AvePoint is committed to testing against all known and published vulnerabilities. A recent announcement exposed a vulnerability in SSL v3 known as POODLE (Padding Oracle On Downgraded Legacy Encryption), which adds to a number of already known issues with SSL v2.
Should I be worried?
While this issue fundamentally isn't with our product, it does put content at risk when communicating between the user and our software. Communicating over SSL could result in a man-in-the-middle attack, which would expose user credentials, passwords, and other information submitted to our products. It’s important to remember that those who are most subject to this threat are typically accessing content over public Wi-Fi or other unsecure networks. Because our products are typically deployed in a data-center on closed networks– accessible only over VPN– the risk of data exposure is extremely low. If you have configured your management consoles or product interfaces to be accessible outside of the corporate firewall, remember that the interface is only used for configuration and does not pass data outside the firewall. Content from your SharePoint environment is entirely processed by our SharePoint Agents, and is not passed to the user through our consoles. Our Agents always negotiate communication over higher level protocols (TLSv1 or higher), so no SharePoint data will be intercepted by this attack. To illustrate this point, please refer to the diagram below: 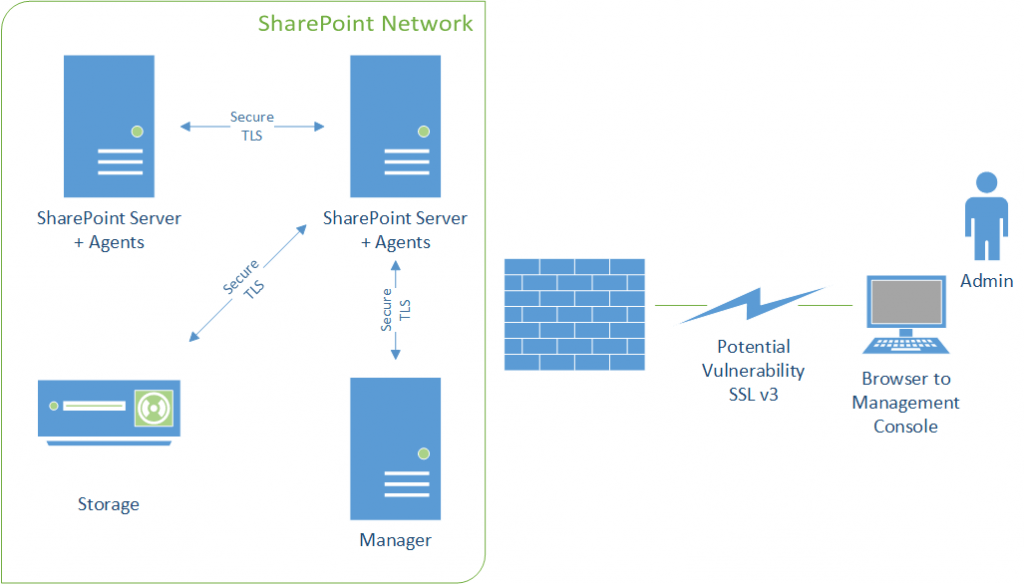
How does this affect AvePoint Online Services?
All AvePoint Online Services offerings have been configured to block any SSL v3 or SSL v2 connection for all products, including AvePoint Meetings, Governance Automation Online, Compliance Guardian Online, and DocAve Online. Your connection to these products should continue with no loss of functionality. Feel free to test our platform against any of the latest vulnerability software, or contact us for copies of our security reports: https://www.avepointonlineservices.com/.
How does this affect my AvePoint server-based products?
AvePoint on-premises products, such as Compliance Guardian, Governance Automation, and DocAve 6, all leverage Microsoft technology for communication. By default, the Microsoft Windows Security Provider and IIS are configured to accept connections over SSL v3 protocol, which means that you could establish a potentially vulnerable connection to the management interface of our products. You can take steps today to protect your environment. We encourage you to follow Microsoft best practices for disabling SSL in your environment on any management servers by modifying your registry:
- To disable SSL v3: https://technet.microsoft.com/library/security/3009008
- To disable SSL v2: http://social.technet.microsoft.com/wiki/contents/articles/2249.how-to-disable-sslv2-on-a-windows-server-2008-and-windows-server-2008-r2-domain-controller-dsforum2wiki.aspx
If you would like to take additional steps for security, you also can make these modifications on all agent servers. However, keep in mind that agents will always communicate over TLS and are not subject to this vulnerability. Our products will continue to operate with no loss of functionality.
How else can I protect myself?
As a user, we encourage you also to update your browser settings to disable SSL, ensuring no other applications you access are subject to this vulnerability. Additionally, when accessing corporate resources over public or unsecured networks, using a reliable VPN service can help protect your traffic. Many users prefer options that are both secure and affordable, such as a cheap vpn monthly plan, to ensure encrypted communication at all times. 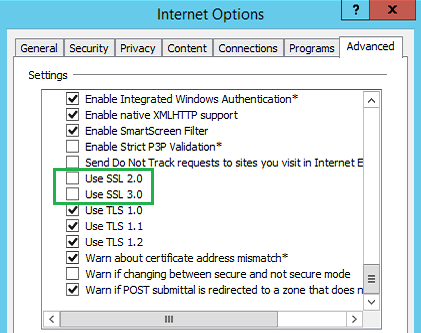
What about legacy AvePoint software? (DocAve v5, v4, etc.)
For customers on our Apache/Tomcat platforms, you will need to modify the Tomcat settings on the manager server under the “…\ZeusWeb\conf” folder. 1. Open the “server.xml” document in the folder above. Find the value of sslProtocol flag, which by default is set to “TLS”. Note that this means that SSL v3 is also enabled. 2. Use the service management tool to “stop” the Web Service: 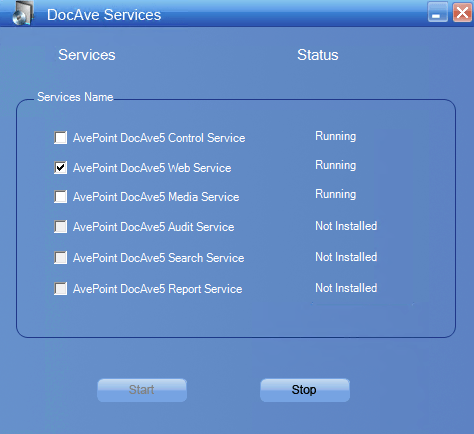 3. Add the argument sslEnabledProtocols=”TLSv1” to ensure that only TLS is used.
3. Add the argument sslEnabledProtocols=”TLSv1” to ensure that only TLS is used. 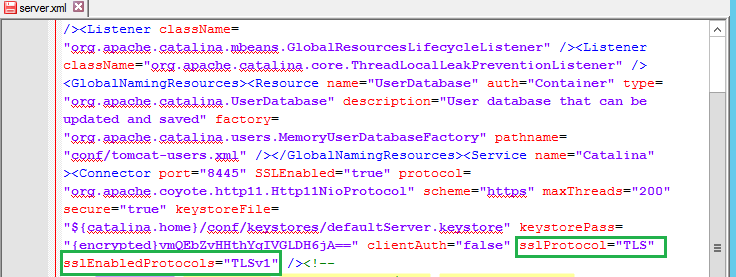 4. Save the server.xml file and set it to “read-only” to be sure no other tools modify or revert this change automatically. 5. Using the same service management tool, restart the Web Service. You should now be able to test this configuration change by accessing the management interface through a browser with only SSL v3 enabled and seeing the failed connection.
4. Save the server.xml file and set it to “read-only” to be sure no other tools modify or revert this change automatically. 5. Using the same service management tool, restart the Web Service. You should now be able to test this configuration change by accessing the management interface through a browser with only SSL v3 enabled and seeing the failed connection.
What if I have questions?
If you have any questions, please contact us at support@avepoint.com.

