Adoption in Office 365 can often be met with a key hurdle: data protection. Data protection is a prominent issue for organizations today, with pressure being placed on safeguarding sensitive information, intellectual property, customer data, employee data, and other regulated content. Privacy professionals agree that nearly 30 percent of breaches are caused by mishandling of data in core information management systems like Office 365. With the potential impact of fines reaching nearly four percent of overall revenue through the European Union General Data Protection Regulation (GDPR) as well as regulatory fines from many other agencies and government bodies, it is more important than ever that organizations take steps to safeguard their sensitive data.
Regulators, whose job has always been to protect the public from danger, now face another danger: that their own application of old rules to new realities might suppress innovation of tremendous potential value to the public. Office 365 offers major productivity improvement opportunities, but data protection teams – including information security officers, privacy officers, or lawyers – are almost always asking sobering questions around the following key features:
External Sharing in OneDrive for Business: One-click sharing internally or to partners really expedites collaboration!
- Who has access to our sensitive content?
- Who is allowed to share that content externally?
- Who are we allowed to share that content with?
Delve and the Office Graph: We used to lose a lot of time searching for content, finding subject matter exports, or potentially duplicating work!
- Whose content is published to Delve?
- What content is now being pushed forward that used to be hidden by obscurity?
- How do we ensure the right people have access to content before it is exposed to Delve?
Strike a Balance on Controls
 When we look to answer these questions, it’s tempting to let fears dictate our policy:
When we look to answer these questions, it’s tempting to let fears dictate our policy:
- Because someone could see sensitive information, we could simply choose not to go to the cloud!
- Because someone might misuse our sharing capabilities, they should be turned off.
- Because we found a Social Security Number in a file share that one time, we can’t trust our users with what they put in their OneDrive!
The answer to the questions asked by the privacy-minded community may simply be “You’re right, we can’t trust our users!” However, both law and common sense dictates a risk-based approach. Just saying no to business users who are simply looking to do their job in the most efficient way possible often drives them toward other cloud services where you have less control. Office 365 Compliance Center – which houses the native compliance-related features for an Office 365 administrator – is Microsoft’s attempt to deal with these concerns, although it still leaves gaps that organizations will need to address in the cloud.
Delve, which may create concerns about inappropriate access to and sharing of information, can be addressed in a common sense manner. Rather than taking a prohibitive stance across the board, access to the Office Graph can be disabled, blocking Delve controls from a user. Anyone who searches for their board will find only profile information – not a list of documents they may have touched or worked on. For external sharing, rather than blocking all access, you can choose to limit what policies can be used, such as requiring an external user to be authenticated first before accessing data.
AvePoint has worked with Microsoft to detect changes to these policies in Office 365 in our Policy Enforcer in DocAve Administrator to ensure they are followed once you reach an agreement on controls.
Watch for Key Areas of Risk
 In order to begin enforcing the right balance of controls, you have to first identify potential content that might contribute to risk. You’ll want to tag and classify that data, and then apply appropriate location, access, and data loss prevention (DLP) controls to ensure the highest level of protection.
In order to begin enforcing the right balance of controls, you have to first identify potential content that might contribute to risk. You’ll want to tag and classify that data, and then apply appropriate location, access, and data loss prevention (DLP) controls to ensure the highest level of protection.
Identifying the nature of the data you own and regulations that govern that data will help you create a clearer, risk-based strategy for protection. In the US, for instance, you might be looking at SEC, ITAR, EAR, HIPAA, or any number of regulations that directly influence how you handle data, SharePoint and its governance controls. AvePoint Compliance Solution Specialist Marie Penot recently posted an insightful article on the European Union General Data Protection Regulation (GDPR), which serves as a reminder that even if a small portion of your business happens in Europe, you’re still accountable for the data you own!
Microsoft’s new DLP features in Office 365 are primarily designed to help you understand the data you have, albeit with some important limitations. Integrated into the eDiscovery center is the native ability to generate DLP queries based on pre-configured policies that map to common laws and regulations. If you’re interested in understanding what data you have as it pertains to the GDPR, financial regulations, or even HR and payroll data, native abilities can help you get that information.
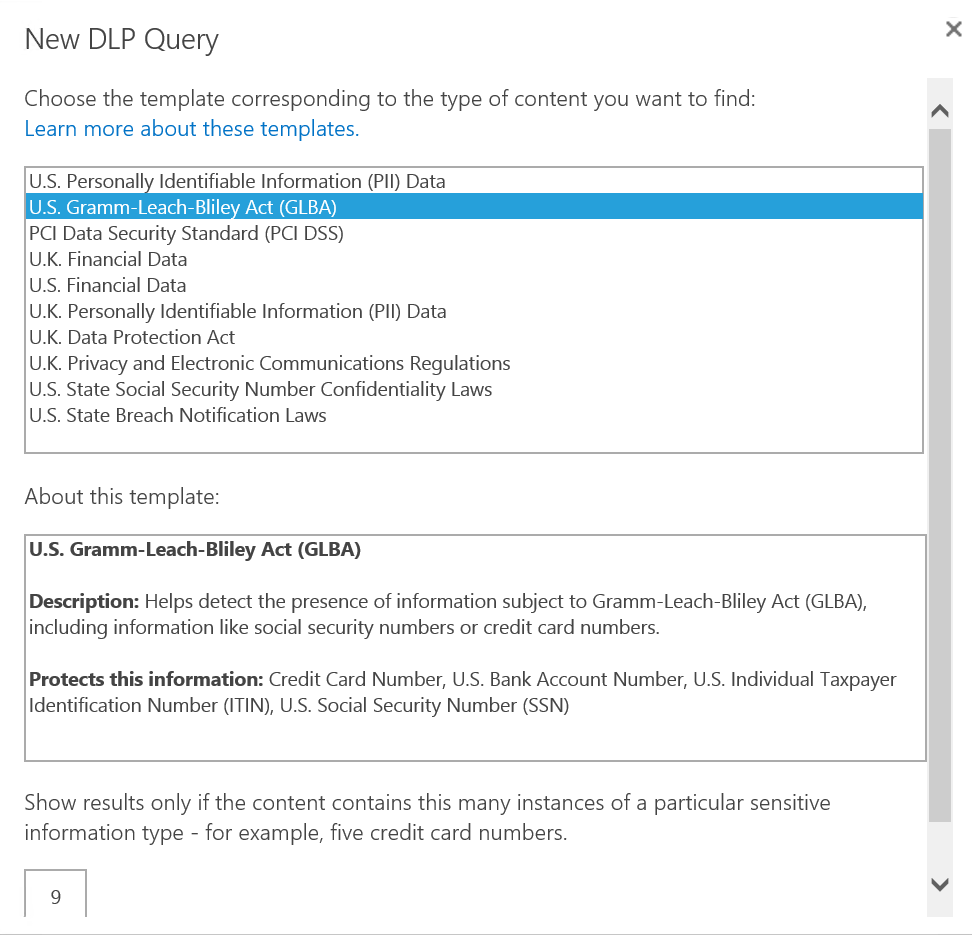
Now you can watch these changes over time to identify potential areas that need to be cleaned up. Keep in mind that the ability to configure, customize, and extend these rules – or even to build your own – based on your organizational needs has limitations in Microsoft’s out-of-the box offering. AvePoint Compliance Guardian provides extended and complementary capabilities to further extend data discovery and protection across Office 365 and beyond.
Provide Guidance when Users Step Out of Bounds

Once you’ve migrated your users over to Office 365 and helped them understand the policies in place, you can fully expect they will test the boundaries they’re given!
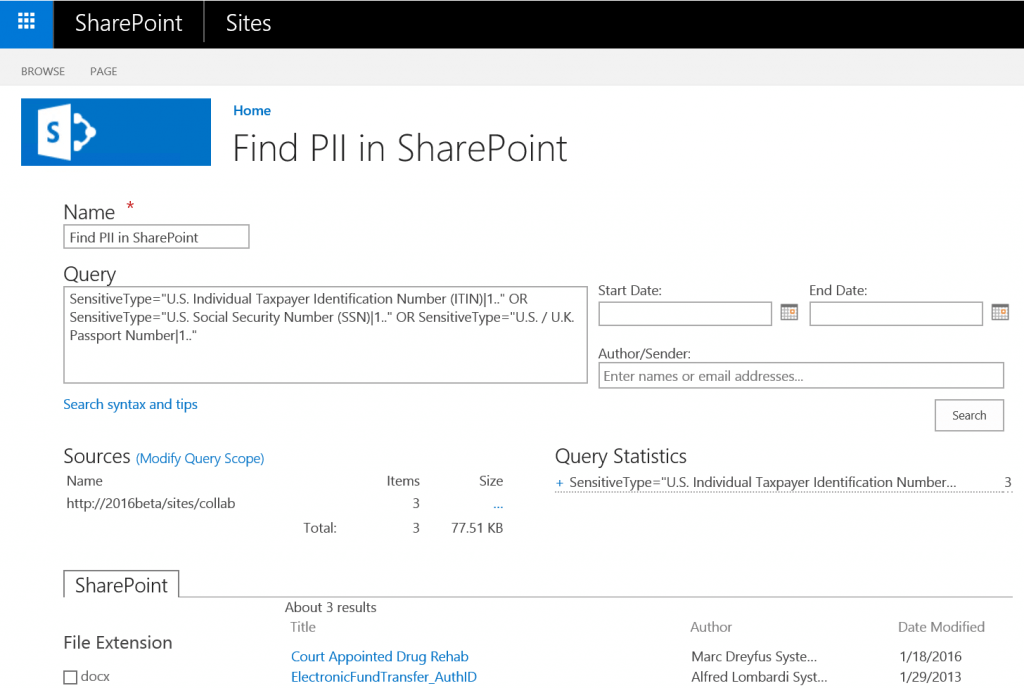
To learn more detail about what you can expect from the Office 365 DLP stack as well as where it falls short, check out this previous blog post I put together. You can see a breakdown of how Office 365 configures policies to detect sensitive information, tracks their occurrence, and takes action once you’ve identified potential violations. We also recently provided a view of the DLP features as they appear in the upcoming on premises release, SharePoint 2016, where the configuration maps closely to what you get in Office 365.
For those of you who are looking for a quick summary – those same policies we used to identify areas of risk can be used to alert users as they are working with content that has been deemed too risky for the environment they’re in. For instance, perhaps you have enabled external sharing for a site and want to block PII from being uploaded to it, as shown below.
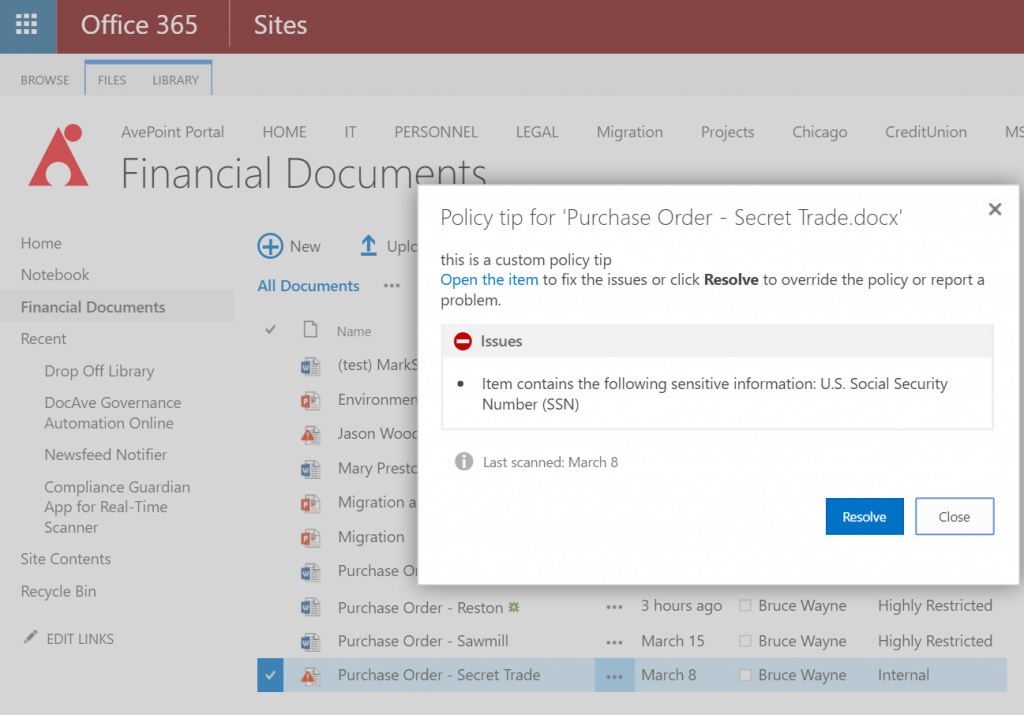
Where Office 365 DLP Capabilities Fall Short, and How to Deal with It
Out of the box, Office 365 DLP gives you the ability to report incidents and generate alerts. You can either provide these through email or consume them through the Office 365 Management Activity API. These can be sent to an incident management team, or a set of librarians for a group of sites (defined in the sensitive data policies when you assign them to sites). The level of detail these emails contain depend on the policies you create. In addition, you can effectively “quarantine” the file to the author and legal teams once the policy has been violated. As discussed in my previous blog post, your ability to take action and provide reports with native capabilities stops there, though.
This is where Microsoft relies on its partner ecosystem and where technologies from AvePoint can provide a more comprehensive solution. For most organizations, simple discovery and alerts are just not enough. While you should empower your end users to do the right thing, you still need the proper systems in place to stop them from accidentally or maliciously leaking information through tagging and classification, quarantining, redacting, encrypting, and blocking sensitive data from ending up in the wrong place.
One of the biggest objections we hear to DLP solutions is that they create excessive false positives and become a true bottleneck to productivity. This is an issue for Office 365 native functionality because of its limited flexibility. A nuanced approach that allows you to fine tune the rules to increase the accuracy of your results as well as take actions, such as content redaction, is an important part of a successful DLP implementation.
It’s also very much worth noting that Office 365 DLP features only work on the platform, and it’s highly unlikely that Office 365 is the only system in which your company is storing potentially sensitive information. AvePoint Compliance Guardian offers a full platform for incident management, remediation, and reporting for Office 365 as well as other systems like file shares, SharePoint Server, Skype for Business, and Yammer. The best security program is one that takes a layered approach and extends across the organization. Accessing a single pane of glass for risk across multiple content sources helps provide a fully balanced ecosystem of trust.
What’s Next?
As you plan your journey to the cloud, be sure to check out AvePoint’s Cloud Arcade for more helpful tips on managing, migrating, and protecting Office 365! You can also learn more about making the right decisions when choosing your cloud, on-premises, or hybrid deployment by watching our on demand webinar, AvePoint’s Cloud Arcade Presents: Mastering the Cloud Game.


