Note: The following is an excerpt from our ebook, “Right-Sizing Microsoft Teams Management and Security.” You can download it right here!
When Was a Team Accessed?
Let’s say you have gotten this far using native Microsoft 365 functionality. You’ve run your permission report, you’ve researched your security groups and nested groups, and you’ve cross-referenced that with a permission report that’s tens of thousands of lines long. Now, you’re finally able to report back to your security teams about who had access to sensitive information in Microsoft 365 and Microsoft Teams.
They might say, “Great, this is really helpful information. It looks like a few external users inadvertently had access to sensitive information against our policy. Can you tell us if they accessed it and when? Also, is this exposure level better or worse than last year’s?”
You let out a long and weary sigh — it looks like your quest isn’t quite over. You covered the who, what, and where. Now it’s time to tackle the when.
Microsoft Insights
To understand what risky activity may be taking place and who has viewed these documents and when, you’ll need to pull audit reports that surface user activity and show you who has access to your content. While these logs are relatively easily to locate in the report section of the Microsoft 365 admin center, keep in mind this is now the third report you’re cross-referencing.
Furthermore, each time you go through this exhaustive process of cross referencing all three reports, it’s still only going to give you a comprehensive snapshot of your sensitive information exposure and its potential risk to your organization. That means that, in order to stay up to date, the process will need to be repeated again and again at a frequency that meets your organizational requirements.
How to Tell Why a Team Exists?
Microsoft 365 allows you to either enable or disable external sharing across the tenant — the same with guest user access. While you do have the option to create specific policies for specific Microsoft Teams, SharePoint sites, and other workspaces, it is a tedious and time-consuming process.
Microsoft Insights
To create appropriate controls for each workspace, some organizations use a controlled Microsoft Teams provisioning process wherein all Microsoft Teams creation requests are sent to IT for approval. However, it’s not that straightforward. For IT to ensure the proper settings are being applied, they need more information:
- Why does this Microsoft Team exist?
- Will it have sensitive data?
- Is it for a project?
- Will it require guest users?
Once again, to gain critical context, IT is forced to go through a time-consuming, manual process — in this case, communicating with the requestor and the business owner. An additional challenge is that once the workspace is provisioned, the Owner of that workspace can change the settings at any time in its lifecycle.
This process can eat into your budget and bandwidth. A survey of IT professionals conducted by the AIIM (Association for Information and Image Management), and commissioned in part by AvePoint, found that 63 percent of respondents spent 4 to 8 hours per week performing routine SharePoint governance tasks such as provisioning, changing permissions, and revising site settings.
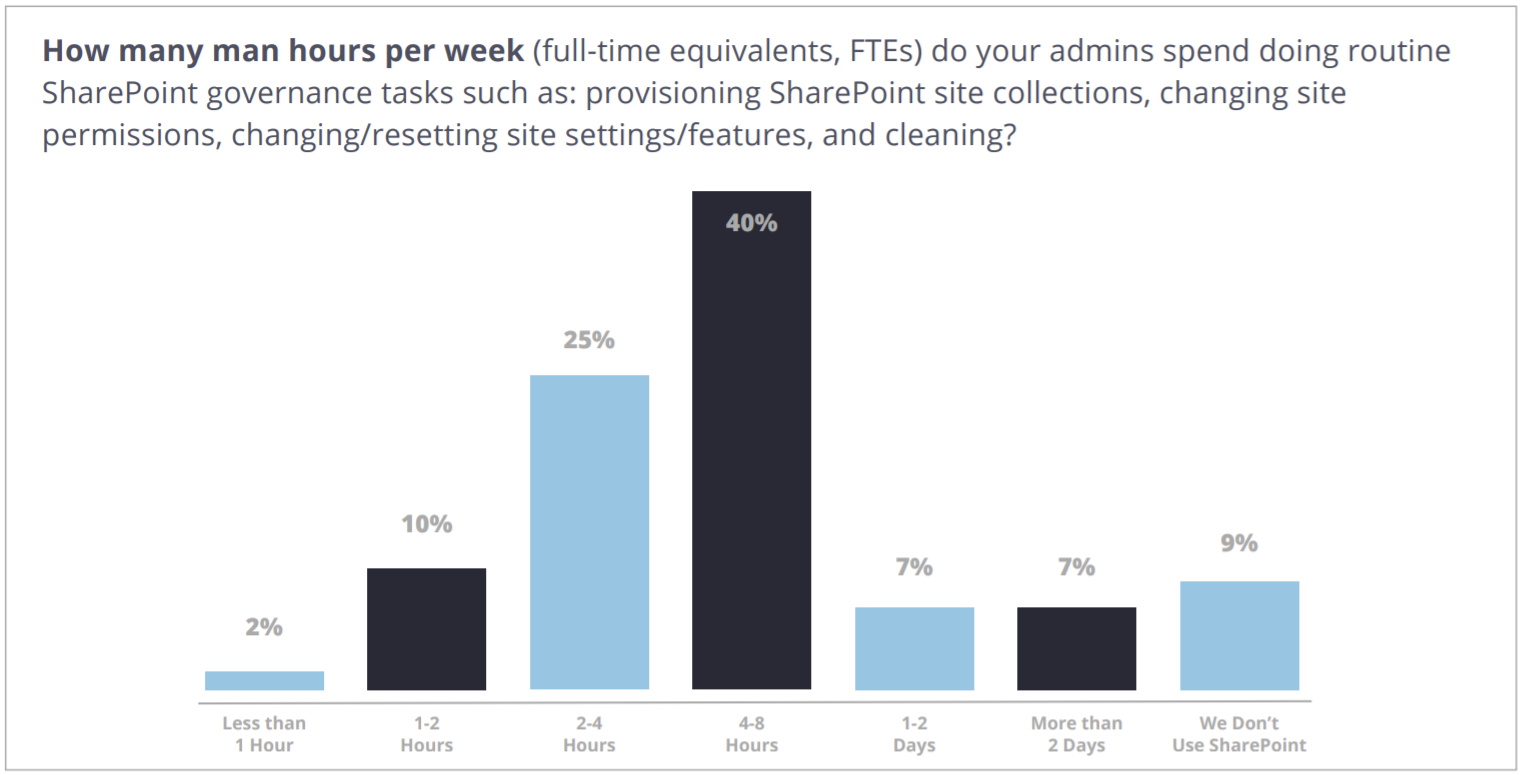
That’s one full workday every week! That time could be better spent on more strategic tasks that add value to the organization.
Have other burning Microsoft Teams governance and security questions you need answered? Download the full ebook here and check out other excerpts below:






