Create a culture of transparency, action and trust. Learn more about our award-winning compliance solutions here.
One of the best parts of my job at AvePoint is being able to help customers around the world with their privacy, security, compliance and data protection initiatives. GDPR was one of the more popular topics discussed this year, but there are still many organizations that are interested in or being challenged to adopt good security and governance best practices in order to keep their information assets secure.
ISO/IEC 27001 helps organizations prove that they have those practices in place. Speaking from work experience, I can attest to it being even more challenging to keep forward momentum after your organization has been ISO 27001-certified.
Although ISO 27001 certification is not mandatory, working towards it can help you get ready to meet data governance requirements for similar acts, laws, regulations and standards. Most of these share a common goal: protection of information and assets.
ISO 27001 Standard Controls
One of the most common questions organizations often ask is, “How do I get started with risk assessment?” Ideally, risk assessments should be part of Privacy and Security by Design or as part of project management under ISO 27001 Annex 6.1.5 which reads, “Information Security shall be addressed in project management regardless of the type of the project.”
First, you should start and agree upon your risk assessment methodology. Tailor the rules of how to perform the risk management assessment and follow a standard that you can replicate across your organization (especially if you have a global presence). Don’t forget to define what your risk scoring mechanism (severity vs likelihood) and risk level threshold are.
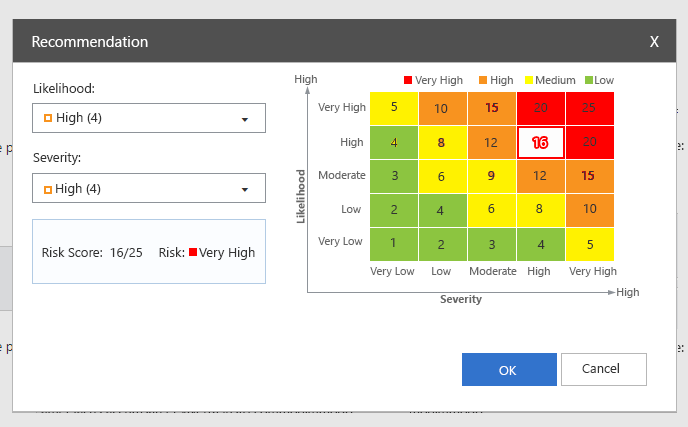
Once you have defined the methodology, the next step is to apply it across all the assets your organization has. This is tricky as it also requires you to have an Asset Inventory in advance as ISO 27001 mandates in Annex A.8.1.1. In most cases, organizations may not know or fully understand the risks associated with each of the ISO controls. Some questions to help get you audit-ready are:
- Is there an asset owner assigned to each asset?
- Who maintains the asset inventory?
- Is the asset inventory regularly reviewed?
- What is the asset’s retention period?
- What is the asset’s classification?
- How often is the asset/information backed up?
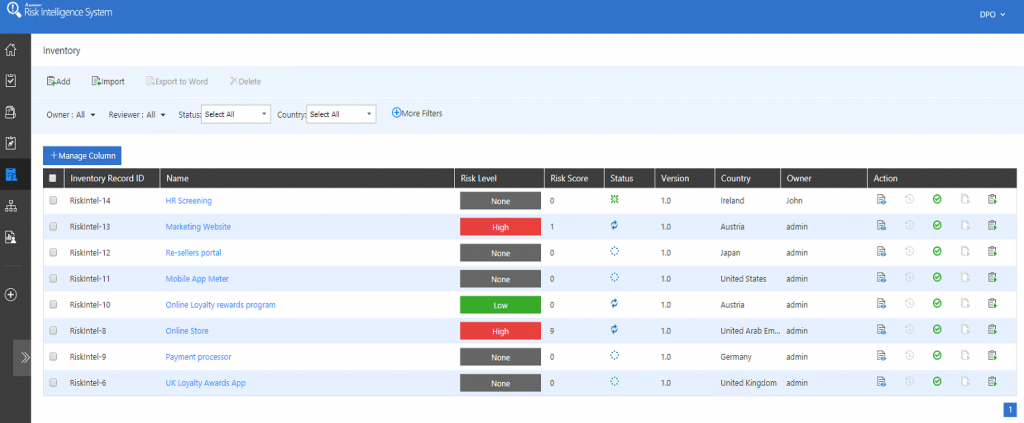
If you’ve done the first two steps, you should now have identified the gaps between the business expectations and actual situation of your information assets. Now it’s time to start planning your risk treatment or corrective and preventative action controls.
Applying security controls is one of your options to mitigate or minimize the risks, but you also have the option to:
- Transfer the risk to another party
- Avoid the risk by disabling the process or activity which is too risky (although the business may not be very happy about this)
- Accept the risk, which make sense if the cost and effect of mitigating the risk is higher than the actual potential loss or damage. With the recent changes in data breach penalties such as the GDPR (up to 4% of global revenue or up to 20Mil euros), however, accepting the risk can be quite the questionable decision.

Another common question when it comes to ISO 27001 requirements and controls is about data labeling or data classification. Annex 8.2.1 from ISO 27001 states that “Information shall be classified in terms of legal requirements, value, criticality and sensitivity to unauthorized disclosure or modification.”
The biggest challenge with information or data classification is finding the easiest, most efficient and accurate way to achieve this goal. Positioning this task to employees can sometimes be both time consuming and inaccurate.
In addition, not every employee is familiar with how to appropriately classify data. Data changes frequently, and it’s often hard to solely rely on untrained personnel to make sure classification is done according your company information classification policy. It’s not that you shouldn’t trust your employees, but it’s better to monitor and control how information is used throughout the organization.

Unintentional employee action is the most common cause of data breaches worldwide. In order to protect your assets, organizations need to classify what you have and, based on the value, apply appropriate security controls.
Not everything needs to be protected, but understanding what information you have, where is it, who has access, who is it shared with, what the retention period is, etc. is all part of a best practices data governance process.

AvePoint itself received ISO 27001 certification and has been able to meet many of the ISO 27001 requirements using our own Enterprise Risk Management (ERM) solution. We’ve been able to do things like:
- Automatically apply data classification to data at rest and any newly- created document based on sensitivity, document/information type and retention period.
- Identify non-conformities in the Incident Management Center
- Automate third party vendor risk assessments
- Evaluate security into contracts using Impact Assessments
Stay tuned for a more detailed blog post on our ISO 27001 certification process in the coming weeks!
If you’re just beginning your ISO 27001 certification journey or are performing your periodic ISO 27001 review and need a centralized solution to help you with automating some of the ISO requirements, consider AvePoint’s compliance solutions and feel free to contact us for more information.
Want more on data protection and compliance? Subscribe to our blog to stay in the loop.

