- Security provisioning and change requests fulfillment on demand based on business need, with the ability to centrally audit and track all changes
- Involvement of business owners that have insight on content sensitivity into the security review process with multi-stage approval, enabling compliance officers to enforce data governance
- Continual monitoring of who has access to what content with scheduled permissions recertification, enabling you to stay apprised of the latest content and permissions to ensure access is given only to those who should have it
- Automated removal of permissions after a set time period to provide stricter security control with less effort
- Relieving IT of the traditionally manual and repetitive administrative task of assigning permissions with an automated and seamless process, freeing time to focus on business value adding activities
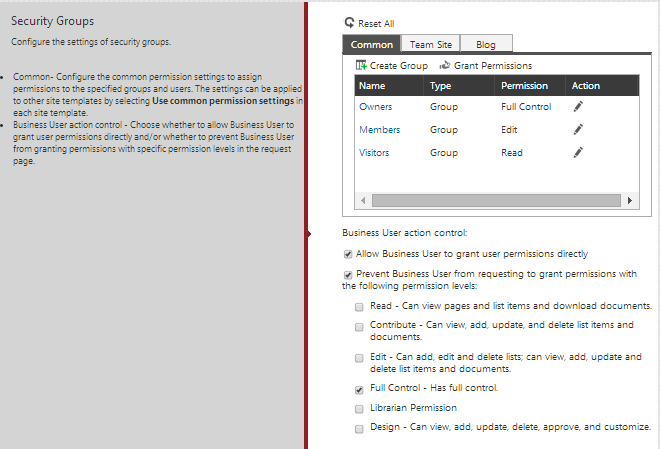 The new and improved interface for security assignment during the site and site collection provisioning process.[/caption] [caption id="attachment_3562" align="alignnone" width="674"]
The new and improved interface for security assignment during the site and site collection provisioning process.[/caption] [caption id="attachment_3562" align="alignnone" width="674"]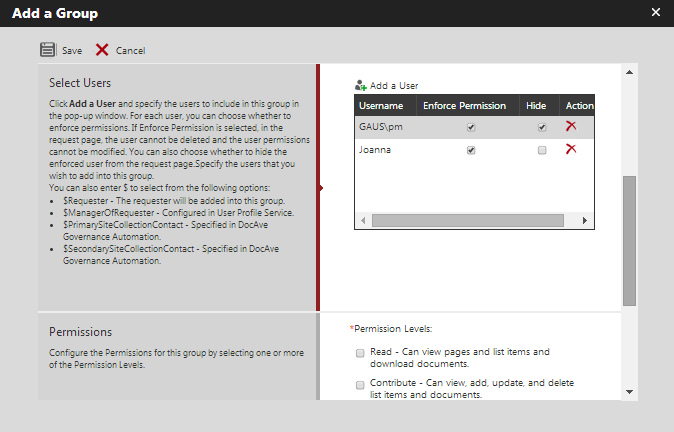 Mandate specific AD users or groups to a permission group and optionally hide this information on the request form.[/caption] The ability to prevent business users from requesting certain permission levels is carried over to Governance Automation’s “Grant Permissions” service, where the administrator can mandate permission level exclusions on the request form. The exclusions apply to both granting a user permissions directly and permissions inherited by adding them to a SharePoint group. For example, a requester will not be able to add other users to the SharePoint site owners group if the full control permission level is excluded from the request page. [caption id="attachment_3563" align="alignnone" width="661"]
Mandate specific AD users or groups to a permission group and optionally hide this information on the request form.[/caption] The ability to prevent business users from requesting certain permission levels is carried over to Governance Automation’s “Grant Permissions” service, where the administrator can mandate permission level exclusions on the request form. The exclusions apply to both granting a user permissions directly and permissions inherited by adding them to a SharePoint group. For example, a requester will not be able to add other users to the SharePoint site owners group if the full control permission level is excluded from the request page. [caption id="attachment_3563" align="alignnone" width="661"]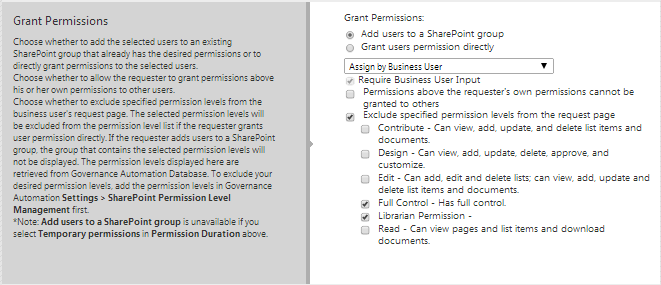 Security settings in Governance Automation’s “Grant Permissions” service.[/caption] As you can see, Governance Automation SP 5 provides administrators more flexibility when managing security assignments throughout the process of provisioning and granting permission requests. Administrators can now be more proactive in helping prevent security breaches by ensuring that only the appropriate permission levels are available for user requests, instead of relying on users to reject inappropriate permission requests during the approval process. With the ability to prevent users from granting full control permission to others, Governance Automation helps eliminate permissions sprawl as users will no longer be able to grant others permissions directly within SharePoint but rather request permissions through the managed process that the solution provides. The ability to mandate specific AD users or groups to both native and custom permission groups ensures that all the accountable business users are given the necessary permissions to do their jobs. In the next post, we will discuss the powerful enhancements made to enable administrators to automate content database management. In the meantime, please visit our product page for more information, videos, and screenshot tour of DocAve Governance Automation. To try the solution for yourself, download a free, 30-day trial today!
Security settings in Governance Automation’s “Grant Permissions” service.[/caption] As you can see, Governance Automation SP 5 provides administrators more flexibility when managing security assignments throughout the process of provisioning and granting permission requests. Administrators can now be more proactive in helping prevent security breaches by ensuring that only the appropriate permission levels are available for user requests, instead of relying on users to reject inappropriate permission requests during the approval process. With the ability to prevent users from granting full control permission to others, Governance Automation helps eliminate permissions sprawl as users will no longer be able to grant others permissions directly within SharePoint but rather request permissions through the managed process that the solution provides. The ability to mandate specific AD users or groups to both native and custom permission groups ensures that all the accountable business users are given the necessary permissions to do their jobs. In the next post, we will discuss the powerful enhancements made to enable administrators to automate content database management. In the meantime, please visit our product page for more information, videos, and screenshot tour of DocAve Governance Automation. To try the solution for yourself, download a free, 30-day trial today!
