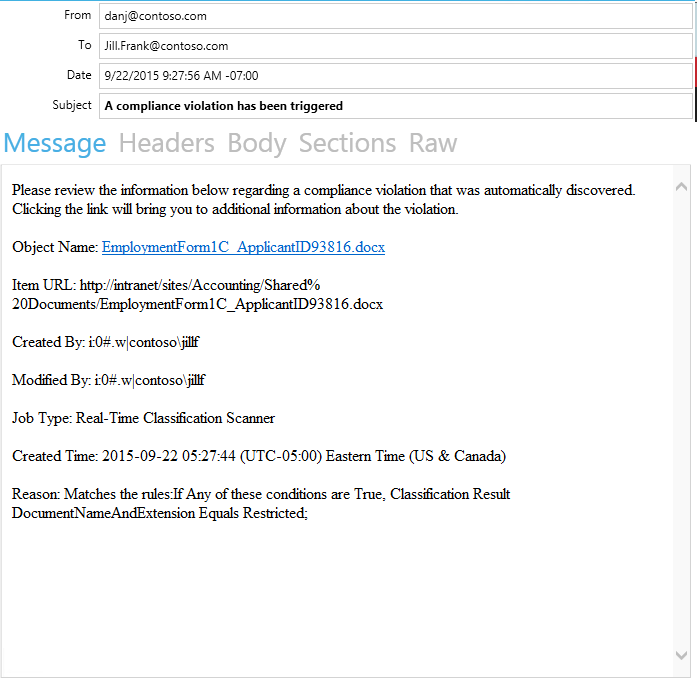
At the same time, Jill’s manager and the organization’s Controller, Karim, has also received an email informing him that a compliance incident has been assigned to him.
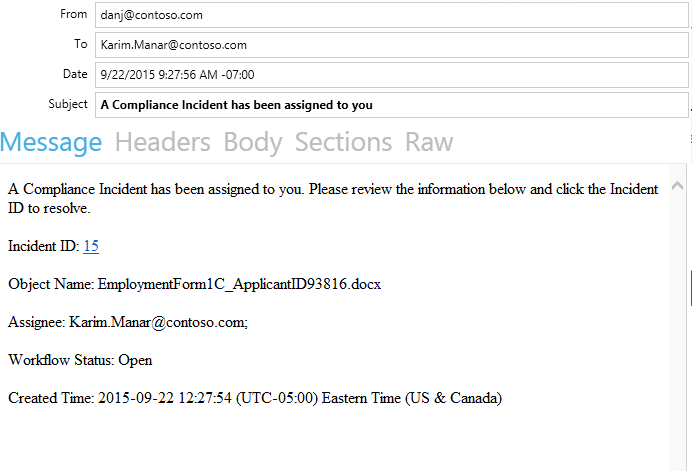
Karim was assigned to this incident automatically because of configurations that were easy to set up. An administrator utilizes Active Directory (AD) users or groups as well as properties such as “Title” or “Department” when setting up automatic alerts and assignments. Additionally, you can add a SharePoint group if you utilize them for handling privacy-related responsibilities and tasks.
The link brings Karim to the Incident Management Center in AvePoint Compliance Guardian. On the summary tab, Karim can see that the document failed a PII scan in SharePoint and was assigned to him to review. He reviews the tabs to gain more information.
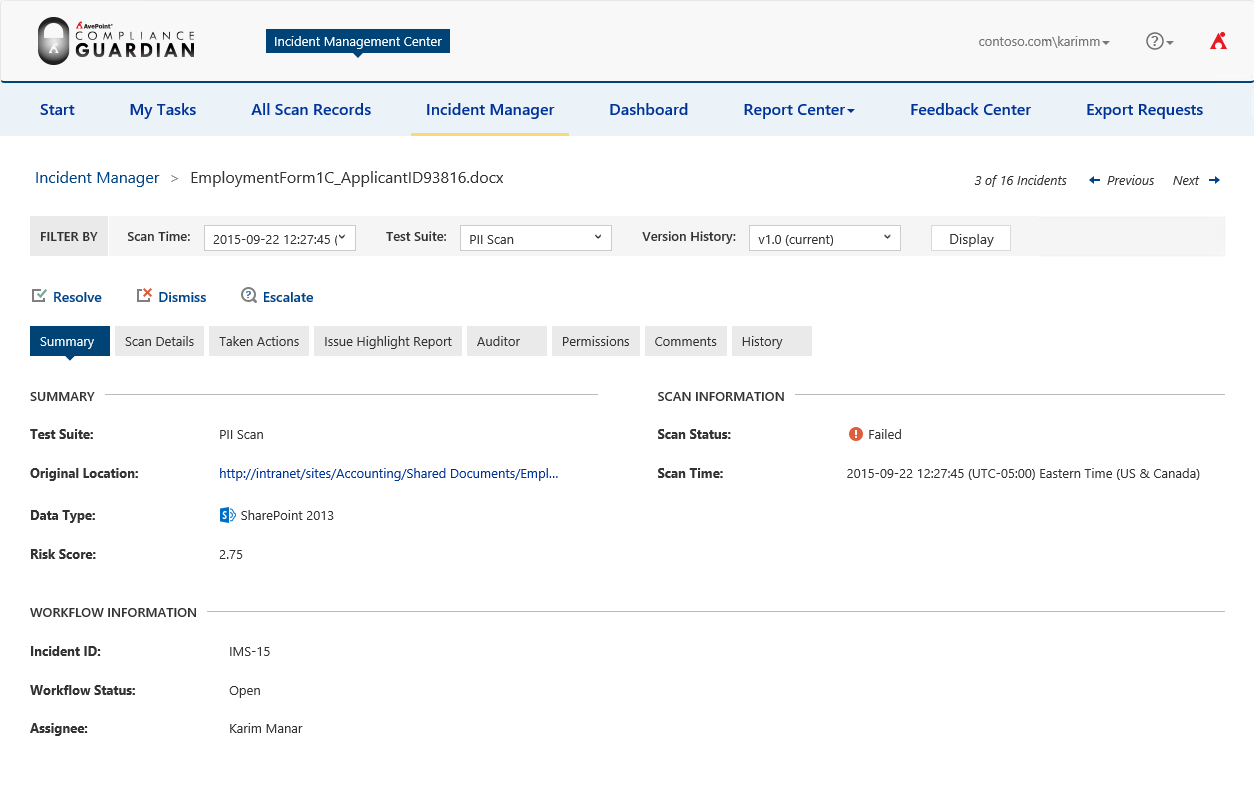
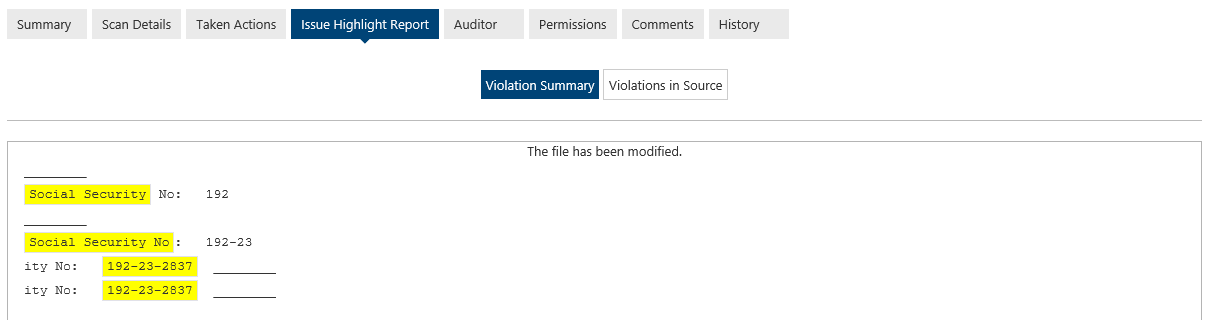
On the “Scan Details” tab, he sees that Compliance Guardian specifically found a social security number in the document.
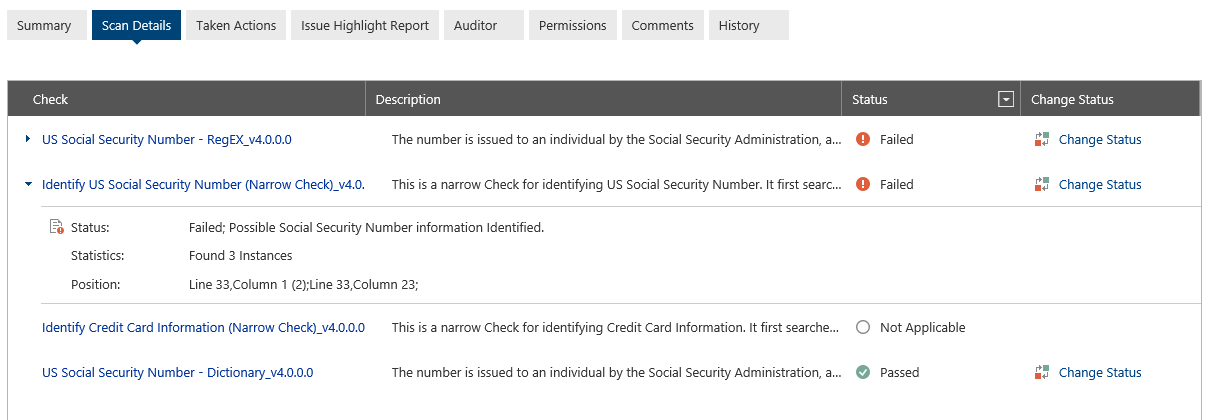
On the Taken Actions tab, he sees that the document was tagged “Restricted” and encrypted, which is what Jill saw earlier in SharePoint.
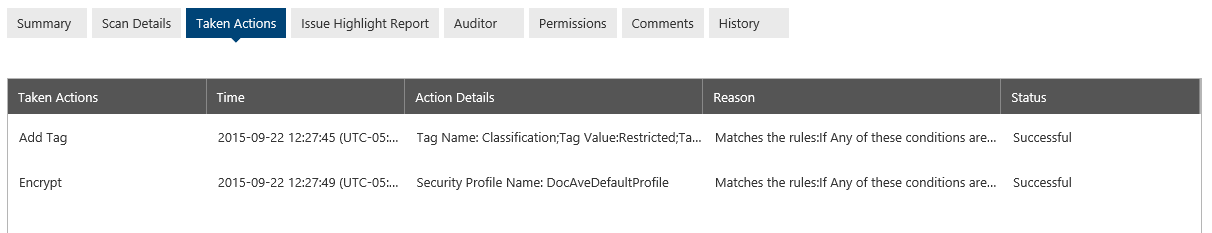
On the “Issue Highlight Report” tab, Karim can quickly see the violation or get the full context of it in the document itself. Please note that Compliance Guardian does not store the violations but instead surfaces the content from the live document.
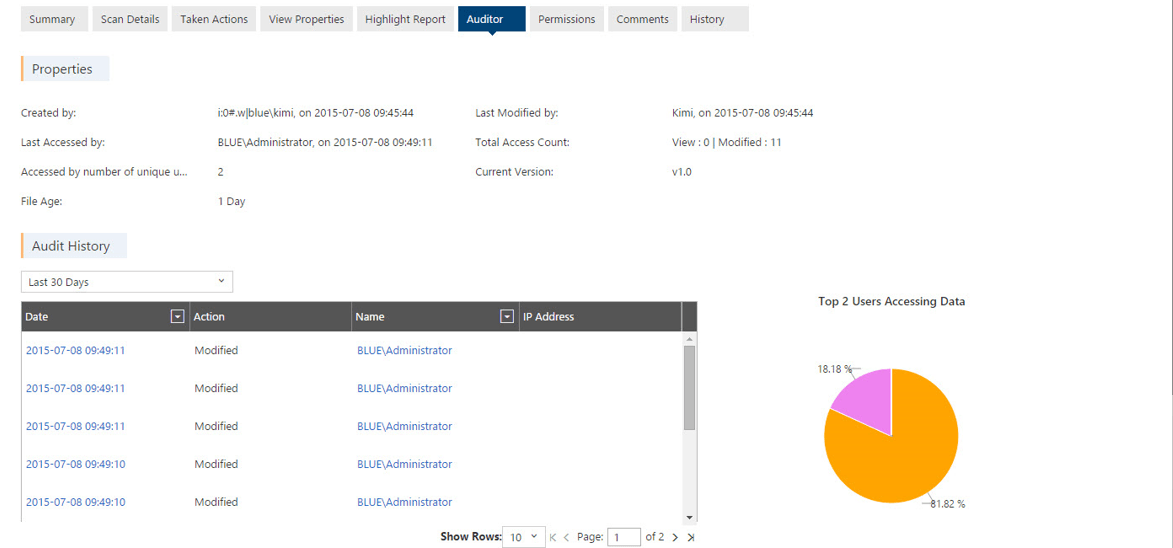
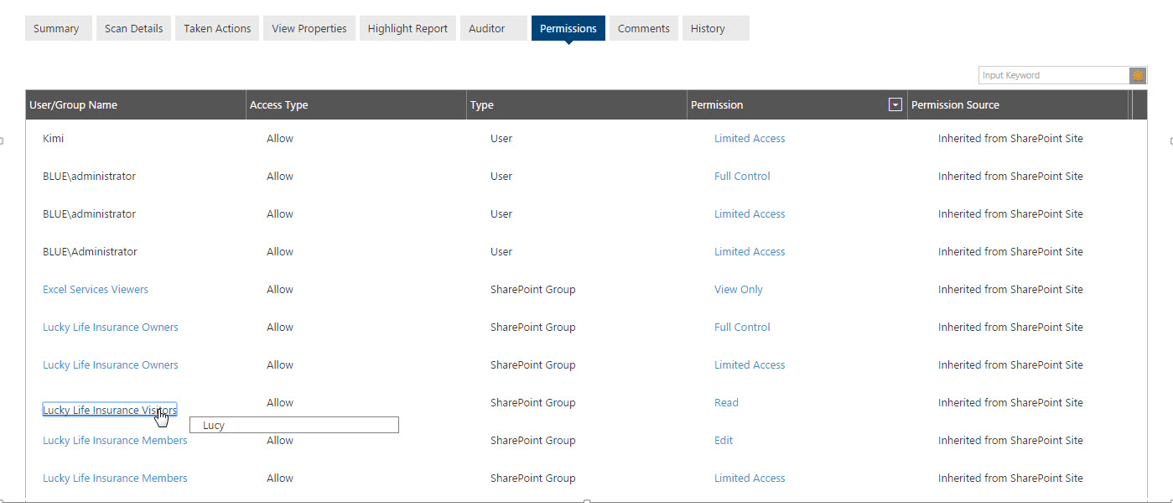
The “Auditor” and “Permissions” tabs give information about who has used the document and who can use the document. This can be important in a situation where the violation was not caught in real time upon upload, as was the case with Jill. Karim would want to know if there was a breach and who has access to the document. It may look like these examples below.
Karim also has the ability to make comments on the incident and view the history of the incident if anyone else is involved in resolving it.
Once he has reviewed the incident and is ready to proceed with a resolution, there are three choices for him above the tabs: “Resolve”, “Dismiss” and “Escalate”. In this case, he decides to “Resolve”.
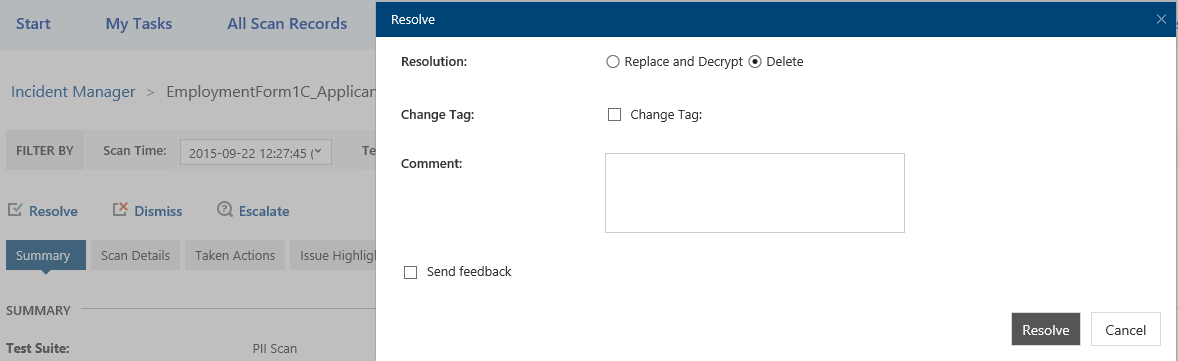
He decides that the document is not appropriate for this library and deletes it.
Back on the Incident Manager list, Karim can sort the incidents by Risk Score to prioritize his reviews to the most urgent cases.
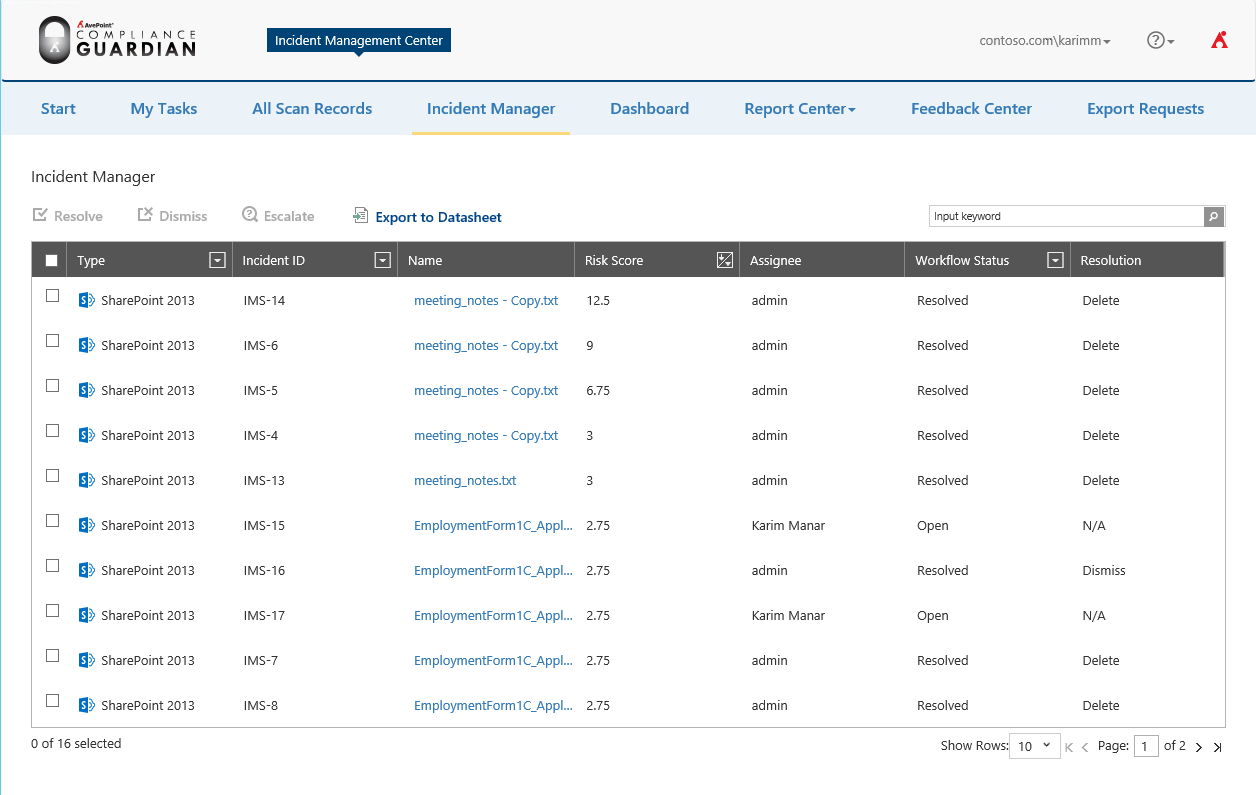
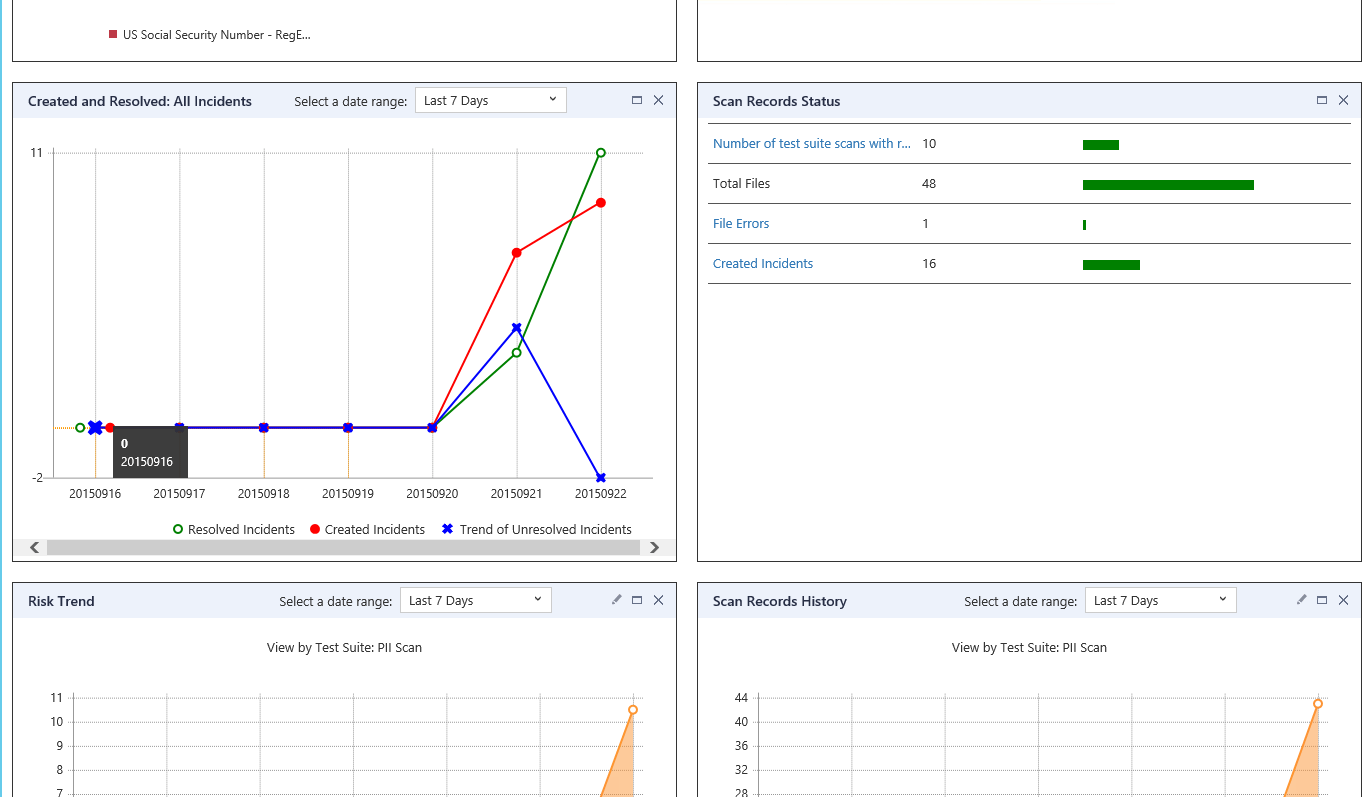
He also has heat maps and dashboard reports to help him understand important key performance indicators (KPIs) regarding risk in the environment.
Making Risk Management a Shared Responsibility
Organizations are rightfully concerned that they have undiscovered intellectual property (IP) on file shares, sensitive content on extranets, or PII published on public web apps as well as what this “dark data” implicates. The size of the problem may be overwhelming, and the solution has three dynamic variables that determine the correct action, complicating the issue further.
Inaction is no longer an option, as the threat of data breaches and the loss of trust and significant fines that come along with them continue to loom overhead. That leaves technology and automation as the sensible road forward. The ideal solution manages the “who”, “what”, and “where” of each piece of content and delivers a prioritized and manageable list of tasks to appropriate resources throughout the organization, as compliance is a group effort and a responsibility that should be shared by all. With AvePoint Compliance Guardian, organizations finally have a way to identify and react efficiently to compliance violations before they become public information.
Want to see how AvePoint Compliance Guardian can benefit your organization and help you automate incident management? Contact our sales team or request a free demo today!

