The following is an excerpt from our Mitigating Collaboration Risk Workbook. Download the full book here!
Check out our other ebook excerpts below:
When it comes to mitigating information risk, you first need to decide which of the risks in your risk portfolio makes sense to mitigate first and develop a list of approaches for doing so. In combination, whatever mitigations you embrace need to address the people, process, and technology aspects in a coherent and balanced way.
Mitigations to consider include:
Data Classification
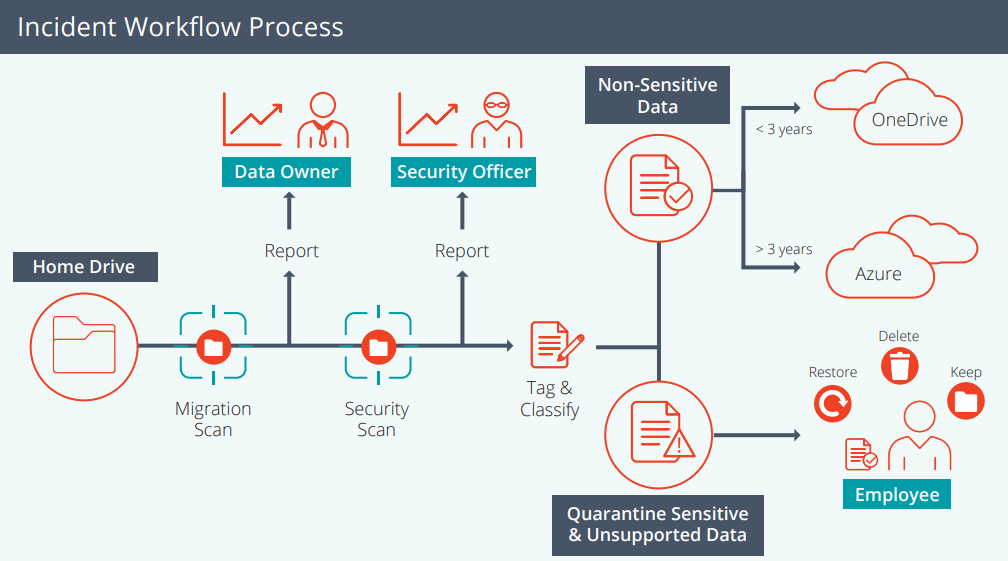
Classifying confidential, personal, sensitive, and protected data wherever it exists across your data estate. The ability to mitigate information risk relies on the ability to identify specific information at risk, and both manual and automated classification approaches enable this.
If data is classified in advance, then downstream security technologies can apply policy-based decisions, data access requests by data subjects are greatly simplified, and decisions on archiving and deletion streamlined. File Analysis, a capability in AvePoint Compliance Guardian, provides a classification of files in target systems based on the data types within each file.
Need help creating a risk mitigation plan? Check out this post: Click To TweetPolicies for Handling Information
Develop the access, sharing and protection policies that should apply to the various types of information collected, stored and used within your organization. AvePoint PI allows you to quickly set your policies based on the regulations and different categories of risk that are important to your organization, so you can enforce broadly stated but ineffectual policies.
For example, the who involved in a sharing action—and in comparison to their usual task set and the baseline of sharing activities for all people in that role—will dictate whether a specific sharing action represents minimal, moderate or high risk. PI will trigger a different policy response based on additional context factors of this nature.
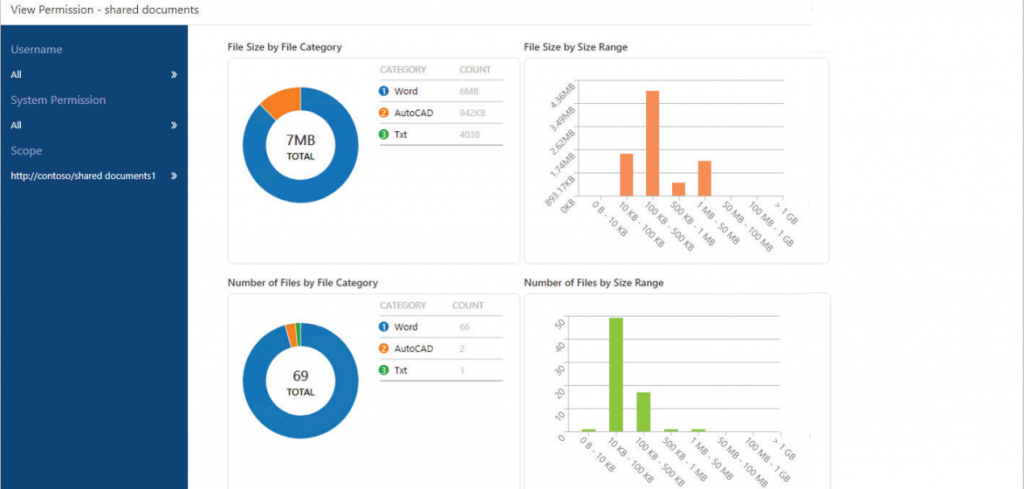
Minimize Duplicate Data
Duplicate data should be minimized, such as through deletion or encryption. For example, extracts of sensitive data from structured authoritative systems that are now held in unstructured formats should be tightly controlled to prevent inadvertent access or breach. Once identified through classification mechanisms, the data can be automated deleted, restricted through encryption, or restricted through applying a specific access policy.
Information Risk Awareness Training
Helping employees to develop an awareness of the rhyme and reason for the various controls, policies, and risk safeguards creates a human layer of risk mitigation.
Similar in intent to Security Awareness Training but tailored for information risk, such training programs explore rationale (the why, such as regulatory requirements to protect sensitive data), technical and policy mitigations (the how, including data classification aligned with DLP policies), and the new work practices required (the what, such as using AvePoint Cloud Governance for requesting a new workspace so that access, classification, and retention policies can be applied to the workspace as an integral element of its creation process, along with ongoing recertification of content ownership and classification).
Find out the other steps of creating a risk mitigation plan in the full workbook!

