In today’s digital workplace, organizations are leveraging AI tools like Microsoft 365 Copilot to revolutionize the way they work.
Forty seven percent of generative AI users are on Microsoft 365 Copilot, according to the AI & Information Management Report.
In fact, early adopters of Microsoft 365 Copilot are seeing its benefits: Microsoft found that 70% of users saw themselves more productive and 68% experienced an improvement in their quality of work.
Due to the benefits of Copilot, 77% don’t want to give it up.
However, to successfully scale the utility of Copilot at work, ensuring data security has become a top priority to sustain the expected level of productivity, according to a AvePoint’s latest AI & Information Management report.
Here’s how AvePoint helps organizations globally to prepare their enterprise workspace to be ready for Copilot, and to harness its return on investment in the long run:
The Essential Missing Step: Identifying Data Loopholes Before Turning on Copilot
As you begin using Microsoft 365 Copilot, it’s important to remember the power of this technology.
Risk of data leaks and unauthorized access to sensitive information heighten as companies begin to use AI. Gartner also predicts that by 2025, generative AI will cause an increased demand for cybersecurity resources, with over 15% boost in spending on application and data security. This roots from Copilot’s ability to use information from anywhere it has access to, which is why it’s crucial to understand where your sensitive or overshared content is stored in your Microsoft 365 environment. This understanding will enable you to implement robust security measures to keep your data secure.
One of the recommendations in a recent Gartner report to lower internal and external risks of data exposure is to integrate a third-party security tool to determine and mitigate such risks. A Copilot readiness solution helps organizations establish a strong data foundation for managing their workspaces to guide user behavior and mitigate risks associated with AI use.
Doing it doesn’t have to be complicated and costly. For just $2 per user, per month, together, AvePoint Insights and AvePoint Policies provide automated solutions for identifying and mitigating potential risks, ensuring consistent policy enforcement, and prompt remediation of policy violations, laying a sound data security foundation for Microsoft 365 Copilot use, and safeguarding your data against unauthorized access.
Here are three best practices to keep your data secure while using Microsoft 365 Copilot:
Run a risk assessment.
Rolling out Copilot requires organizations to think about security in a more granular level to ensure that sensitive information is not leaked to the wrong users. It is critical to take the opportunity to take stock of data exposure and sensitivity across the enterprise before adopting AI at scale.
Before organizations can mitigate risk, understanding the data profile of workspaces and where risks exist in the environment is crucial. This process involves identifying risky behavior, such as overshared or unprotected sensitive information — think personally identifiable information (PII), financial, or regulated data, or content with anonymous sharing links.
For example, an HR SharePoint site that has salary information should only be accessible to the HR department. When implementing AI solutions such as Copilot, this becomes a potential risk because any employee can prompt queries – such as salaries of employees – that can reveal all information available related to the query.
Organizations that share links to external parties, such as vendors and support teams, should also make sure that these links do not include sensitive corporate or client information, which could introduce possibilities of data breaches.
AvePoint Insights have proven to be a cost-effective tool to help organizations take stock of their enterprise data in terms of data sensitivity and exposure to start configuring their ongoing actions to prevent or correct future risks of over exposed data.
Here’s an in-depth explanation on how you can use Insights to detect risks in your workspaces:
Insights scans and aggregates sensitive and over-exposed data across an organization’s Microsoft 365 tenant and allows business or IT users to detect and resolve permission issues instantly. Organizations can delegate workspace administrators, who can set definitions of medium and high exposures for the organization, so they can be notified accordingly when these types of exposures happen in the workspace. Implementing this proactive measure prevents Microsoft 365 Copilot from accessing information intended only for restricted use.
By deploying Insights, in just a few minutes, you can quickly identify:
- Where sensitive content lives in your enterprise workspace
- Potential risks from user access to sensitive content
- Shared links that and external users that are in the Microsoft 365 tenant.
The Insights dashboard enables you to edit in bulk from actionable reports, acting quickly to mitigate any suspicious or risky behavior.
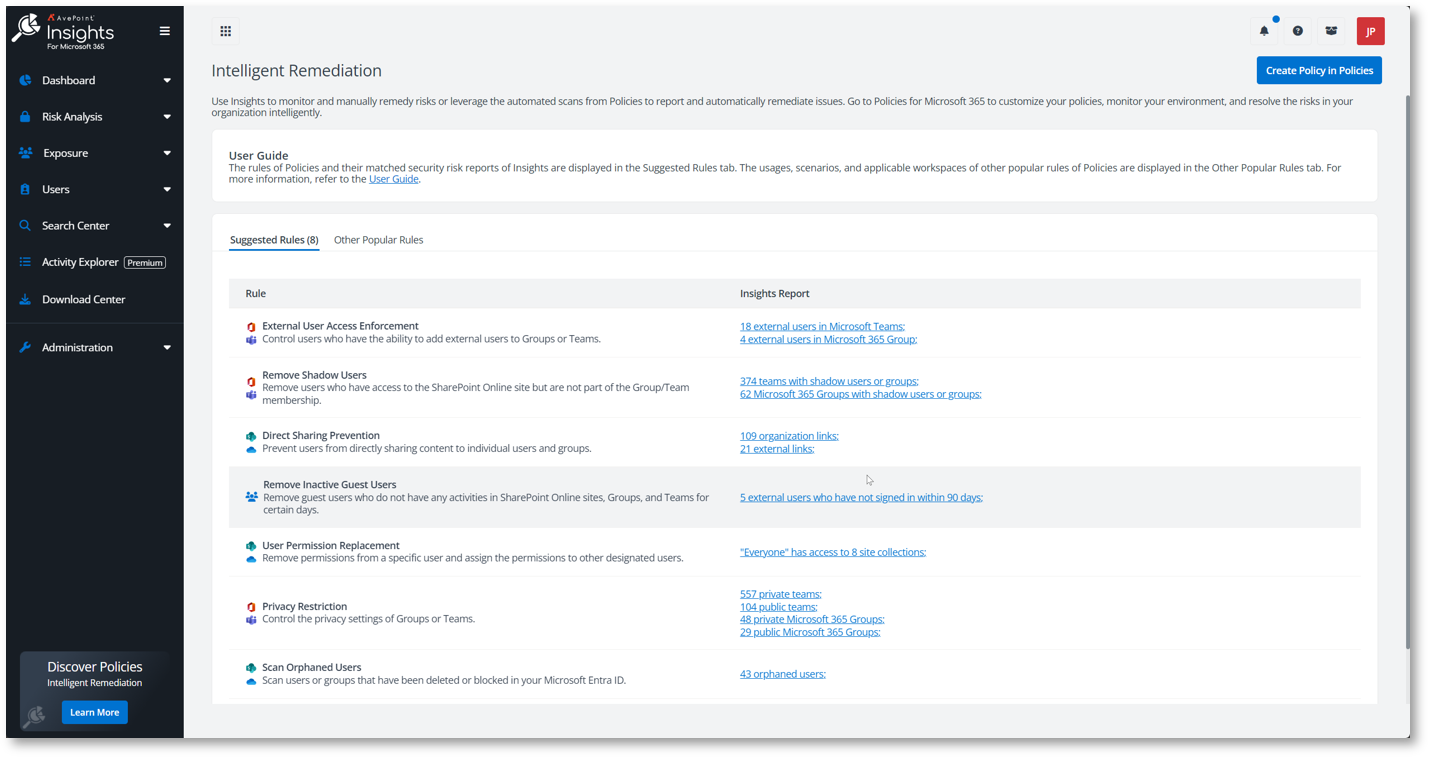
Clean up permissions and enforce policies.
Although detecting and preventing attacks is important, it’s essential for business leaders to also focus on mitigating the risks. This means implementing proper security measures to reduce the risk of internal data breaches.
After identifying the risks in the workspace, to ensure your data remains secure while using Microsoft 365 Copilot, organizations will need continuous data governance, as well as to configure who can access which data. Without this in place, anyone in the organization may trigger a prompt that can provide them information to sensitive data, including those information employees are unauthorized to access.
With these configurations, organizations can secure data using “just-enough-access permissions” and automated policies, to ensure that information surfaced by Copilot to every individual would be limited to information they are allowed to access.
Doing this process manually is possible; you’ll either need to go through each container to adjust permissions or, if you use security groups, you can adjust access and permissions by groups, which will save you a lot of time. Keep in mind, though, that if there are any users inadvertently left out of a security group, their permissions will need to be adjusted independently.
However, as employees use Copilot, data transactions will significantly increase, making data management more complex. It would be a challenge to monitor every query that is made on AI platforms, such as Copilot.
To ensure continuous governance, instead of manually creating classifications and permissions, or fix high-risk items, organizations need an automation tool, such as AvePoint Policies, which can automatically set the necessary security rules to your Teams, Groups, Sites, and OneDrive, or your entire Microsoft 365 tenant if needed.
AvePoint Policies helps organizations act on findings from Insights, subsequently create multiple types of permissions across various workspaces and immediately run them without having to manually set permissions every time.
Maintain your security measures.
Once you have established a secure and compliant environment for your data, it is important to maintain it. However, the task of maintaining control over who has access to what data across different cloud platforms is becoming more challenging, and a recent study confirms this: There are over 40,000 types of permissions available to users, services, and devices, of which 50% are considered high risk.
Therefore, regularly reviewing and updating your security policies is crucial to ensure that they remain up-to-date. This includes monitoring user activity, permissions, and access controls, as well as implementing new policies to address new and emerging concerns.
AvePoint Insights provides automated reporting for IT in at-a-glance dashboards and proactive alerts to flag any irregular or suspicious activity. If the solution flags an issue, you can easily adjust your security measures from within the tool to promptly respond to what it finds, so you can act on any potential concerns in a timely manner.
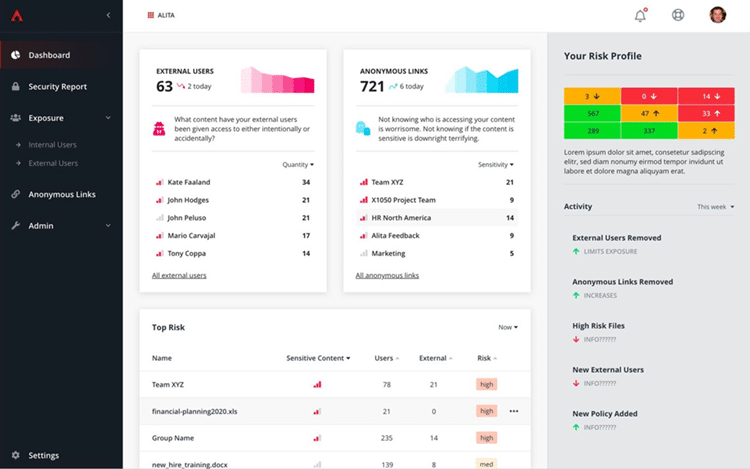
Centralized management and enforcement of policies across Microsoft 365 is also crucial, which can be achieved through AvePoint Policies. It automatically enforces policies, reduces the risk of human error, and monitors for policy violations in real-time, notifying administrators to remediate the issue promptly.
Unlock Microsoft 365 Copilot’s Transformative Power
To unlock the potential of Microsoft 365 Copilot while maintaining compliance and security, you must secure your data. By implementing the data readiness measures discussed here, you can create a secure environment that enables you to derive maximum value from Microsoft 365 Copilot.
To further accelerate your digital workplace success with AI, check out our step-by-step guide for secure Microsoft 365 Copilot adoption. And if you’re ready to take your Copilot experience to the next level, AvePoint has a full suite of Microsoft 365 Copilot data readiness solutions to help you get started.



