As the second most common attack vector, preparing for phishing attacks requires a strategic incident response procedure to mitigate and contain any related risks.
Whether you’re coming up with your incident response plan or actually looking for a guide after being attacked, read on as we go over what you should do if you’re phished in Exchange 365.
With the growing complexity of phishing attacks, it’s becoming harder to identify if you’ve become infected (check out this Microsoft documentation for common signs you should look out for).
Whether you’re only in the initial phase of suspecting or in the middle of verifying the attack, it will be more advantageous for you and your organization to act on it immediately.
I got phished. Now what?
Once attacked by malware, time is of the essence when it comes to cleaning and securing your environment.
The longer the attacker has control over your data and credentials, the higher the risk there is for data loss, increased ransom fees (depending on the type of data they access), and a wider spread of infection.
It’s crucial to go through these steps as soon as there’s a suspected infection:
If You’re a User: As a user, you must understand that a phishing attack affects the whole organization. While it may sometimes seem like it’s the better option, DON’T try to solve it yourself as this may cause more harm than good.

The best practice would be to let your management team know about the attack (or the suspicion) quickly so appropriate measures can be enforced to minimize the risks of the breach.
Lastly, make sure to inform your immediate colleagues that your account is or may be compromised so as not to spread any more phishing attempts.
If You’re an Administrator: The key is to contain the malware and regain control of your Exchange 365 email account as well as its connected apps before retrieving any lost data. Here are some steps to follow to begin regaining control:
1. Regain Email Access
First, unwanted access must be removed and blocked from resulting in any more illicit activities that could cause your data to be compromised, stolen, or deleted. You can do this by:
- Reset user’s password. The new password must be strong and complex (with lower and uppercase, numbers, and special characters) and must be secured. Do NOT send the new password to the email of the intended user as you’re still in the primary step of regaining control over the email account.
- Remove suspicious email forwarding addresses. This would ensure you’re only allowing legitimate and trusted accounts to be sent emails. When you remove certain addresses, you’re not allowing those accounts to receive forwarded emails from the compromised account.
- Disable suspicious inbox rules. This would guarantee that no automated actions—such as automatically forwarding email messages to another account—are being undertaken as you fix the account.
- Unblock user from sending mail. If the attacker has used the email account to send spam mail, the mailbox will be automatically tagged by Microsoft as a restricted user and would not allow it to send any more messages.
- Block user account from signing-in. Until the account is safely secured with no unwanted access present, continue to block any attempt to sign into the account.
- Remove account’s administrative roles to avoid unwanted control over other accounts. You can do this via:

2. Check Integrated Apps
Exchange Online is deeply integrated into the other Microsoft 365 tools and syncs between apps and devices, so control must be regained in these areas.
Pausing syncs and updates would help contain the possible spread of data encryption. To accomplish this, you can:
- Disable Exchange ActiveSync for a mailbox to stop syncing data between devices and Exchange Online mailboxes.
- Pause OneDrive sync to hold updates of cloud data from infected devices.
3. Run antivirus scan
Now that any access to your mailbox is on hold, it’s time to check all suspected computers and devices (including ones that sync data) by running a full antivirus scan.
You can use two native Microsoft tools for detection and removal of malware:
4. Recover files and emails
Once it’s determined that your environment is safe from malware payload or unwanted access, you can now restore your data that’s either encrypted or deleted.
If your backup versions are safe, you can use:
- File History for Windows 11, Windows 10, Windows 8.1 to try to restore local files and folders.
- Files Restore in OneDrive for Business to restore your entire OneDrive to a previous point in time within the last 30 days.
In cases when all your email is deleted, you can still potentially recover deleted items by following this process.
Or, if you have a third-party backup solution, simply restore any file or email data from there.

5. Reinstate Access and Reenable Sync
Finally, you can unblock the user from signing in, reassign admin roles, and reenable your Exchange ActiveSync and OneDrive sync.
6. Report message to Microsoft
As best practice, it is encouraged to report the attack to Microsoft by sending emails, attachments, or files to help improve Microsoft’s email filters and avoid this from happening again in the future. You can do so by following these steps.
Moving Forward
With both the frequency of data breaches and the cost of ransom increasing, cloud security becomes a crucial business need to defend your data, users, and your whole organization against cloud risks.
It is therefore important to deploy not only the proper incident response strategy, but also to utilize tools that help mitigate risks and improve processes to detect and remove these types of malware in the easiest way and earliest time possible.
Here are some tools you should take advantage of to help strengthen security and easily recover should it happen (again):
- Defender for Microsoft 365 Automated Investigation and Response (AIR): Enhances security capabilities by automating quick detection of compromised accounts, limiting scope of the breach, and providing fast and effective response actions in cases of vulnerabilities with the help of compromised user alerts.
- Anti-phishing protection in Exchange Online Protection: With capabilities such as Spoof Intelligence, it is possible to block detected spoofed senders from external and internal domains and plan out automated response actions once detected.
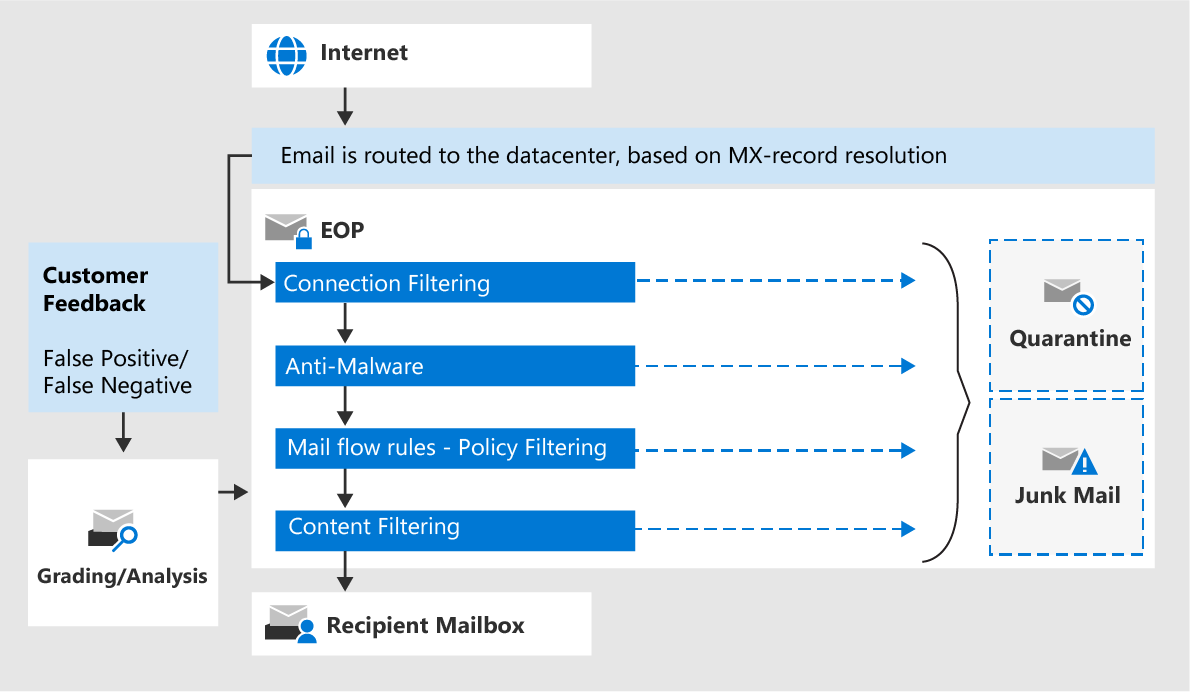
- Additional anti-phishing protection in Microsoft Defender for Microsoft 365
- Campaign views: Coordinated phishing attacks are detected via machine learning and other heuristics by identifying and analyzing involved messages in the entire service or organization
- Attack simulation training: A training resource where fake phishing messages can be created and sent to internal users to gauge your users’ awareness and readiness against possible phishing attacks
- Third-party backup solutions: Helps establish a secure databank where you can easily recover data that has been compromised or deleted. AvePoint’s Cloud Backup, for example, backs up to 4x a day to ensure multiple recent copies of your data are available even with various data loss risks, which helps sustain business continuity.
These, and following Microsoft’s best practices, can help you, your organization, and your users be more prepared and protected against these ever-growing attacks.
If you want to know more about how you can better protect your organization against ransomware attacks, be sure to check out our recent webinar, Ransomware: Prevention, Response, and Recovery.






