Are you concerned about important data leaking when using Microsoft 365? Watch our free webinar “Preventing Data Leaks in Microsoft Teams (and Other Collaboration Systems)” for critical tips.
Read the other post in our Securing Collaboration series below:
- How to Get ISO 27001-Ready
- How to Find Sensitive Content in Office 365
- Sensitive Info Identifiers in Office 365
- 5 Risk Management Challenges in Office 365
- Top 5 Microsoft 365 Security and Compliance Center Features and Tricks
- How to Build a Strong Permissions Management Strategy
- Office 365 Governance in an Always Online World
- When to Upgrade From E3 to E5 for Stronger Microsoft 365 Data Protection
Ever since the cloud adoption trend first started, we’ve seen users concerned about oversharing risks. Recently, as more people work from home, virtual collaboration has become vital for most companies. The adoption of Microsoft Teams—as well as other Microsoft 365 products—increased dramatically to help make remote work more efficient.
However, the dark side of collaboration (a.k.a. oversharing) is often overlooked and poses security and privacy risks to organizations. Let’s explore how the upcoming Insights for Microsoft 365 products can help provide visibility to users and enable secure collaboration.
A Few Challenges
Oversharing, especially when it happens unknowingly, can easily go unnoticed for a long time before it’s too late. This situation can happen in a variety of ways; here are some common real-life scenarios.

Challenge #1: Find misplaced sensitive files in high exposure locations
Imagine you have a large environment with thousands of Teams, SharePoint site collections, and OneDrives. How do you determine which files are high-exposure? (Hint: this could include the places that everyone, external users, or anonymous users have access to).
Now assume that you have the list of all high-exposure files (potentially thousands if not millions of them, as every OneDrive has a “Shared with Everyone” folder plus many collaboration sites). How do you know which files are misplaced according to sensitivity?
Challenge #2: External user governance
Let’s say you have many external users to work with. Do you know the answers for the following questions?
- What are the areas external users have access to?
- Do they have access to potentially sensitive content?
- What did they do?
- How can you make sure no external users can access sites that are meant to be internal-only?
Challenge #3: Shadow Users/Groups
Shadow Users/Groups come about when files in Teams channels are shared from the backend (SharePoint) to other people who are not part of the Team/channel.
How can you identify these shadow users/groups? A bonus question: Which files can they access? Are any of them sensitive?
Challenge #4: Are Teams chat files or email attachments private?
Each user’s OneDrive contains some special folders used by Outlook to store attachments or used by Teams to store P2P chat files. In real life we saw cases where users shared these folders by mistake and caused files from their private Teams chat or email attachments to be visible to everyone.
As most users don’t even know of the existence of these folders, these issues may exist for a long time before eventually being addressed (if at all). With this comes challenge #4: How can you identify this situation with 100,000+ OneDrive files?

Solutions
Microsoft 365 Built-In Functions
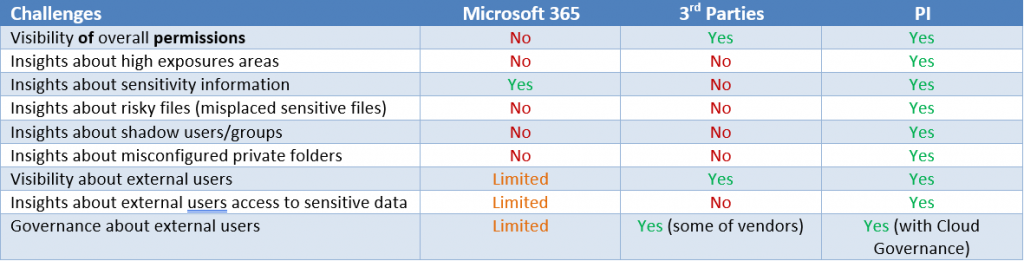
Microsoft 365 out-of-the-box can deliver high-level reports about content sensitivity, but it doesn’t have insights about the permission and exposure factors for files. This makes it very difficult to identify the real risk: misplaced sensitive content.
3rd Party Solutions
There are some 3rd party vendors that can help provide visibility for Microsoft 365 permission settings, but none of them can effectively solve the above challenges.
- There are no insights about exposure. It’s more about the permission settings of a given scope or areas a given user/group can access. The question of “high exposure” stays unresolved.
- There are no insights about sensitivity. In most cases, the majority the high-exposure files are solely for collaboration purposes, and only a very small percentage of them may be misplaced. Without insights about sensitivity, finding these risky files is like finding a needle in a haystack.
- No insights about shadow users/groups or misconfigured private folders. Challenges #3 and #4 are still unresolved.
Policies and Insights (PI)
Insights for Microsoft 365 provide an unique value to the oversharing challenges. It offers visibility from both angles (exposure and sensitivity) to give users a quick and easy full picture to identify when oversharing happens. This includes Exposure Level (taking exposure factors like external users, anonymous links, and even large groups into consideration to identify high exposure areas) and Content Sensitivity (files that contain SSN or credit card information, for example).
The complex logic of identifying shadow users/groups is automatically calculated on the backend with content sensitivity info taken into consideration. With the help of Insights for Microsoft 365, users can quickly identify the risky areas that need attention and possible remediation that would otherwise be daunting to handle via out-of-the-box functions or other 3rd party permission-focused solutions.
AvePoint Cloud Governance helps to streamline the external user lifecycle management process. In addition, Insights for Microsoft 365 can help with other important aspects of external user governance (challenge #2). Furthermore, Policies for Microsoft 365 can help to enforce external user-related settings to enforce governance.
To help illustrate the challenge scoreboard, following is a table to summarize the coverage:
How It Works
Insights for Microsoft 365 work similarly to Policy Enforcer. Since Insights is a new cloud-native product built from the ground-up, we’ll dive more into it here.
Permission Cache
Insights maintain a near real-time cache of all the objects that have unique permission settings within the selected scopes. With the help of this case, many permission-related operations and ad-hoc queries will be much faster without needing to crawl the data source time and again. The cache can be valuable for AvePoint products as well; once the integration is supported, the Cloud Governance permission renewal process and Cloud Management security search will both be much faster.
Exposure Level
With the permission cache it’ll be easier to see where everyone can access the content. This is something the aforementioned 3rd party vendors can provide as well.
However, Insights’ concept of exposure is a step-up from verbatim permissions. High-exposure areas don’t only mean the places that everyone can access, but it also includes the areas that large groups (i.e. AvePoint) or many users/groups can access (a site collection with many users or groups in permission settings, for instance).

Although the concept of exposure level may sound simple, it’s not a simple task to achieve. Many organizations have hundreds or even thousands of groups, and to identify quantities this vast takes some serious computation power. To make it more complex, group membership constantly changes with effects rippling to its parent and grandparent groups. Insights’ backend also performs complex calculations about Shadow Users/Groups and misconfigured private folders (challenge #3 and #4).
Although this extra processing adds more cost to the application, it gives Insights unique advantages over other vendors.
Sensitivity Level
From challenge #1, we can see that just knowing the high exposure files is not enough. Sensitivity is another important layer of insight needed to solve many challenges.
For sensitivity level, Insights leverages Microsoft 365 Sensitive Information Types. This requires another layer of processing on the backend, including both an initial scan and near real-time scans. This is another unique advantage offered by Insights.
Activity Logs
Another dimension to the whole picture is the activity history to help investigations. For example, when some high-risk items are identified, users can see who has accessed the file recently or see the activity of an external user to make sure everything is as expected.

Near Real-time Updates
When using the product for the first time, a few simple configurations are needed to define how to measure exposure levels and sensitivity levels. For most users, using the default rules is probably fine, but users can also customize if necessary. Insights for Microsoft 365’s first scanning will then be started in the backend. Depending on the size of the environment, this process may take a while to complete. Partial data will be available once some workspaces are processed and progressing until the initial scanning is completed. After that, incremental changes to a user’s Microsoft 365 environment will be processed frequently to keep data up to date.
In the end, there’s a lot that Microsoft 365 does to prevent oversharing and make collaboration as secure as possible. As we continue to navigate through these turbulent times, the less we have to worry about sensitive information leaking the better. Working remotely means that a secure cloud is a necessity, and Insights for Microsoft 365 should help achieve just that.
For a bit more on Policies and Insights, check out the video below:


![[WGR] PI Blog Series Headers_2](https://www.avepoint.com/blog/wp-content/uploads/2020/07/WGR-PI-Blog-Series-Headers_2-696x299.png)





