How to Achieve Zero Trust Standards Without Limiting Collaboration in Microsoft 365
Learn how to develop a security strategy to build a safer and smarter digital collaboration workspace.
Don’t leave data within your collaborative workspaces vulnerable
When building your Microsoft 365 Zero Trust deployment plan, ignoring workplace tools like Microsoft Teams or SharePoint could be a dangerous pitfall to your security. For most organizations, these spaces are where work gets done, yet controlling who has access to what is not always top of mind. Left unchecked, you could end up with overprivileged users, unsecured collaboration spaces, and an exponential increase in risk.
Agencies must acknowledge that threats must be countered both inside and outside their workplace network, and a breach (which we have seen firsthand - from a malicious insider stealing and selling secrets to a negligent employee unintentionally compromising their own credentials) could result in your team losing the very collaboration platforms that have increased productivity and enabled flexible work.
Deploying Zero Trust Security in Collaboration Platforms
To avoid the perils of an unsecured workspace, agencies must review their security model to identify gaps and implement additional protection measures aligned with Zero Trust principles: least-privilege access, verify explicitly and assume breach.
In this guide, you’ll receive comprehensive, expert strategies to deploy Zero Trust security in your collaboration platforms, with real-world examples and actionable solutions to better protect your digital workspaces. The guide will cover:
- What is Zero Trust Architecture
- Implementing Zero Trust in Workplace Tools
- Microsoft's native security tools and Zero Trust
- FedRAMP-authorized solutions
Getting Started: Zero Trust Cloud Security
While there is no single solution or technology that will allow you to fully secure your data in Microsoft 365, there are several strategies that can help you build a more robust security framework and reinforce the government’s defenses against increasingly sophisticated and persistent threat campaigns.
Download this free guide to learn how you can develop a security strategy to build a safer and smarter digital workspace.
Table of Contents
Get a Sneak Peek
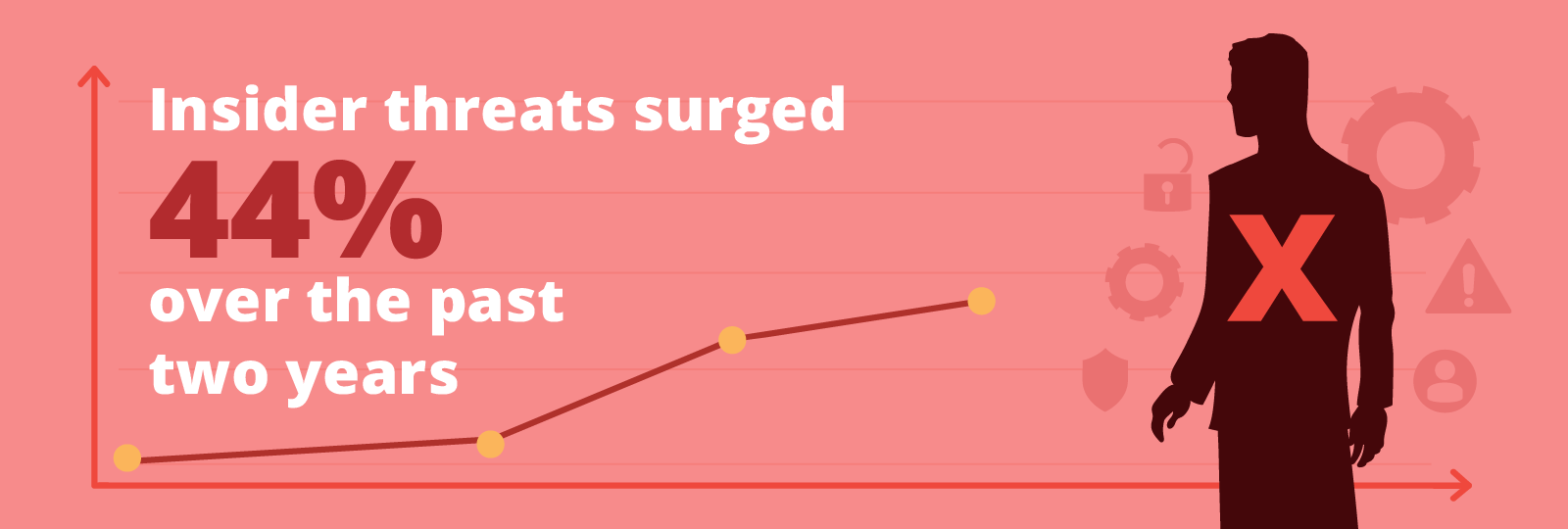
Historical digital security approaches are antiquated and ineffective
The beauty of modern collaboration tools, such as Microsoft 365, is that your team can work from anywhere, on any device; but this is its own curse. This flexibility opens the door to remote users, “bring your own device” practices, and more people working in shared, non-private spaces, introducing new vulnerabilities and risks. The assumption that anyone on the inside of your network is trusted and anyone on the outside is not outdated. Under traditional security practices, these insider threats are free to access and infiltrate your sensitive information due to a lack of granularity in security controls. (pg.3)
Utilize delegated administration to unburden your central IT
Many agencies work with government contractors, who may add or remove staff to projects frequently. Traditionally, the central IT organization in charge of the tenant would be burdened with the responsibility of managing these personnel changes, creating users, managing licenses, and deleting old users. With delegated administration, these onboarding and offboarding duties can be distributed to the contractors’ staff, who are better suited for the responsibility. (pg.7)
Improve identity management with better insights into external collaboration
Control external collaboration by leveraging guest access in your M365. Controlled at the individual user level, guest access provides people from outside your organization with access to content inside your Microsoft Teams – such as the channels, chat threads, and shared files – without costly additional licensing traditionally required to add users. Your internal team can collaborate with external users while you continue to maintain control and security over the shared information within your environment. (pg.11)
The new security standards don’t equal new security budgets
The right solution for you will improve efficiency and security while being cost-effective. After all, while a more robust security model is necessary, a more robust budget isn’t necessarily following; to balance your need for increased protection with other priorities, you need to find a solution that delivers more. With migration, backup, security, management, and governance solutions all in a single, SaaS platform, AvePoint can help you meet Zero Trust security standards while taking advantage of all the benefits Microsoft 365 has to offer. (pg.18)
More Similar Resources to Explore

