The desire to move to the cloud has reached its zenith. Where previously organizations cited issues such as loss of control and data sovereignty as barriers to adoption, it seems that the desire to leverage the cost and flexibility benefits of cloud technology has begun to outweigh the risks at even some of the most conservative of organizations. In fact, a recent Gartner survey indicated that 80 percent of organizations intend to use cloud services in the next 12 months. Still, for those who utilize Microsoft technologies, accessing the cloud in a seamless manner can still provide a few hurdles. One of these challenges lies in understanding the authentication landscape, and how to set it up for your business.
The key to understanding authentication – or the process of determining somebody is who they say they are – lies first in identifying what you are attempting to achieve, and secondly in becoming familiar with the various moving parts I will outline in this article. From an objective point of view, many businesses are looking to achieve three objectives through their cloud technologies:
- The most robust setup they can have
- The lowest total cost of ownership possible
- A seamless end user experience
As with all technical challenges, there is no one-size-fits-all answer for authentication in the cloud. However, by understanding the different needs of Office 365 and Azure implementations, the decisions are easier than many would expect.
Core Technologies
As a basis for understanding authentication, there are a number of core technologies you need to be aware of. These include:
- Active Directory (AD)
- Active Directory Domain Controllers (AD DC)
- Active Directory Federation Services (AD FS)
- Azure Active Directory (Azure AD)
- Office 365 Directory Synchronization (DirSync)
- Azure Active Directory Sync (AAD Sync)
- Azure Active Directory Connect (In preview)
Depending on your implementation decisions, you will require a combination of these technologies to achieve your objective.
Office 365 Authentication
For organizations implementing Office 365, user accounts fall into two categories: cloud and federated identities.
Cloud Identity
Cloud identity credentials use an Azure AD, which is separate from an on-premises identity. This setup is fine for businesses that are entirely based on Office 365. However, for those using a hybrid environment with a combination of on-premises and Office 365 services, the end users would have to maintain and manage different sets of credentials and passwords for the different services. Although this might seem like a small inconvenience, it is well known that end users hate managing passwords, and especially hate having to remember multiple passwords that are out of sync and under different accounts. Ultimately, this could challenge adoption.
Federated Identities
To simplify this situation for hybrid environments, Office 365 offers federated identities, which enable on-premises AD credentials to be used for your Office 365 services as well.
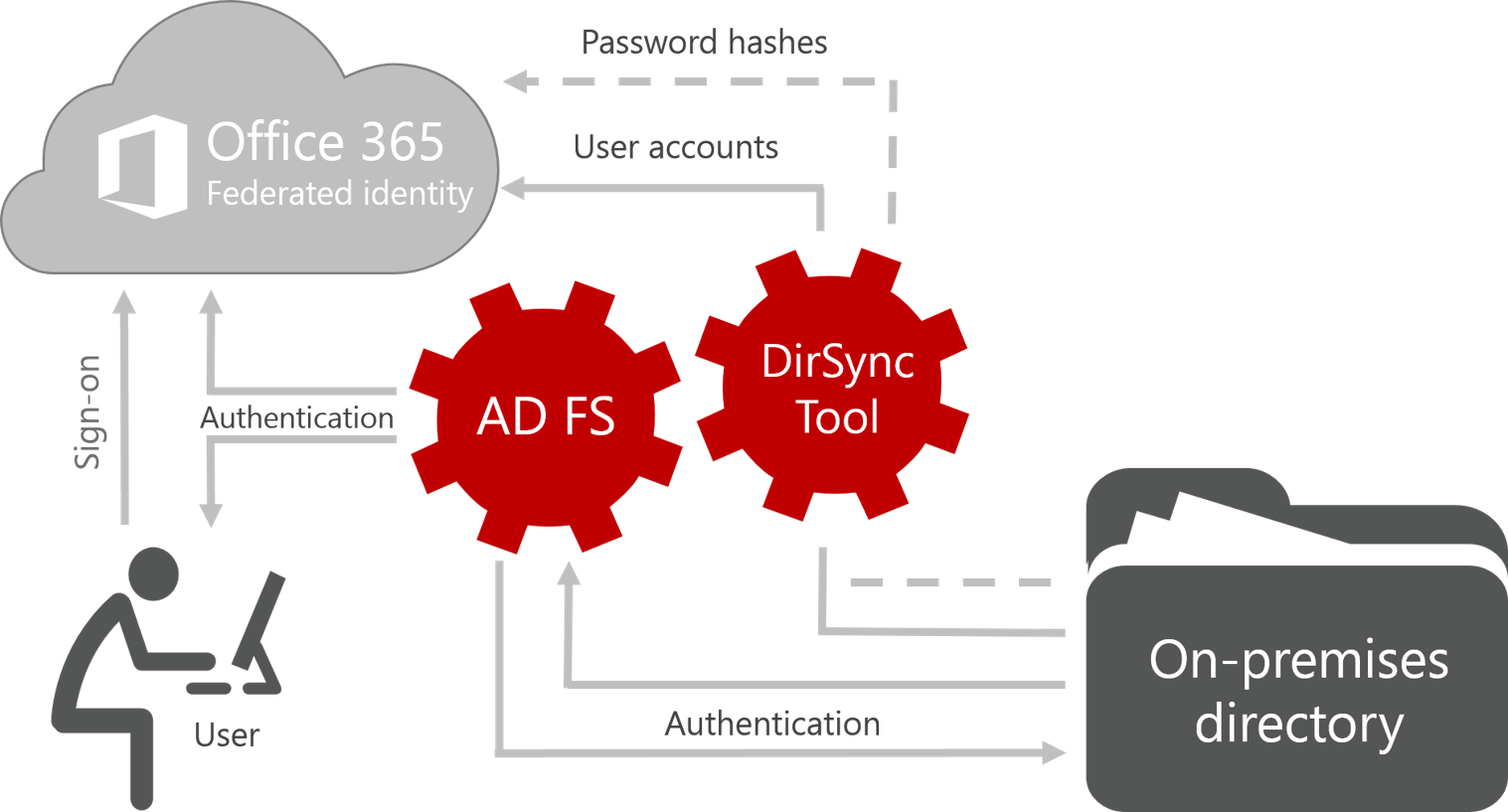
In the implementation phase, there are two choices for Federated Identities. DirSync or its newer replacement AAD Sync can be set up between your on-premises AD and Azure AD. Installed in isolation, these provide a same sign-on experience, meaning the user credentials and passwords for both your on-premises and Office 365 implementation are kept in sync. The advantage of this solution is that there are no real infrastructure upgrades required if you do not already have AD FS – just the configuration of the tool. The disadvantage is that users have to sign in to both your on-premises and Office 365 setups.
The second and more seamless experience involves choice involves setting up DirSync along with AD FS so that not only are users accounts kept in sync, but instead of the user being prompted to log in to Office 365 using their on-premises credentials, the authentication request to Office 365 is handled by AD FS. This provides the true single sign-on experience, which, unlike same sign-on, does not require the user to enter their credentials multiple times. In contrast, however, it does present the drawback of having to implement AD FS (with high availability AD FS recommended) into your infrastructure.
To support this more involved setup, the AD team at Microsoft has recently released (in preview) Azure AD Connect, which incorporates Azure AD Sync and the setup of ADFS.
Azure Authentication
Authentication for Azure implementations present other challenges. The common infrastructure setup for Azure to on-premises integrated environments involves AD deployed on premises, with a site-to-site VPN connection to the Azure Virtual Machines (VMs). The challenge with this setup is that end users accessing solutions running on Azure VMs still require authentication. Azure AD can be the solution for some situations. For organizations that wish to use separate identity providers, Azure Access Control Service can be setup to authenticate systems like Microsoft SharePoint 2013 running on Azure VMs, while on-premises systems can continue to use on-premises AD.
Single Authentication Provider in Azure
For those looking to use a single authentication provider, it is important to remember Azure AD is not a replacement for on-premises AD. For example, you cannot join a user to an Azure AD. As a result, authentication requests to cloud-based systems (such as a SharePoint 2013 farm) can still require authentication to Domain Controllers. Charges for traffic over the VPN means that most organizations may want to avoid authentication requests from Azure VMs going back and forth to on-premises AD. Implementing a High Availability Domain Controller setup on Azure VMs with directory replication and cloud authentication requests being handled by cloud-based DCs can provide a more streamlined implementation.
Asking the Right Questions
There are many different technologies available for authentication and identity management, and Microsoft has put a lot of effort into documenting each one with samples and tutorials of how to implement them into your organization. The challenge for most businesses is in understanding what they are looking to achieve and what their technical constraints are. Key questions to ask include:
- Can you run your IT infrastructure entirely in the cloud, or do you have on-premises constraints such as AD?
- Will your Office 365 – SharePoint Online environment be heavily accessed by locally authenticated internal users?
- Do you currently have AD FS setup, or do you have the ability to set it up in the future?
- Do you have multiple instances of AD – also known as forests?
Helpful Resources
For further reading on the topic of authentication, I recommend checking out the following resources available from Microsoft:
- Supported scenarios for using AD FS to set up single sign-on in Office 365, Azure, or Intune
- Synchronizing your directory with office 365 is easy
- Office 365 User account management
- Active Directory Federation Services (AD FS),
- Azure Active Directory (Azure AD)
- Office 365 Directory Synchronization (DirSync)
- Azure Active Directory Sync (AAD Sync)
- Azure Active Directory Connect
To learn more about how AvePoint can help simplify your management of SharePoint in the cloud, on premises, or through hybrid deployments, please visit our website.
Have a question about authentication? Let us know by commenting on this blog post!

