Modern Work Needs Modern Insights and Efficiency
Today’s modern organization understands clean data is crucial to their success. However, they struggle to oversee vast amounts of data across multiple collaboration platforms. AvePoint’s Control Suite provides actionable insights, automates data governance, and proactively enforces policies to reduce security risk, optimize operations, and ensure compliance.
Discover, Secure and Comply
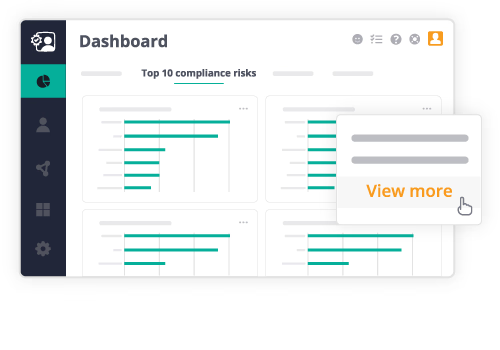
Identify and fix employee and guest access to safeguard your modern SaaS platforms.
Transform Data Governance
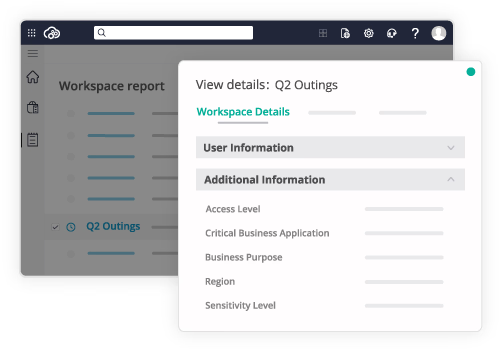
Provide a secure yet frictionless experience with a scalable support and data governance framework.
Efficient, Modern Operations
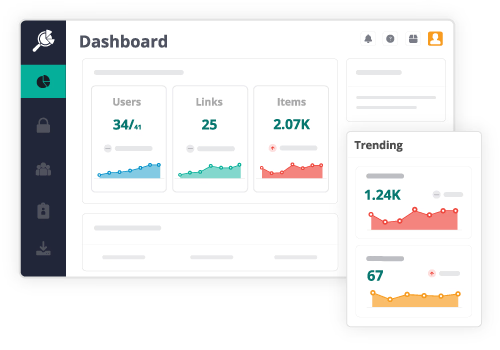
Automate IT operations to support collaboration at the speed and scale of today’s workplace.
Your Keys to Modern Insights, Efficiency, and Control
The New Dream Team: IT and Security
Explore Solutions that Align IT and Security Leaders
IT Leaders
Drive Modern Work with Scalability and Control
Security Leaders
Eliminate Risk and Increase Your Security Posture
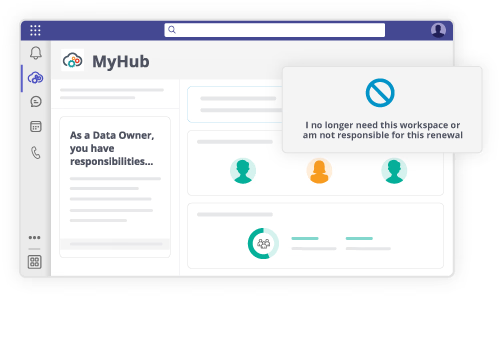
Give teams one hub for messaging, sharing, and tasks with flexible yet secure settings. Strategically manage software licenses in real-time to optimize value of technology investments. Empower managers to configure permissions balancing team needs and security. Maximize every dollar spent through oversight and strategic allocation of subscriptions.
Gain visibility into user access of sensitive data to identify vulnerabilities. Bolster defenses with automated policies to safeguard critical assets. Continuously prove compliance with protocols in sync with changing internal guidelines and external regulations. Remove compliance exposure by seamlessly upholding security and permission setups.
The AvePoint Control Suite Difference

Simplify Workplace Operations with One Trusted Platform
Today's workplaces rely on numerous complex cloud apps and platforms. Managing it all brings data governance and security challenges. The AvePoint Control Suite can handle all your essential needs at once. Automate governance across SaaS apps, manage licensing and budgets, empower users with scalable policies, secure data by controlling access, and protect from cyber threats. Achieve efficient, sustainable operations and confidently oversee a workplace full of diverse technologies and workspaces.

Centralize Your Workplace Management
The nature of your workplace is complex and distributed, with data residing in multiple workplace tools. Why turn to different technology companies to gain actionable insights, automate data governance, and proactively enforce policies across them all? With the Control Suite, reduce security risk, optimize operations, and ensure compliance without undergoing numerous security reviews, complicated pricing, and multiple points of contact.
Take the Next Step to Win Today’s Workplace
Support every stage of your digital workplace transformation with the AvePoint Confidence Platform.
Modernization Suite

Bring all your data together and build business processes that transform employee experience.
Resilience Suite

Secure your data, manage information lifecycle, and prevent breaches to eliminate risk.
Control Suite

Gain complete visibility across your digital workplace and scale your data governance framework and operations.
Trusted by the World’s Leading Organizations
Griffith University
We attempt to limit the restrictions we place on how people use Microsoft 365. Our goal is to manage growth and reduce the size of the tenant, so we are only managing active content and active workspaces. AvePoint lets us have that vision, but also enable critical governance.
Senior Information Solutions Analyst, Griffith University

Microsoft 365 sites disposed