In the past year and a half, two of the buzzwords we’ve all been hearing constantly are “remote work” and “the cloud.” Indeed, this is the new work ecosystem we find ourselves in, and people in industries around the world are seeing it unfold in real-time.
While productivity is still a priority in this new remote work setup, security has become even more crucial and difficult to monitor for admins. The security risks have increased, and relying on identity governance is not enough.
Proper data governance would be critical to ensure sensitive data and the apps that are used to access them like Microsoft Teams–which has now become a hub where employees work and access data–are secure.
But while the combination of strong data and identity governance measures may protect your sensitive data from most of the risks in the cloud, setting up extra security measures like conditional access would benefit your overall security strategy even more.
What is Conditional Access?
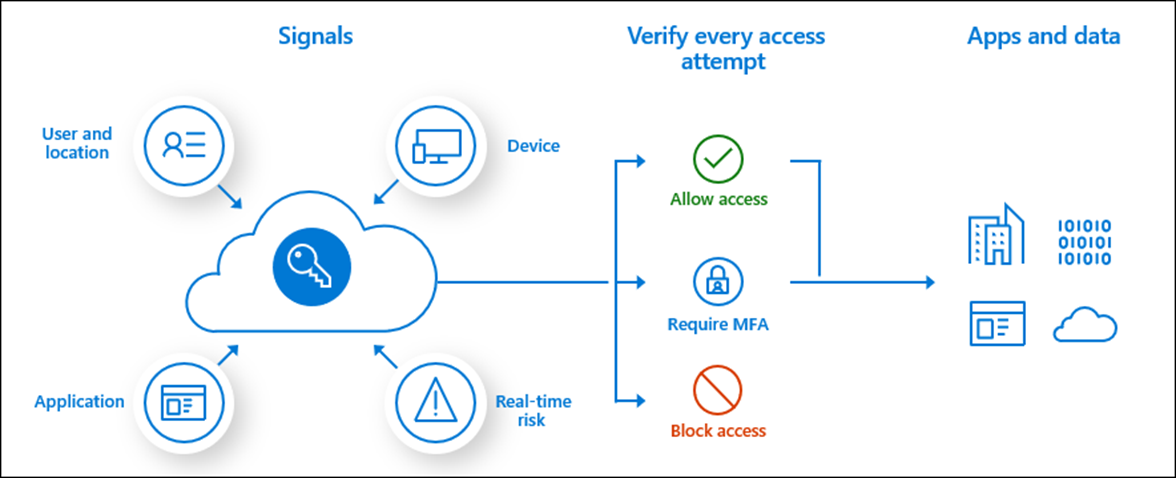
A tool used by Azure Active Directory, conditional access brings signals together to help you enforce organizational policies. It’s used to strengthen defenses against suspicious identities by allowing you to control access to apps based on identity, location, and device.
In the simplest terms, conditional access policies allow you to block or grant access to certain resources and apps depending on whether a user or a device satisfies certain conditions. Below are certain policies commonly used:
- Requires multi-factor authentication
- Requires device to be marked as compliant
- Requires Hybrid Azure AD joined device
- Requires approved client app
- Requires app protection policy (preview)
The Integration of Microsoft Teams with SharePoint and Exchange Online
But while applying conditional access policies sounds easy enough, the integrations between Microsoft 365 apps make things more complex.
Microsoft Teams is supported separately as a cloud app in Azure Active Directory conditional access policies. But as you probably well know, Microsoft Teams is deeply integrated with SharePoint Online and Exchange Online.
This integration makes it hard to enforce consistent policies with transparent result, like when you need to grant access to Teams but access to shared resources from SharePoint must be blocked.
But what you need to understand is that SharePoint Online and Exchange Online are the underlying platforms that support Teams. That means whatever policy you set up in both cloud apps would apply to Teams once a user signs in. In contrast, policies set up in Teams might not reflect on SharePoint Online and Exchange Online.
For example, if you set up multi-factor authentication for SharePoint Online and a user wants to access resources in your SharePoint Online environment through their Microsoft Teams tenant, they will also be subject to the MFA policy.
To Ensure the Targeted Results, Consider Setting Policies on Microsoft 365 Instead
The complexity of these integrations may push you, though unconsciously, to set inconsistent policies across the apps. This will then create gaps where certain resources will be accessed without your consent. To prevent this from happening, setting consistent policies across related apps and services will help solidify your security strategy.
To make this possible, Microsoft recommends using the Microsoft 365 suite to target the services all at once and avoid issues with the cloud apps’ service dependencies. Administrators should assign policies to the Microsoft 365 app to ensure all metadata is protected across apps and their dependencies.

Strengthen Your Conditional Access Policies With Intune
Once you have a consistent policy map planned out, automation will now be key to strengthen your policies without sacrificing productivity in the name of security.
Microsoft Intune can be used and integrated with Azure AD to strengthen your security space. By utilizing Intune, you can automate your policy settings and add additional security measures to your access settings without the heavy burden of constant monitoring to your IT team.
Closing
Microsoft has many security offerings that can help you plan your defense against the risks in the cloud. Understanding how each of them works should help you as an admin prepare better for securing your organization’s security needs.
Mapping out your security strategy also means enhancing what Microsoft offers with third-party tools, like AvePoint’s Cloud Governance, which can help reduce the burden of your IT team and make security much less complex for you as an admin.






