This is an excerpt from our latest ebook “The Value of Automated Office 365 & Microsoft Teams Governance.” Download for free here!
There are few native controls governing the methods of adding (provisioning) collaboration spaces (SharePoint Sites, Groups, Teams, OneDrives), users, mailboxes, and other objects into Office 365. As such, there are several common challenges that spring up for those new to the platform.
1st Challenge: Group Sprawl
Because of the lack of moderated controls, organizations are typically forced to put the full burden of creating users, workspaces, and sometimes even content on IT administrators.
The only alternative involves allowing either all business users or subsets of users to create objects with little to no oversight. Allowing objects to be created without proper enforcement can increase risk within organizations and create tons of “clutter,” making it more difficult for users to find what they need.
2nd Challenge: Consistent Naming Conventions
Out-of-the-box, Office 365 offers the ability to enforce a naming policy to assist in communicating the function of a group, membership, geographic region, or who created the group.
This approach adds either a prefix or suffix (or both) and is applied across the entire Office 365 tenant–meaning that all Teams in the organization are limited to having the same settings applied to them. This presents a challenge for any organization that has more than one division (which is generally the case).
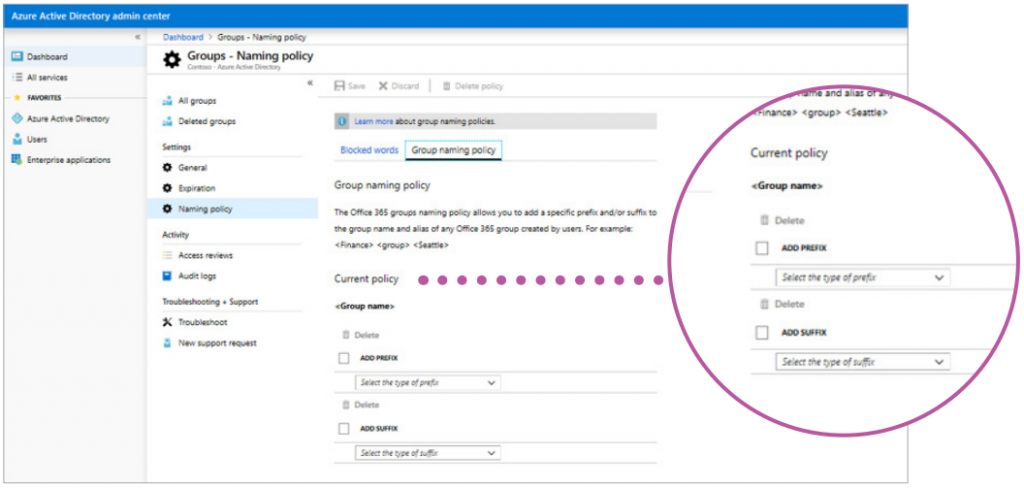
Divisions will often have different needs and preferences for naming, and the Microsoft naming convention is one-size-fits-all within the tenant. The native naming functionality also relies heavily on Azure Active Directory properties being complete and correct for all employees (which is rarely the case).
3rd Challenge: Public vs. Private Groups
When a new Group is created, owners are asked if it should be a public or private group. However, there’s no clear messaging to users around the implications of this choice. Users are generally unaware that for public Groups anyone in the organization can see, alter, and delete your files.
A public Group is exposed to all users within your Office 365 tenant, including any vendors or contractors to whom you may have granted an account within your Office 365 subscription. Users can browse, search, and instantly join a public Group.
Even non-members of a public Group can access, edit, and share all the Group’s files and information. Every new user you add to your Office 365 tenant receives the same rights.
Setting a Group to private immediately prevents organization-wide access to files and information which may only be appropriate for the eyes of a few. However, even when Groups is set to private, its membership is still visible throughout the entire organization.
4th Challenge: External Access
The next issue to consider is sharing with external guest users whose accounts and credentials are not controlled within your Office 365 tenant. By default, at the tenant level, Office 365 Groups allow owners (therefore end users) and Office 365 global administrators the ability to:
- Add external guests as members.
- Provide external guests and members access to Group files and OneNote.
Since this is at the tenant level, this is an all or nothing proposition. However, some departments may have a greater need for external collaboration and deal with less sensitive information.

