(Note: This post was co-authored by Chief Compliance and Risk Officer Dana Simberkoff and VP of Product Management for Global Accounts John Hodges.)
We live in a data driven society with globalizing economies, data transfer, and ubiquitous access to everything from everywhere. At the same time, we have seen an influx of compliance and data security stories flood news outlets. From Facebook to Google Glass, NSA to Verizon, there is an ongoing balancing act of sharing information that we choose to share with whom we choose to share it, and at the same time protecting information we wish to keep private. Living in our increasingly social world has and will continue to present a paradox with personal privacy – information placed on the internet and available publicly can be used in unintended ways regardless of your original intent. Information workers are now exposed to technology that blurs the line between public and private data within their own organization, easily sharing information over Lync, Yammer, Office 365, and other social collaboration systems.
Whether personally identifiable information (PII), health information, financial data, contract information, research and trade secrets, intellectual property, or contract data, information has become a new kind of “currency”. Companies like Google and Facebook have become multi-billion dollar organizations by offering “free” services that attract their users to provide this kind of information so that they can then share it with paying sponsors and advertisers. However, when shared inappropriately – whether by accident or breach – disclosure of sensitive data can have dramatic financial impacts on an organization and erode consumer trust. Trust is something that businesses must work to establish with their customers every day. Once lost, it is very difficult to regain. For this reason, we at AvePoint developed technology that captures data loss as soon as it occurs, releasing real-time reporting for systems including Microsoft SharePoint, Office 365, and Yammer with Compliance Guardian Service Pack (SP) 3, which is generally available as of this week.
When asked to give one piece of advice about how companies should improve their privacy and data protection programs in 2015, we suggest that you begin to think about privacy and security protections in a new context – that of “Crime and Punishment”.
As in the novel by Fyodor Dostoyevsky where the protagonist commits a crime with the idea that he will use the money he has stolen for good, businesses must understand that the ends simply do not justify the means. They must maintain transparency with their customers about how they will use data collected from them, but also be accountable for any lapses in those practices. Companies must not only build policies around protection of data, but also follow through with reasonable security measures. If they do not, there must be consequences – whether imposed internally or in the public eye.
What is reasonable security? It starts with a true understanding of what is important to you as a company and what controls you are putting in place to protect it. Information in the right context, such as in a team site secured for HR use, is a valuable asset to the company. Because of this, Compliance Guardian provides context-based checks, with the ability to change security based on the classification of the information being uploaded.
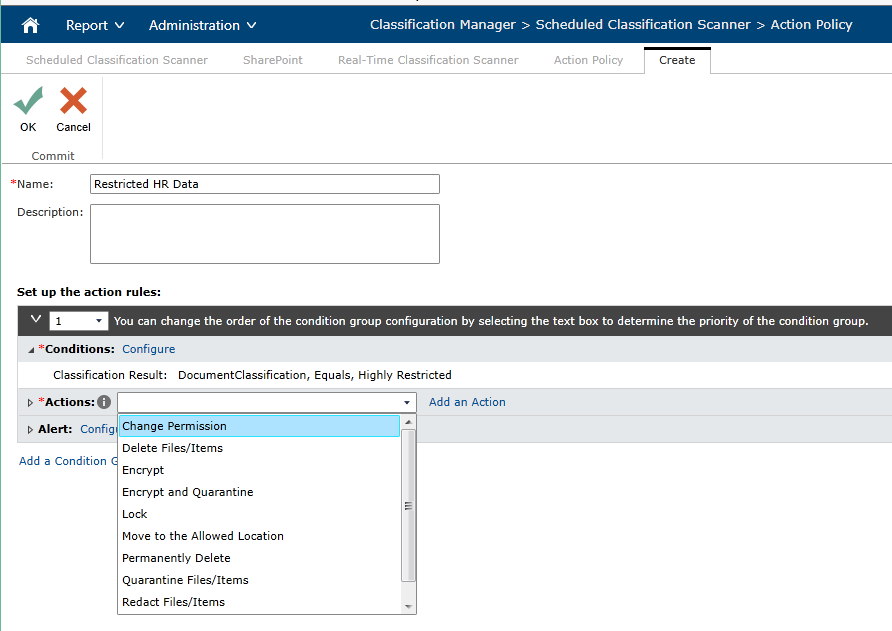
But, let’s say that information finds its way out of these secure zones. How can you recover quickly if you are breached? Compliance Guardian can now not only produce a forensic report of the audit and security information for the exposed data, but will also provide a full archive and history of any Lync or Yammer conversations for future eDiscovery needs.
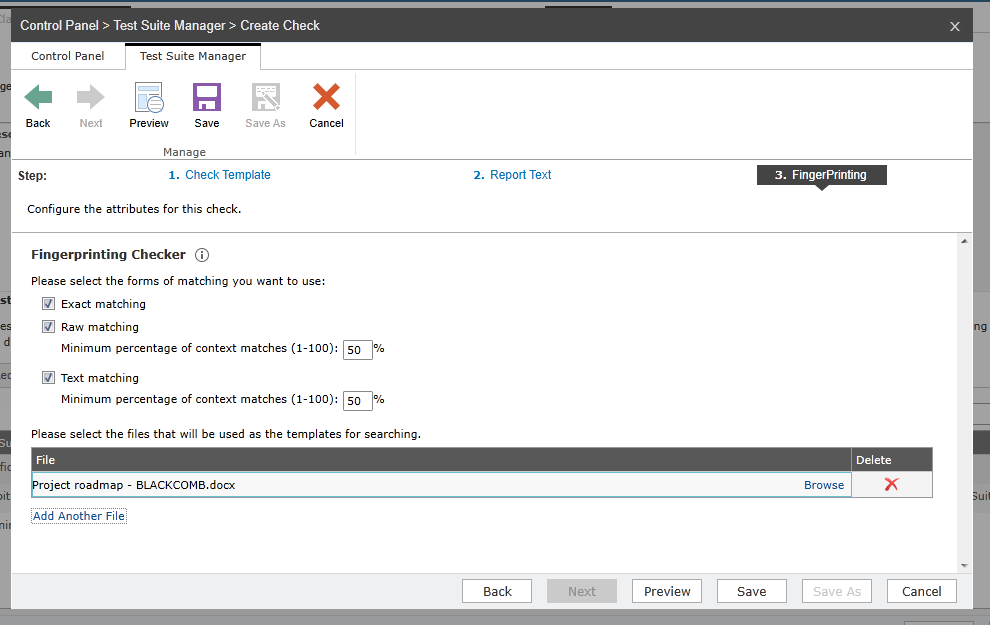
Many companies conduct annual privacy and security training. However, try to think of ways in which you can build an ever-present sense of privacy and security awareness into your employees’ daily activities. Automation can help educate your employees by reinforcing “good behavior” and identifying mistakes as they happen – building privacy and security by design. Compliance Guardian’s classification policies are designed to help users find out how their document should be tagged and secured, even when they are unsure. Our computer-assisted tagging can now also use Document Fingerprinting to identify known templates and identify potential exposure of sensitive information. Don’t leave it up to mere education to ensure your users to do the right thing!
By investing in compliance technologies, companies can turn what was previously considered to be a “cost to the business” [security, privacy and Data Loss Prevention (DLP) technologies] into a corporate asset. It’s very important to understand just how much risk you have in your organization today. Knowing you could be on the hook for millions of dollars in fines is important to understand at every level of the organization. This is the “punishment”.
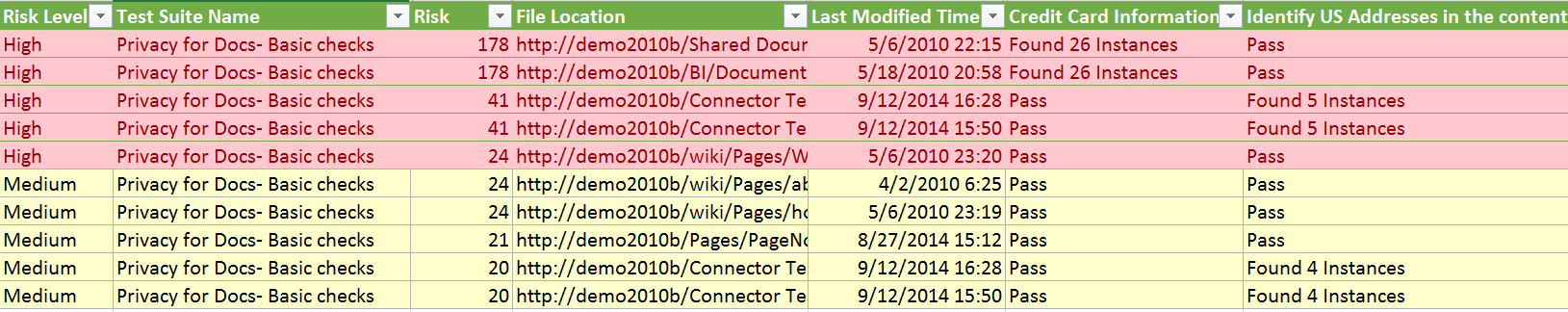
Fundamental to understanding the cost is a picture of your risk score. Most solutions consider just the presence of personal information to a risk, but not all data is created equal. You stand to be fined for each record lost. Compliance Guardian tailors risk scores based on the type, number of times information appears, and location of the data to give you an accurate picture of the key risk indicators for your organization.
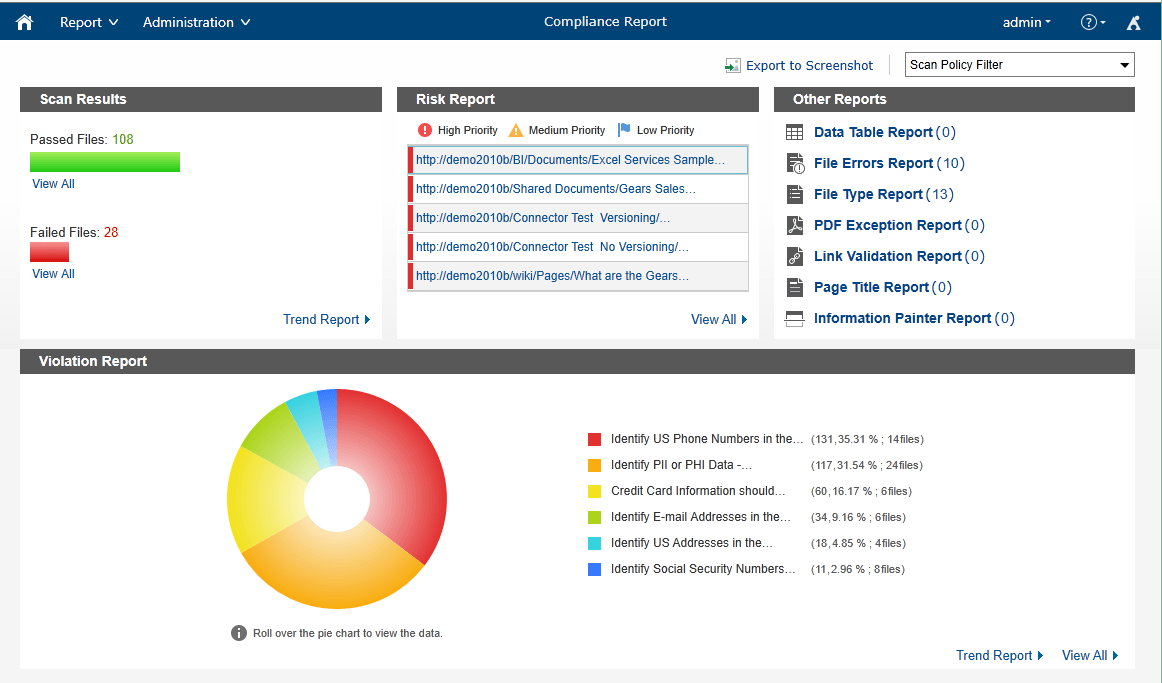
In mitigating this risk through a Compliance Guardian, organizations can also find the dark data where it lives – all across the enterprise. This hits on the critical need for data discovery. Companies can also harness Compliance Guardian to drive enterprise classification and taxonomy across enterprise collaboration, messaging, and social platforms – whether on-premises or cloud-based. Not knowing is never better. Be sure to understand how your business users are managing sensitive data today so that you can properly remediate and educate following a system clean-up.
For organizations to create a truly successful compliance program, they must change their approach altogether – rather than viewing it as an obligation to the legal team, they must see this as a moral obligation to their customers. Failing to follow through with data privacy and risk management is a crime of trust against them and is punishable by loss of trust, loss of revenue, and even loss of the business completely. So in 2015, begin fostering strong, long-term relationships with your customers through reasonable security measures. Your customers and your business will be grateful for years to come.
To learn more about Compliance Guardian, please visit our product page. Want a personalized demonstration to see how it can help your business? Request one for free today!






Great article! I am printing this out to discuss with my team.