Read our other Microsoft Ignite recaps below:
- Satya Nadella’s Keynote: Business Trends & The Metaverse
- How to Protect Sensitive Microsoft 365 Data With Data Loss Prevention
- 4 New Microsoft 365 Hybrid Work Features on the Horizon
- 6 Things You Need to Know About Microsoft Teams Connect (Shared Channels)
Failing to establish strong security and privacy policies can lead to unimaginable damages for any organization. However, users are now generating more personal data than ever before when switching between personal and work devices and networks. In this Ignite session, Microsoft introduced a new privacy tool that will help admins and even end-users easily mitigate risks and maintain strong compliance inside and outside of their organization.
Current Privacy Challenges
As the amount of personal data generated increases, the risk of data breaches increases accordingly. There were reportedly over 800 data breaches just in the first half of this year, which already made up 3/4 of all breaches for the entirety of 2020.
With these alarming numbers on the rise, there are more global privacy regulations and standards being implemented to help organizations up their security. 129 out of 194 countries already have such regulations to protect data and privacy rights. Moreover, it’s predicted that by 2023, 65% percent of the world’s population will be covered under modern privacy regulations, up from a 10% today.

Privacy affects all of us from a single identity to the biggest organization there is. Organizations and businesses should be more careful in handling private customer data and information to maintain and grow customer trust. However, achieving strong privacy management is not easy. Here are the three key challenges organizations face that Microsoft wants to rectify with this new privacy tool.
- An inability to identify and effectively manage personal data – Some organizations still use a manual/traditional approach to data mapping such as the use of spreadsheets, e-mail, and in-person communication.
- The lack of context around the use of that data and visibility into associated risks – There are proper flow or action plans for those collected data to mitigate risks.
- Having to manually manage subject rights requests – They need solution that can help automate processes and requests at scale to save resources and time.
What is Privacy Management for Microsoft 365?
Privacy Management is a tool that can be accessed from the Microsoft 365 compliance center and delivers a modern way to manage and achieve privacy requirements. Key features include:
- Discovering data automatically instead of using surveys and providing visibility for possible risks.
- Providing actions to take to mitigate critical privacy risks
- Helping organizations to take a proactive approach to privacy
The following features of the Privacy Management tool respond to the three key privacy challenges mentioned above.
1. Visualize and Gain Insights
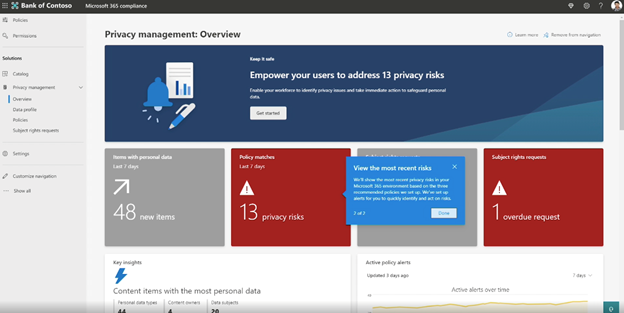
As an admin, in the overview dashboard, you will be able to have a view of your organization’s privacy posture. You can see how much personal data (social security numbers, credit cards, etc.) exist in your tenant, where they are located, and how they are being moved. Additionally, you can see a comprehensive view of key trends, policy matches, and the associated risks.

From there, you can have a granular view of what data you want to see in detail. You can filter the list based on your needs, such as data fit for public access as shown below. Owners are even anonymized to maintain privacy.
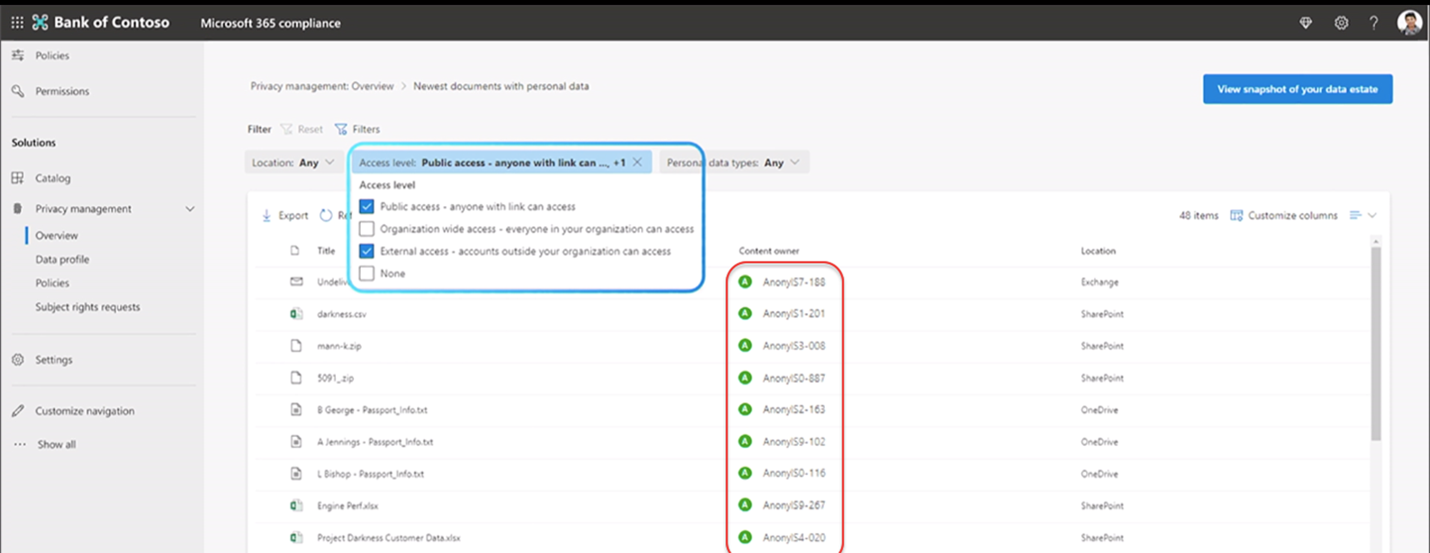
On the data profile page you can easily see the type and volume of personal data, where the data is stored, and a breakdown by location.
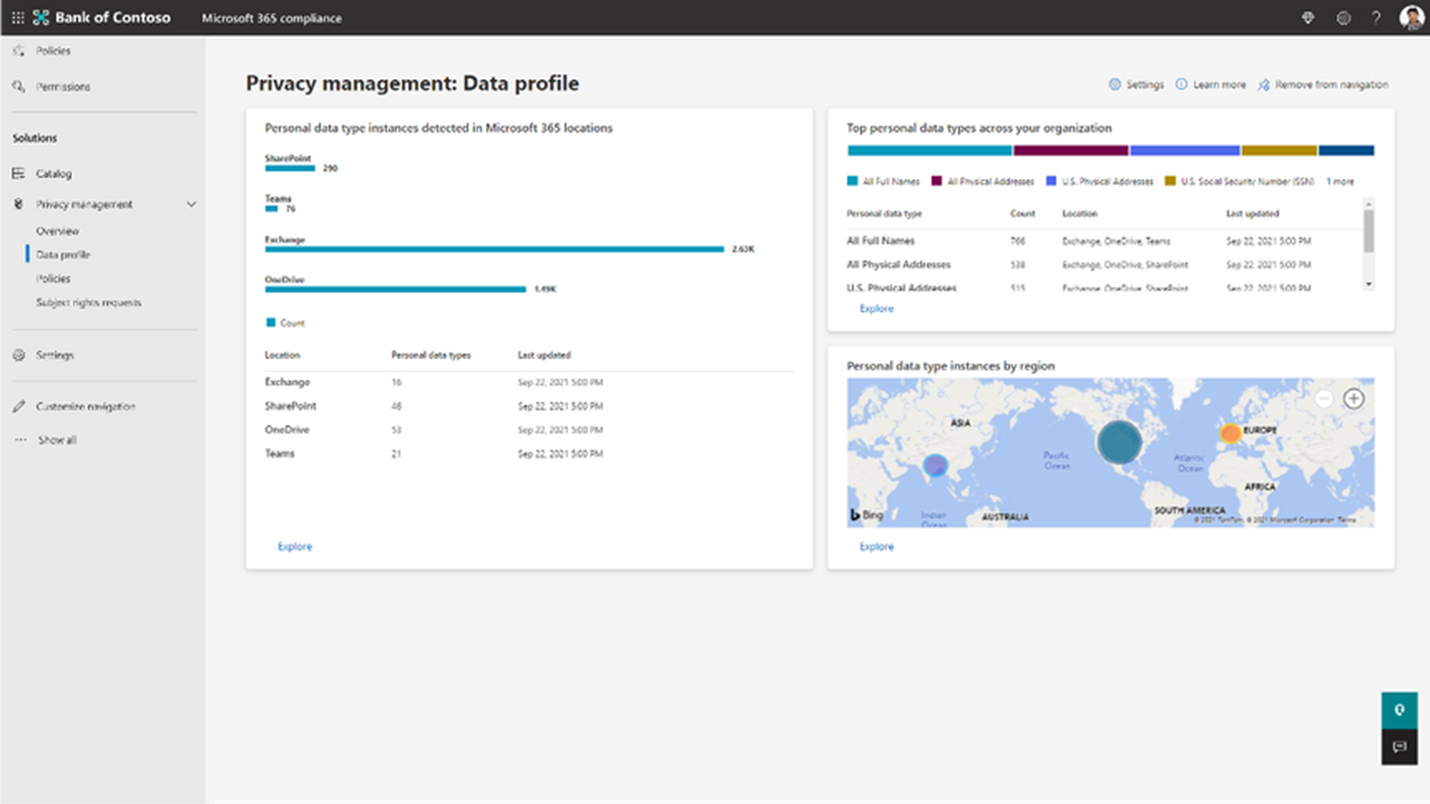
2. Empower Employees to Make Smart Data Handling Decisions
The red tile in the Overview tab shows privacy risks in the organizations that are from three different categories of privacy risks.
- Data minimization – Identifying content that contains personal data and is not used for a long period of time.
- Data overexposure – Identifying content containing personal data that may be overshared or exposed.
- Data transfer – Identifying personal data that’s moved across boundaries, inside and outside of the organization.
From this alert, you can see more details about the risk (why was this data flagged in the first place?) and take immediate action from the dashboard, either removing the access, deleting the document, or applying the appropriate label to the document. Moreover, you can also notify owners and let them take the next action.
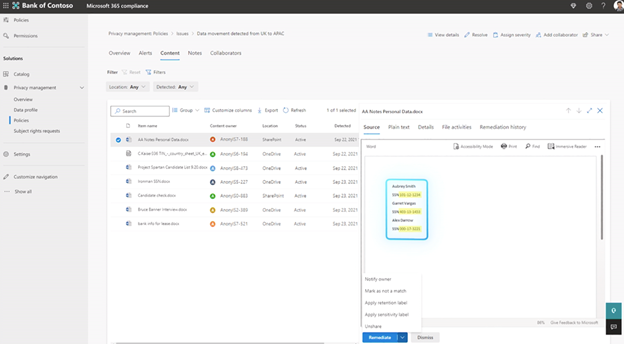
To allow users and owners to take immediate action regarding their data, you can notify them of possible risks or create policies that they need to comply with in order to move forward. As seen in the animation below, personal data has been blocked in Microsoft Teams by the policy applied. The user needs to provide business justification to comply.

Here’s another example of a privacy in place policy for data overexposure. The data owner has received an email digest about a file that might has been maliciously accessed. The data owner can take the action right from the email in Outlook.
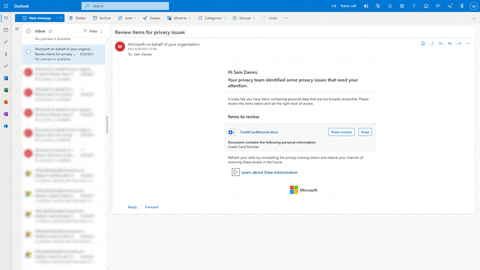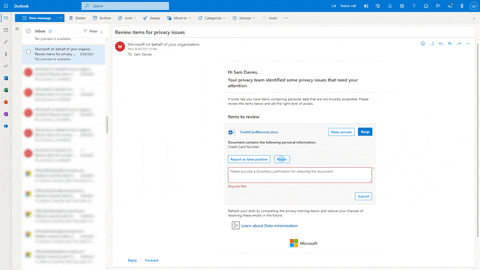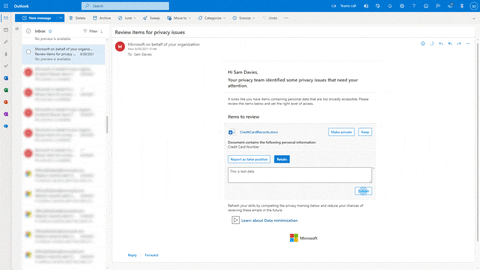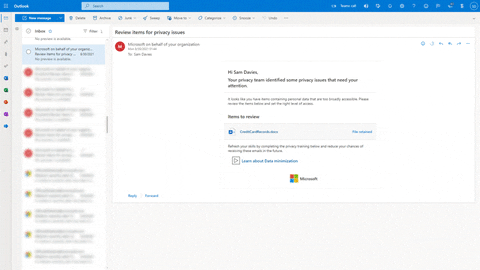
These policies can be implemented and used in just a few clicks with templates. They can also be customized with over 100 options such as scoping a policy to a specific location and adding training links and resources present in your environment.
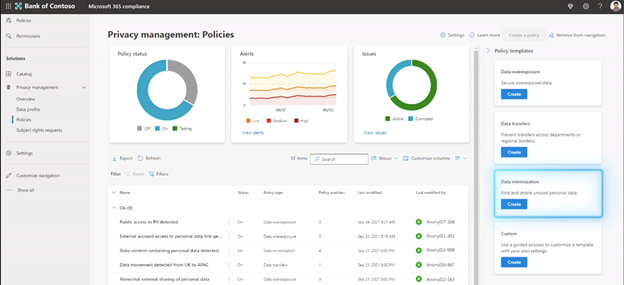
Afterwards, you can see how many users are taking the suggested actions and how your policies are working in the organization.
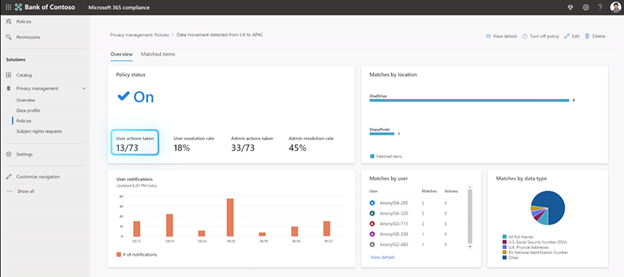
3. Data Subjects Rights Requests
Privacy Management allows admins to automate and manage data subject requests at scale in just a few clicks.
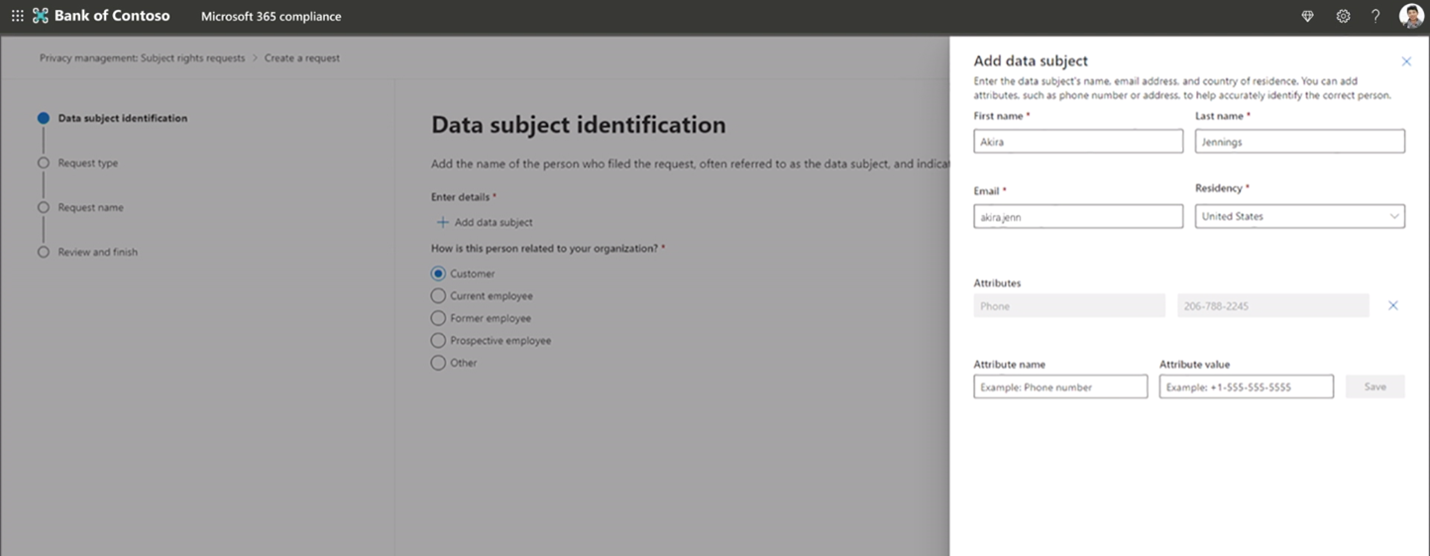
After entering the user’s important details, you can also add some personal attributes such as a nickname and address. Afterwards, you can indicate specific regulations, provide the name and description for the request, and it’s completed!
Afterwards, you can see all requests as well as detailed information about each request like what’s already been done and which actions need to be taken next. Moreover, you can integrate this process with other solutions such as ServiceNow to track progress or set calendar reminders.
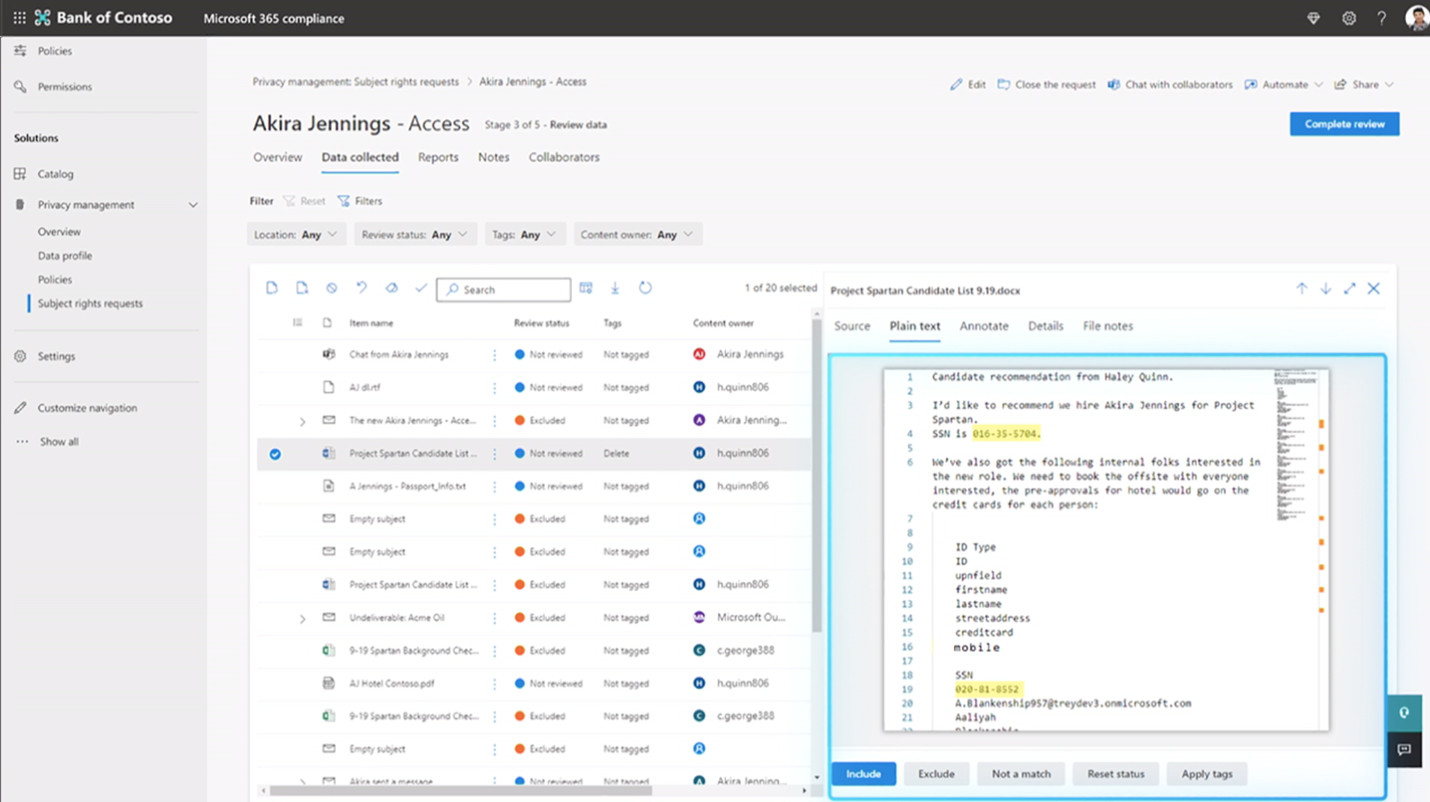
This is a powerful privacy solution that should help admins establish a strong security posture in their organization. This tool can be accessed from the Microsoft 365 compliance center with a Microsoft 365 or Office 365 license. That said, a solution like this has also been offered by AvePoint for a while now: Policies and Insights. This can be implemented not just on a document level but also on a workspace level, providing an even wider range of privacy options. Learn more about its features in this blog post or request a demo today!






