Learn how to govern your records in Office 365 with our free digital records management guide.
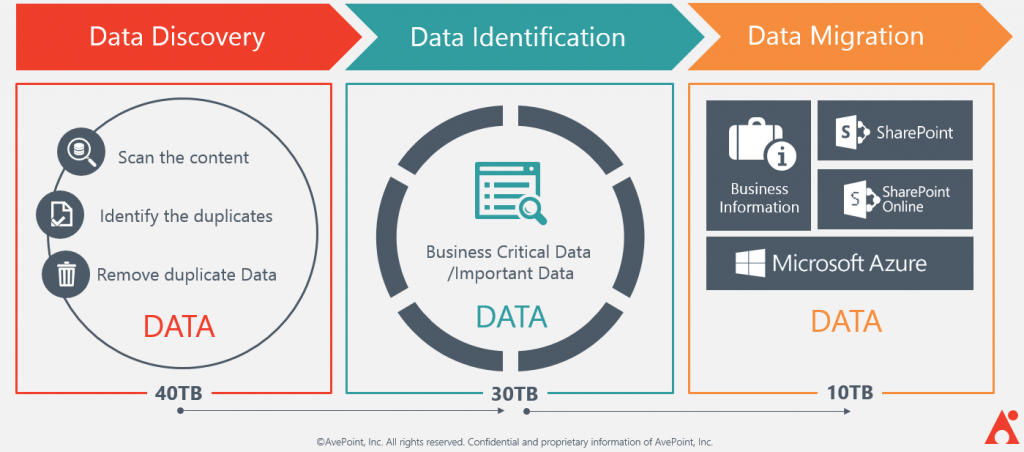
In one of our previous blog posts on Compliant Migration, we emphasized the importance of “scanning your data” before starting the migration process. This time, I’d like to home in on a component of our Compliant Migration process called file analysis which focuses on:
- Scanning all your files within a file share, SharePoint, or SharePoint Online
- Helping you understand what you have in terms of:
- What file types you have in your environment
- What permissions are associated with your files
- What metadata are part of your files and the value of that metadata
- Identifying duplication
- Identifying potential files that are good candidates to be archived
Tip 1: Less is more.
File Analysis’ ability to identify specific duplicate files allows you to:
- Save on storage, licensing, and data management costs
- Reduce potential exposure to risk and data breaches
- Reduce the time to backup/restore your data
- Reduce the time to complete your migration project by excluding duplicate items
Every individual or company creates duplicates throughout the typical workday, and as IDC’s CMO of Advisory Service says, “[Most collected] data is garbage. IDC’s group researchers say that some 80% of data collected has no meaning whatsoever.”
Another interesting quote from the IDG Research Service is “Only 28% of data stored today represents any value to day-to-day business.” My all-time favorite quote on data management, though, is from Forbes and reads “The average cost of data management is 3.5% of revenue.”
Having trouble managing your data in Office 365? This post might help: Click To TweetWhy should these words be top of mind for every CIO/CTO/CISO? If we take the above facts from IDC and Forbes and assume that your organization makes 100 million dollars a year in revenue, that’s approximately 2.8 million dollars spent on dark or duplicate data management.
The benefit of keeping everything makes us insure ourselves from fears that we may end up deleting something important (or maybe not so important).
Tip 2: Let it go.
Let’s face it: it can be as challenging to throw personal things away (many people keep their favorite belongings in the closet sitting there and collecting dust even though they are old or outgrown) as it is to delete data. In almost every compliant migration project we’ve helped our clients with, there has always been data that is a good candidate for archiving.
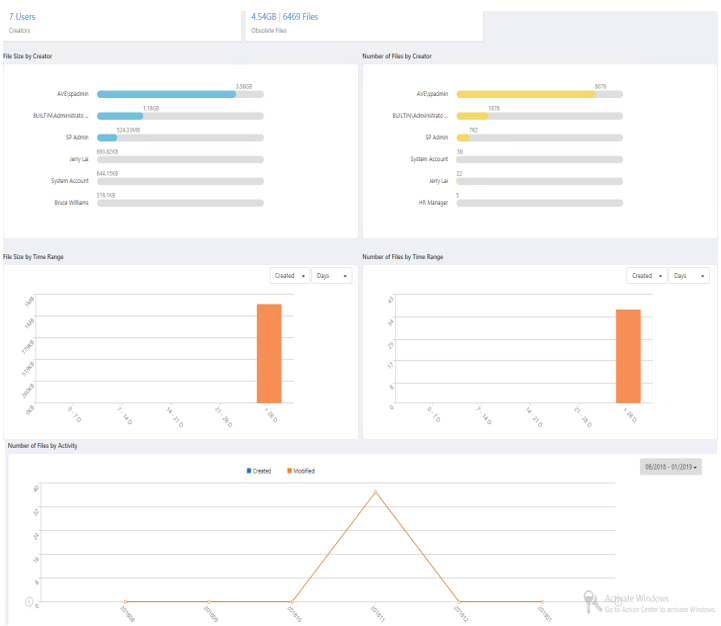
For example, if you haven’t opened a file in 3-5 years, there’s a high probability that you don’t need it anymore (unless it’s sensitive or has business value to your company). With AvePoint’s File Analysis, you can identify the dates of when a document was created, modified and accessed (if it’s configured and present). You can also scan the content of those files and figure out the content type, from a PowerPoint presentation to a product brochure to a purchase order; they’re all identifiable.
Tip 3: Identify sensitive data and who has access to it.
Gone are the days where 50MB of email space was the upper limit defined by your IT department. Back then, most of us had to create several email archives because one was simply not enough.
Another benefit of running a File Analysis over your network file share drives is the report which allows you to see what file types you have and who else has access to them. In the case of Outlook data files, it’s a case of identifying confidential/sensitive information (presumably in high volume/quantity). If the same file is shared with George or Bob from the neighboring department, then it’s even more of an issue.
One of the most interesting data breaches we’ve seen recently is the Oklahoma government data leak exposing 7 years of FBI investigations as mentioned by Forbes. More than 120GBs of archived emails and other file types were left unprotected.
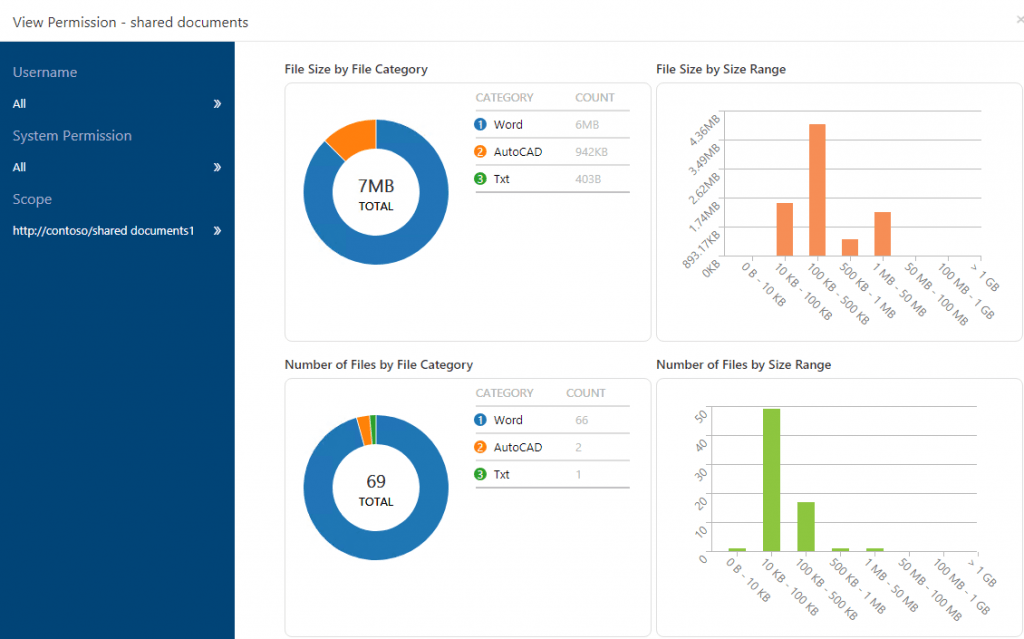
File Analysis can be your first step towards better data management by giving you insight on what you need to move, delete, protect, rearrange, and classify.
Additionally, File Analysis can be part of your information governance plan (which, of course, is a journey in its own right). Understanding whether people follow your company-approved data management policies is the first insight. File Analysis allows you to measure this; if you find torrents, the latest season of Games of Thrones, email archives widely spread across multiple locations, multiple duplicate files, or other illegal material, chances are your policies are not as effective as they are neatly written.
Finally, while File Analysis may be something IT would leverage on a regular basis, other departments could benefit as well. Legal could use it for the defensible removal of junk, compliance and risk departments could benefit from better access to controls and protection of sensitive content, and procurement departments wouldn’t need to purchase new hard drives or spend money as frequently.
Want to learn more about how to keep your data secure and efficiently managed? Find in-depth product details and request a full demo here!






