Learn how to streamline your day-to-day management tasks with our free ebook “The Value of Automated Office 365 & Microsoft Teams Governance.” Download here!
Read the other posts in our Securing Collaboration series below:
- How to Get ISO 27001-Ready
- Oversharing Challenges in Microsoft 365
- How to Find Sensitive Content in Office 365
- Sensitive Info Identifiers in Office 365
- 5 Risk Management Challenges in Office 365
- Top 5 Microsoft 365 Security and Compliance Center Features and Tricks
- How to Build a Strong Permissions Management Strategy
When to Upgrade From E3 to E5 for Stronger Microsoft 365 Data Protection
I recently wrote a blog post about trying to find the “Signal in the noise” of our new data-driven society in order to make good cybersecurity decisions based on actionable intelligence. In an effort to provide more and more value to customers, technology providers like Microsoft continue to subscribe to the idea that “more is better,” providing vast arrays of new functionality that allow businesses to parse and analyze their data.
But in truth, when this data is unmanaged it simply becomes more noise and more work. That being said, I have a strong belief that not knowing something is happening is always worse than figuring it out. So using the Microsoft technology stack, how do we prioritize our efforts, focus our attention, and pinpoint the issues that we really need to address? How do we find the signal we have been looking for in the noise of our information society?

Trust-and-Verify Approach to Compliance
It’s all about the data. Every organization has sensitive data, but it’s a question of what it is, where it is, who can access it, what they’re doing with it, where it’s flowing, and with whom it is being shared. All of this needs to be proactively managed as part of a good data governance and data life cycle management program.
However, many organizations have data governance policies that are theoretical rather than operational. In other words, there’s a corporate policy that is unenforced or left to the business users to implement. The challenges presented by a trust-driven system include key questions that need to be verified including:
- Is data being properly tagged?
- Are inappropriate discussions happening?
- Is sensitive or confidential information being shared with internal or external users?
- Are privacy and compliance policies being circumvented, either deliberately or inadvertently?
Making it easier for your employees to do their job successfully while building a more secure environment includes implementing a culture and technology systems where privacy and security controls are not limited to “once a year” training sessions, but rather an ever-present “culture of compliance” where it’s easier for your employees to do the right thing than to do the wrong thing. Companies must create a transparent security organization to discourage employees from working around security. For this reason, AvePoint’s approach supplies a trust-and-verify method to ensure users are doing the right thing, while preventing inadvertent breaches from occurring.
AvePoint’s Approach to Compliance
AvePoint takes a pragmatic approach in ensuring data-centric audit and protection delivers business value. We empower organizations to effectively establish and implement a data governance framework.
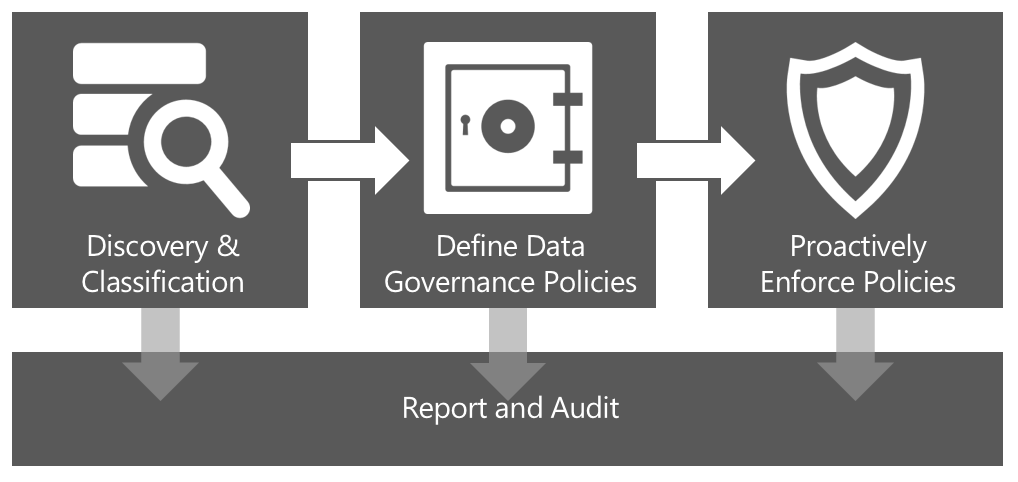
Discovery and Classification
Many companies worry about “dark data” (data that is not properly understood) or data that exists across their enterprise systems (file shares, SharePoint, social systems, and other enterprise collaboration systems and networks). Understanding what and where this data is and properly classifying it will allow organizations to set the appropriate levels of protection in place.
For example, many companies apply their security controls in broad terms using the same security procedures for everything. But logically, do you need to put the same security protocols around pictures from your company picnic as you do towards your customer’s critical infrastructure design, build information, or credit card information?
Data discovery will allow you to determine the origin and relevance of the data you hold, and establish a suitable retention schedule. You’ll be more equipped to effectively implement Data Loss Prevention in a tactical way. Data-aware security policies provide an opportunity for organizations to build a more layered approach to security, prioritizing where efforts (and costs) should be spent, and building multiple lines of defense.
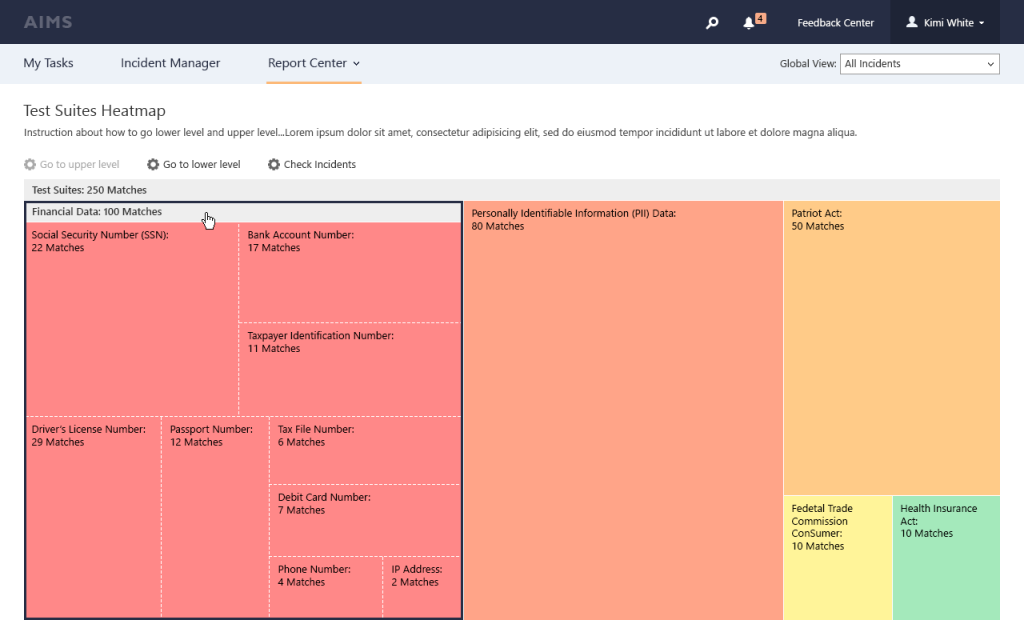
AvePoint Compliance Guardian discovery solutions analyze, index, search, track and report on file content and metadata, enabling organizations to take action on files according to what was identified. Compliance Guardian Data discovery capabilities allows you to discover where “dark data” lives no matter if it’s in an on-premises or cloud environment.
Define Data Governance Policies
Proactively Enforce Policies
One of the biggest challenges organizations face as it pertains to data governance and information lifecycle management is actually enforcing corporate rules that govern how users interact with and share data across the enterprise. As part of AvePoint’s best practice approach to implementing a data governance strategy, technology is an important factor that shouldn’t be overlooked to help incorporate an automation layer that will proactively enforce the policies and rule you put in place.
An effective technology strategy to enforce these policies is one that takes into account the following areas:
- Privacy and Security by Design
- Data-Centric Audit and Protection
Privacy and Security by Design
The basis for any solid Data Protection strategy is to ensure that data privacy and security is incorporated into the design of the governance framework. AvePoint’s AOS platform is designed with this methodology in mind. As organizations implement/enhance their data governance programs, they can leverage AvePoint technology, like Cloud Governance, to build into their collaboration systems policies that can carry out the management of the data lifecycle from its origination point through its disposition with automation. This includes:
- Categorization of Data Repositories – Provides organizations with a way to determine the business need or use of data repositories which in turn drive the governance policies that need to be enforced on the data.
- Automated Information Lifecycle Management – Automated management and enforcement of data destruction and disposition rules based on the content and/or the data repository categorization with business stakeholder input.
- Recertification and Audit – Proactive and automated periodic review of data ownership and access credentials in an effort to reduce the risk of data leaks and unapproved access to content.
- Built-in Governance – As the end user community continues to collaborate and originate content, governance policies are automatically provisioned into collaboration containers at the time of onboarding in an effort to ensure proactive enforcement.

Data-Centric Audit and Protection
AvePoint Policy and Insights “PI” helps you monitor Microsoft 365 platform so you can easily answer critical questions for your security team such as “Who has access to sensitive data?” “Have they accessed it?” “Are any external users a threat?”
PI provides insights to answer critical security questions about your Teams, Groups, Sites, and OneDrives. You define what risk means to you by selecting the regulations or permissions controls you care about most! PI does the work of combining, parsing, and prioritizing your potential issues so that you can cross-reference access controls with sensitivity and activity data. Easily identify issues including over-exposed sensitive content, over-active external users, shadow users, and other security concerns. Then, take action where it has the most impact.
Want more best practices for managing data in the cloud? Check out these resources:
- Blog Post: A Look at What’s New in Microsoft Planner
- Blog Post: Office 365 Governance in the DOD: Explained
- Blog Post: Which Tool When: Microsoft Lists, Planner, Tasks in Teams, or To Do?
- Webinar: How To Ensure Microsoft 365 Collaboration Success For Remote Workers
- Webinar: 3 Ways to Successfully Drive Office 365 Productivity and Change Management




