The evolving nature of work has exponentially increased entry points for data loss, rendering traditional perimeter-based security approaches obsolete. Organizations must recognize that their current data loss prevention (DLP) strategies may have critical blind spots, making data loss not just an IT problem but an existential threat to business continuity.
Beyond the immediate financial impact of data breaches or losses, organizations face unprecedented regulatory scrutiny, with global privacy laws imposing severe penalties for data protection failures.
The reputational damage from data loss incidents can destroy customer trust built over years, while the operational disruptions — experienced by 45% of organizations surveyed in a Gartner study — can bring business operations to a complete halt, or lead to business demise in dire cases.
Our previous blog post discussed how frequent, small data loss events can have a huge business impact, exposing the hidden risks they present. In this final installment of our four-part blog series on rethinking your business continuity and disaster recovery (BCDR), we arrive at a powerful conclusion: the best data recovery is no recovery at all. We provide an overview of the Shared Responsibility Model, the limitations of backup solutions, and how a platform approach ensures comprehensive and consistent protection of critical data, making recovery unnecessary.
Cloud Data Protection: Where Provider Security Ends and Yours Begins
The Shared Responsibility Model is a fundamental concept that delineates the division of security and compliance obligations between cloud service providers (CSPs) and their customers. This model is crucial for understanding how to effectively protect your data in a cloud environment.
CSPs like Microsoft, Salesforce, Google, and AWS are responsible for the infrastructure that supports their services. To establish a robust foundation for their customers’ data and applications, they need to address the physical and operational aspects of their responsibility (shown also in Figure 1). The physical aspect includes:
Security of their data center facilities
Hardware failure
Power outages
Protection of their infrastructure against natural disasters
The operational aspect, on the other hand, covers the following:
Software failure
Accidental deletions
Excessive permissions
Unsecure sharing links
Security of external workspaces
Configuration errors
Accidental data exposure through agents or copilots
Malicious prompt engineering
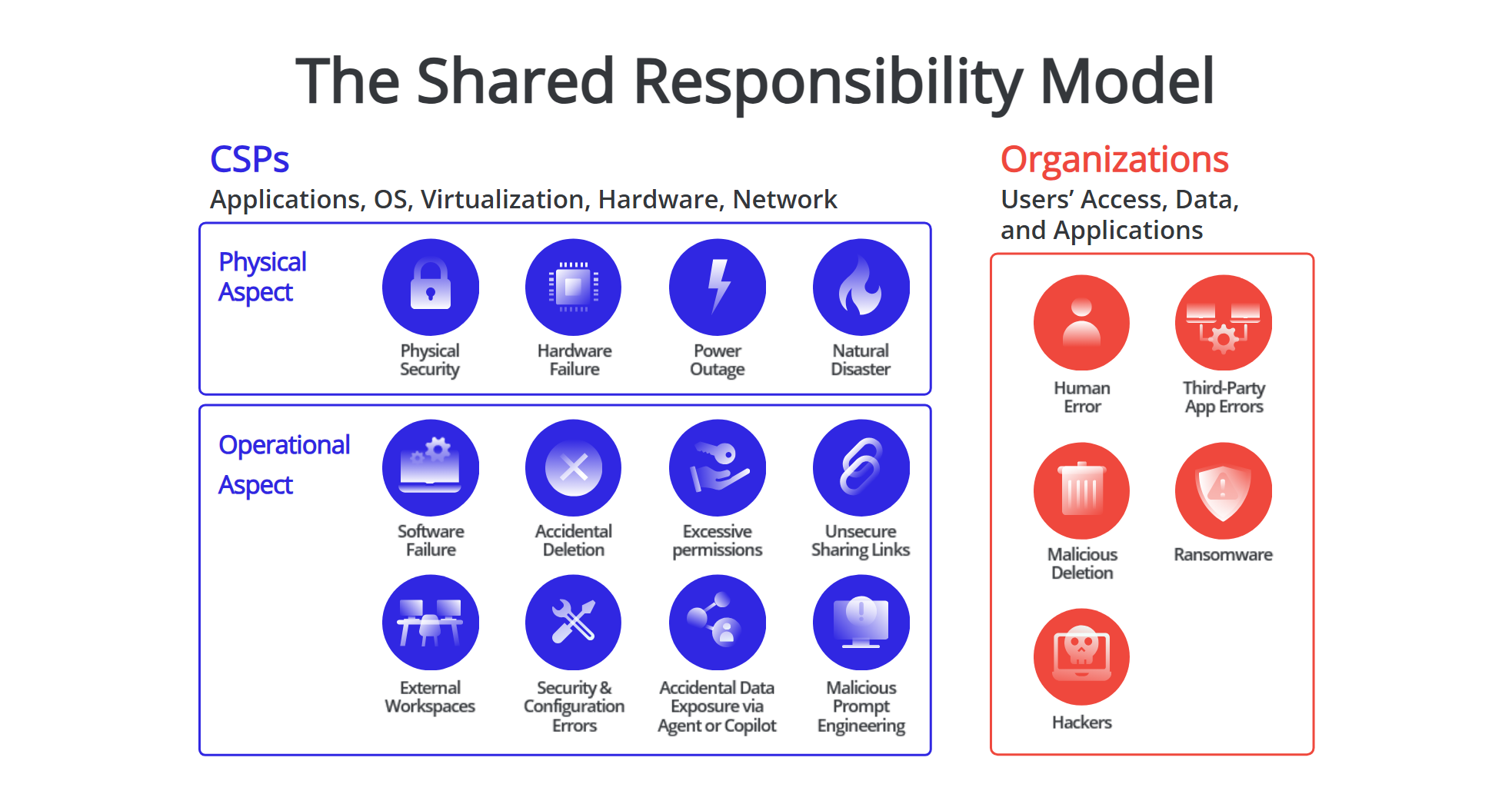
CSPs are responsible for securing their infrastructure, but customers are equally responsible for protecting their data and digital environment. This includes addressing risks like human errors, accidental or malicious deletions, ransomware, third-party application errors, and other cyber threats. While CSPs secure the cloud infrastructure, customers must secure their data, systems, applications, and user access and permissions within the cloud.
By embracing the Shared Responsibility Model, businesses can better prepare for potential data loss incidents and implement data protection strategies to mitigate risks that fall under their purview.
The Limitations of Backup in Preventing Data Loss
The “loss” isn’t just about deletion or corruption; it’s also about theft. The only way to prevent that is to limit and control access, understand your risk exposure, and appropriately label and classify your data.
If you skip these steps, your data isn’t just vulnerable to deletion — it’s also ripe for theft. When your sensitive data is stolen, it doesn’t matter if you can restore your secret recipe or proprietary data; everyone knows it now. At that point, your backup and recovery strategy won’t save you from paying hefty fines and potential lawsuits, especially if that data contains personally identifiable information (PII). Remember, once your secret sauce is out, it’s out for good.
Relying primarily on backups for data loss prevention is like having a fire extinguisher but no smoke detector. Backup solutions help recover data post-incident but cannot prevent unauthorized access or data exfiltration.
A backup solution is not designed to stop cyberattacks. For example, the account hijacking campaign in late 2023 compromised hundreds of user accounts in multiple Microsoft Azure environments, including those of senior executives, enabling malicious actors to exfiltrate sensitive data using stolen credentials. While backups are crucial, enterprises need other measures to address vulnerabilities that make data breaches possible in the first place.
In summary, backups are inherently reactive and deployed only after data loss occurs. To minimize significant gaps in protection, implementing a comprehensive strategy that includes robust security controls, information lifecycle management, continuous monitoring, and automated protective actions is necessary to safeguard your data effectively.
A Good Platform Makes Your Data Loss Protection Strategy Even Better
Adopting a holistic platform approach such as the AvePoint Confidence Platform significantly mitigates data loss risks and strengthens your business continuity and disaster recovery (BCDR) strategy. With a comprehensive platform approach, you gain the following benefits:
1. Gain Insightful Recommendations on Your Data Workspaces
Acquire the capability to analyze enterprise data and workspaces using comprehensive analytics to effectively get recommendations for managing user accounts, roles, and permissions. Doing so helps ensure data security and integrity. In addition to these basic analytics, the Confidence Platform provides a deep understanding of user and workspace behavior, so you know where your most important and high-traffic work is happening.
2. Easily Assess and Manage Risks in Your Environment
To find, prioritize, and address risks in your environment, the platform enables centralized reporting on your tenant’s security in near real-time and identifies high-risk action items that require further action. You get aggregated sensitivity and activity data across the tenant, prioritizing critical permissions issues and providing actionable reports to mitigate risk. Eliminate risky link sharing, lock down excessive permissions, and recover from configuration drift with the Confidence Platform.
3. Save on Storage Costs
By eliminating redundant, obsolete, and trivial (ROT) data, a comprehensive platform reduces backup and production storage costs. An AI-powered information lifecycle management, a core component of the platform, not only optimizes storage but also enhances data quality, which is necessary for achieving quality AI outputs.
4. Ensure Timely and Reliable Backups
Systematically removing redundant, obsolete, and trivial (ROT) data reduces production and backup costs, ensuring timely backups despite rapid data growth. A 2024 Dell study found that 62% of organizations cited rapid data growth as a significant challenge negatively affecting their ability to achieve timely and complete backups. The Confidence Platform saves you this trouble by ensuring backups meet Recovery Point Objectives (RPO) and Recovery Time Objectives (RTO), minimizing downtime and enabling swift business resumption.
5. Automate Security and Policies to Secure Your Data with Less Overhead Cost
Rising management and overhead costs associated with backup are a common pain point for businesses of all sizes. This ongoing challenge can be effectively addressed through automation, which alleviates the burden on IT teams by handling routine tasks. As a result, IT professionals can redirect their efforts towards more strategic initiatives that drive business growth.
The Confidence Platform automates policy enforcement to continuously monitor and resolve deviations in your workspaces, ensuring compliance with corporate standards. It streamlines lifecycle management through automated workflows and owner recertification, keeping both data and workspaces secure and organized. Newly created users and workspaces are automatically classified and assigned the appropriate levels of data protection and security.
Boost Your Data Resilience with AvePoint
The platform approach offers a full suite of tools that significantly minimizes the need for data recovery by proactively securing and managing your data and workspaces. By integrating robust security controls, continuous monitoring, and automated protective actions, businesses can prevent data breaches, unauthorized access, and accidental deletions before they occur.
The platform’s holistic approach ensures that data is consistently protected, reducing the reliance on reactive recovery measures. Additionally, features like AI-powered data classification and ransomware detection, leading-edge granular recovery, and automated policy enforcement further enhance data security and integrity.
By adopting the AvePoint Confidence Platform, organizations can transform their data loss protection strategies, making recovery a last resort.
To know more about how the platform approach can elevate your DLP approach, join the free AvePoint Innovates webinar on January 28.


